Certificate Configuration
Scenarios
After creating a Certificate Authority (CA) certificate, you can manage its lifecycle, including exporting, enabling, and disabling the certificate.
Exporting a CA Certificate
- Log in to the console.
- In the navigation pane, choose Tenant Configuration > Certificate Configuration.
- In the Operation column of the certificate list, click Export Certificate or click the certificate name. On the CA Certificate tab page, click Export as File.
- Save the exported certificate as prompted.
Exporting a CRL File
- Log in to the console.
- In the navigation pane, choose Tenant Configuration > Certificate Configuration.
- In the certificate list, select the certificate for which the Certificate Revocation List (CRL) configuration is to be exported. The basic certificate information window appears.
- On the CRL Configuration tab page, click Download and save the downloaded CRL file as prompted.
Disabling a CA Certificate
- Log in to the console.
- In the navigation pane, choose Tenant Configuration > Certificate Configuration.
- In the Operation column of the desired certificate, click Disable to go to the Disable Certificate dialog box.
- If you want to perform this operation, enter YES or click Auto Enter.
- Click OK.
Deleting a Certificate
- Log in to the console.
- In the navigation pane, choose Tenant Configuration > Certificate Configuration.
- In the Operation column of the desired certificate, click Delete to go to the Delete Certificate dialog box.
- If you want to perform this operation, enter DELETE or click Auto Enter.
- Click OK.

Only disabled or expired certificates can be deleted.
Replacing a CA Certificate
- Log in to the console.
- In the navigation pane, choose Tenant Configuration > Basic Settings.
- Click Edit under Basic Settings to go to the page for modifying a domain.
- Select the desired certificate from the Private CA certificate drop-down list box.
- Click OK.
Enabling a CA Certificate
- Log in to the console.
- In the navigation pane, choose Tenant Configuration > Certificate Configuration.
- In the certificate list, select a disabled certificate and click Enable in the Operation column to go to the Enable Certificate dialog box.
- If you want to perform this operation, enter YES or click Auto Enter.
- Click OK.
Importing the Root/Subordinate CA Certificate and CRL File to the AD Server
The private root CA certificate, subordinate CA certificate, and CRL configuration file must be published to all trusted root CAs and enterprise NTAuth store of AD CS.

- Import the root or subordinate CA certificate of the corresponding created CA type, and the CRL configuration file, to the AD server.
- If multiple domains are interconnected with and certificate-based identity authentication is enabled for one of the domains, you must import the corresponding CA certificate and CRL to the AD server of the domain.
- Only the CRL can be used to verify the certificate revocation status.
- Log in to the AD server using the account and password.
- Export the root or subordinate CA certificate and the CRL, and copy them to the AD server. For details, see Exporting a CA Certificate and Exporting a CRL File.
- Press Win+R, enter cmd in the displayed Run dialog box, and press Enter to open the CLI.
- Go to the root CA certificate directory and run the following command:
Example: cd D:\Users\file (file is the directory where the root CA certificate is)
- Run the following commands in the CLI to import the root or subordinate CA certificate:
- For root CA:
- Add the certificate to the enterprise NTAuth store:
- Add the certificate to the trusted root CA:
- Add the CRL to the AD server:
certutil -addstore root rootca.crl

Replace rootca.cer and rootca.crl with the CA certificate name and CRL file name exported from the console.
If there are multiple AD servers, repeat the preceding operations or apply the configuration to each AD server through the group policy. Procedure:

- View the Thumbprint field of the certificate: Double-click the root CA certificate or subordinate CA certificate and CRL file created in Creating a CA certificate, and view the Thumbprint field on the Details tab page. The value of Thumbprint varies with files, as shown in the following figure.

- The default update period of the domain controller group policy is 5 minutes. It takes about 5 minutes to apply the update to all domain controllers.
- On the taskbar in the lower left corner of the AD server logged in to in 1, click
 .
. - On the right of the Start menu, click to open Server Manager.
- In the upper right corner of the Server Manager page, choose Tools > Group Policy Management.
- On the Group Policy Management page, choose Forest > Domains > Group Policy Objects.
- Right-click Default Domain Controllers Policy and choose Edit from the shortcut menu.
- On the Group Policy Management Editor page, choose Computer Configuration > Preferences > Windows Settings > Registry.
- Right-click Registry and choose New > Registry Item from the shortcut menu.
- On the New Registry Properties page, select the registry path HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\EnterpriseCertificates\NTAuth\Certificates\.
- Click the value of the Thumbprint field of the rootca.cer certificate, select Blob, and click Select, as shown in the following figure.
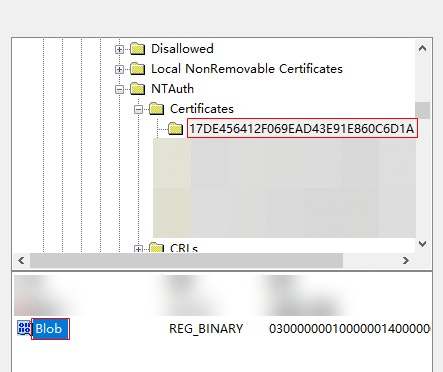
- Click OK.
- Right-click Registry and choose New > Registry Item from the shortcut menu.
- On the New Registry Properties page, select the registry path HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\ROOT\Certificates\.
- Click the value of the Thumbprint field of the rootca.cer certificate, select Blob, and click Select, as shown in the following figure.
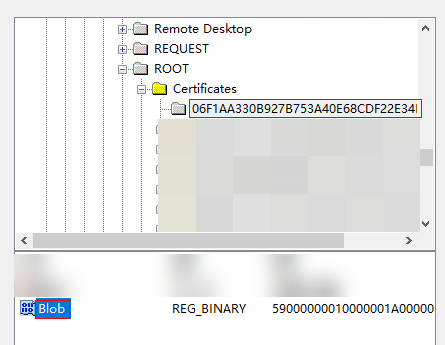
- Right-click Registry and choose New > Registry Item from the shortcut menu.
- On the New Registry Properties page, select the registry path HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\ROOT\CRLs\.
- Click the value of the Thumbprint field of the rootca.crl certificate, select Blob, and click Select, as shown in the following figure.
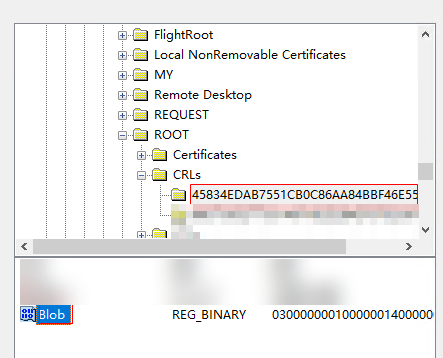
- For subordinate CA:
- Add the certificate to the enterprise NTAuth store:
- Add the certificate to the trusted root CA:
- (Optional) Add the root CA's CRL to the AD server:
certutil -addstore root rootca.crl

If the CRL of the root CA is valid for a long time, you are advised to import the CRL to the AD server (by running the preceding command) and import the CRL again before it expires. Otherwise, ensure that the AD domain server can access the CRL of the root CA.
- Add the certificate to the intermediate CA:
- Add the subordinate CA's CRL to the AD server:
If there are multiple AD servers, repeat the preceding operations or apply the configuration to each AD server through the group policy. Procedure:

- To view the value of the Thumbprint field of the certificate, double-click the root or subordinate CA certificate created in Creating a CA certificate, click the Details tab, and view the fingerprint key string, as shown in the following figure.

- The default update period of the domain controller group policy is 5 minutes. It takes about 5 minutes to apply the update to all domain controllers.
- On the taskbar in the lower left corner of the AD server logged in to in 1, click
 .
. - On the right of the Start menu, click to open Server Manager.
- In the upper right corner of the Server Manager page, choose Tools > Group Policy Management.
- On the Group Policy Management page, choose Forest > Domains > Group Policy Objects.
- Right-click Default Domain Controllers Policy and choose Edit from the shortcut menu.
- On the Group Policy Management Editor page, choose Computer Configuration > Preferences > Windows Settings > Registry.
- Right-click Registry and choose New > Registry Item from the shortcut menu.
- On the New Registry Properties page, select the registry path HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\EnterpriseCertificates\NTAuth\Certificates\.
- Click the value of the Thumbprint field of the subca.cer certificate, select Blob, and click Select, as shown in the following figure.

- Click OK.
- Right-click Registry and choose New > Registry Item from the shortcut menu.
- On the New Registry Properties page, select the registry path HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\ROOT\Certificates\.
- Click the value of the Thumbprint field of the rootca.cer certificate, select Blob, and click Select, as shown in the following figure.
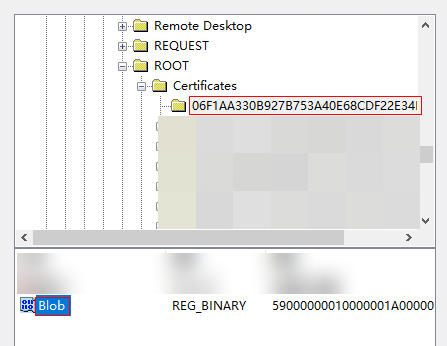
- Right-click Registry and choose New > Registry Item from the shortcut menu.
- On the New Registry Properties page, select the registry path HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\CA\Certificates\.
- Click the value of the Thumbprint field of the subca.cer certificate, select Blob, and click Select, as shown in the following figure.

- Right-click Registry and choose New > Registry Item from the shortcut menu.
- On the New Registry Properties page, select the registry path HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\CA\CRLs\.
- Click the value of the Thumbprint field of the subca.cer certificate, select Blob, and click Select, as shown in the following figure.

- Right-click Registry and choose New > Registry Item from the shortcut menu.
- On the New Registry Properties page, select the registry path HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\ROOT\CRLs\.
- Click the value of the Thumbprint field of the rootca.crl certificate, select Blob, and click Select, as shown in the following figure.

Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot





