Workspace Permissions
Related Concepts
IAM can be used free of charge on Huawei Cloud. You pay only for the resources in your account. For details about IAM, see IAM Service Overview.
Account
An account registered upon your first use of Huawei Cloud. You can use this account to pay the bill, access all Huawei Cloud resources and services under the account, and to reset user passwords and grant user permissions. You can use your account to receive and pay all bills generated by your IAM users' use of resources.
You cannot modify or delete your account in IAM, but you can do so in My Account.
IAM user
You can use your account to create IAM users and assign permissions for specific resources. Each IAM user has their own identity credentials (password or access keys) and uses cloud resources based on the assigned permissions. IAM users cannot make payments themselves. You can use your account to pay their bills.
User group
You can use user groups to assign permissions to IAM users. IAM users must be added to a user group to obtain the permissions required for accessing specified resources or cloud services under the account. If you add a user to multiple user groups, the user inherits the permissions that are assigned to all the groups.
The default user group admin has all the permissions for using all of the cloud resources. Users in this group can perform operations on all resources, including but not limited to creating user groups and users, assigning permissions, and managing resources.
Examples
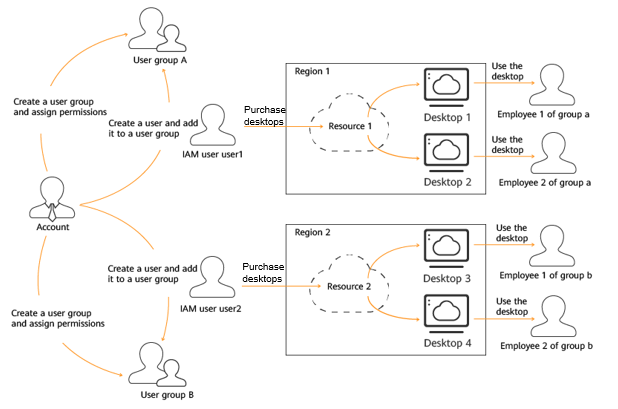
For example, you want to isolate permissions of employees in groups a and b. That is, employees in group a use Workspace resources in region 1, and employees in group b use Workspace resources in region 2.
- You can create user groups A and B and grant permissions to them. That is, assign the administrator permissions of Workspace in region 1 to user group A, and assign the administrator permissions of Workspace in region 2 to user group B.
- Create two IAM users user1 and user2, and add user1 to user group A and user2 to user group B. IAM user user1 has the administrator permissions of Workspace in region 1, and IAM user user2 has the administrator permissions of Workspace in region 2.
- The administrator of group a can use the account of user1 to log in to Huawei Cloud and go to the Workspace console of the project in region 1 to purchase desktops for the employees of group a and manage the desktops of the project in region 1. The administrator of group b can use the account of user2 to log in to Huawei Cloud and go to the Workspace console of the project in region 2 to purchase desktops for the employees of group b and manage the desktops of the project in region 2. Figure 1 shows the operation process. For details about how to create an IAM user, see Creating an IAM User and Assigning Permissions.
Workspace Administrator Permissions
You can grant users permissions by using roles and policies. Workspace grants administrator permissions to IAM users by using roles.
By default, new IAM users do not have permissions assigned. You need to add a user to one or more groups, and grant Workspace administrator permissions to these groups. Users inherit permissions from their groups. After authorization, IAM users can perform operations on Workspace resources in the corresponding projects.
Table 1 lists all system-defined permissions of Workspace. The Dependency column indicates roles on which a Workspace permission depends to take effect. Workspace roles are dependent on the roles of other services because Huawei Cloud services interact with each other. Therefore, when assigning Workspace permissions to a user group, do not deselect other dependent permissions. Otherwise, Workspace permissions do not take effect.
|
System-defined Permission |
Description |
Details |
|---|---|---|
|
Workspace FullAccess |
All permissions on Workspace |
All permissions on Workspace |
|
Workspace DesktopsManager |
Desktop administrator permissions on Workspace |
Creating, deleting, and performing operations on a desktop or desktop pool; desktop-related operations, including Internet access, scheduled tasks, App Center, and image management |
|
Workspace UserManager |
User administrator permissions on Workspace |
User management operations, such as creating users, deleting users, and resetting passwords |
|
Workspace SecurityManager |
Security administrator permissions on Workspace |
All security-related operations, such as policy management and checking user connection records |
|
Workspace TenantManager |
Tenant administrator permissions on Workspace |
All tenant configuration functions |
|
Workspace ReadOnlyAccess |
Read-only permissions on Workspace |
Read-only permissions on Workspace |
Table 2 lists the permissions to be added for the following operations.

For details about the permissions required for Workspace, see Assigning Permissions to an IAM User or Creating a Custom Policy.
|
Operation |
Dependent System-defined Role, Policy, or Custom Policy |
Description |
|---|---|---|
|
BSS-related permissions: Perform yearly/monthly operations, such as purchasing and changing desktops, and switching from pay-per-use to yearly/monthly billing. |
The policy must contain the following action permissions: bss:discount:view bss:order:update bss:order:view bss:order:pay bss:renewal:view |
Select either the system-defined role or the custom policy. |
|
IAM-related permissions: Perform scheduled tasks, perform operations on desktop pools, and create and query agencies. |
Permissions required for creating and querying agencies: The policy must contain the following action permissions: iam:roles:getRole iam:roles:listRoles iam:agencies:getAgency iam:agencies:listAgencies iam:agencies:createAgency iam:permissions:listRolesForAgencyOnProject iam:permissions:grantRoleToAgencyOnProject Permissions required for querying agencies: The policy must contain the following action permissions: iam:agencies:getAgency iam:agencies:listAgencies iam:permissions:listRolesForAgencyOnProject |
When creating an agency, select either the system-defined role Security Administrator or the custom policy. When querying agencies, select either the system-defined policy IAM ReadOnlyAccess or the custom policy. |
|
TMS-related permissions: Query predefined tags during desktop creation. |
The policy must contain the following action permissions: tms:predefineTags:list |
Select either the system-defined policy or the custom policy. |
|
VPCEP-related permissions: Enable or disable Direct Connect access (required for fine-grained authentication of enterprise projects). |
System-defined role: VPCEndpoint Administrator |
VPCEP does not support fine-grained authentication of enterprise projects. |
|
VPC-related permissions: Perform desktop-related operations and enable economical Internet access (required for fine-grained authentication of enterprise projects). |
IAM project-level permissions System-defined policy: VPC ReadOnlyAccess System-defined role: VPC Administrator |
You must have the VPC permission of the enterprise project where the VPC used for enabling Workspace is. |
|
IMS-related permissions: Create an image (required for fine-grained authentication of enterprise projects). |
The policy must contain the following action permissions: ims:images:get ims:images:share |
IMS does not support fine-grained authentication of enterprise projects. |
Once granted permissions on the IAM console, users can perform the following actions (starting, shutting down, and restarting a desktop) only using northbound interfaces (NBIs). They are still not allowed to perform these operations on the Workspace console.

Permissions must be granted on actions of startup, shutdown, and restart on the Workspace console:
Permission: performing operations on a desktop
API: POST/v2/{project_id}/desktops/action
Action: workspace:desktops:operate
|
Permission |
API |
Action |
|---|---|---|
|
Starting a desktop |
POST /v2/{project_id}/desktops/start |
workspace:desktops:start |
|
Shutting down a desktop |
POST /v2/{project_id}/desktops/stop |
workspace:desktops:stop |
|
Restarting a desktop |
POST /v2/{project_id}/desktops/reboot |
workspace:desktops:reboot |
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot