Resolving Findings
You can take some measures to resolve findings. After a finding is resolved, its status changes from Active to Resolved.
Resolving External Access Findings
If you find any unintended access, you can modify the policy to modify or remove the permissions. For example, for unintended share access permissions on OBS buckets, go to the OBS console to configure the permissions on the bucket.
After you modify a policy, IAM Access Analyzer scans the resource again. If the resource is no longer shared outside your zone of trust, the status of the finding is changed from Active to Resolved. You can view the finding in the resolved finding list. If the changes you made resulted in the resource being shared outside your zone of trust, IAM Access Analyzer generates a new active finding.

- When IAM Access Analyzer is not able to analyze a resource, it cannot generate a finding.
- Resolved findings will be deleted 90 days after the last update to the findings.
- Log in to the new IAM console.
- In the navigation pane, choose Access Analyzer > External Access.
- In the upper left corner of the displayed page, select a target analyzer from the drop-down list.
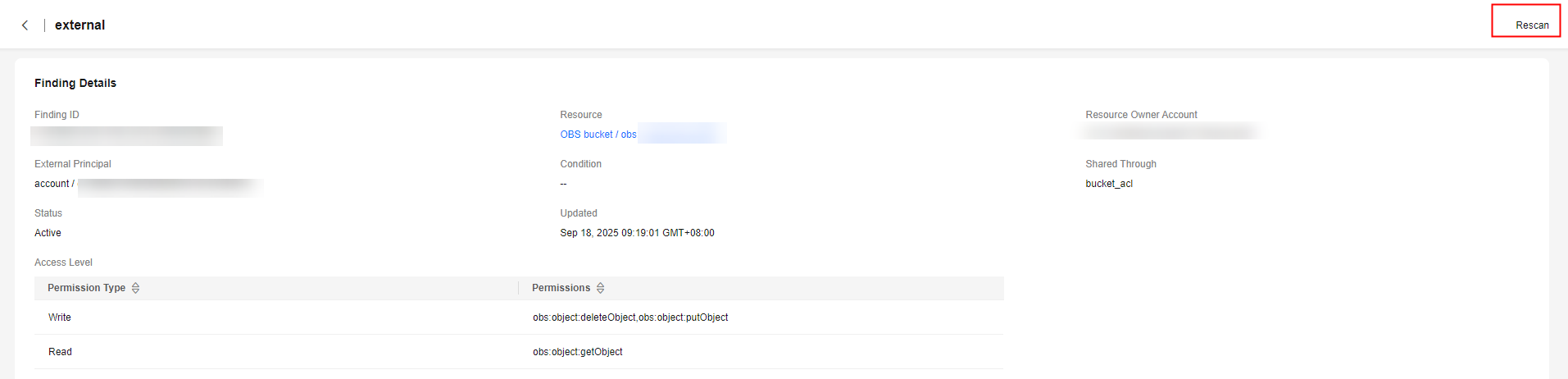
- In the finding list, click the ID of the target finding to view its details. If you find any unintended access, you can modify the policy to remove the permissions that allow the unintended access.
- In the Access Not Intended area, click Go to IAM Console, Go to OBS Console, Go to DEW Console, Go to SWR Console, Go to CBR Console, or Go to IMS Console to modify corresponding policies.
Figure 1 Modifying a policy

- Go back to the finding details page and click Rescan in the upper right corner. The analyzer will analyze the policy again.
Figure 2 Rescanning policies
Resolving Unused Access Findings
When an unused access analyzer scans an entity in your zone of trust, if the access keys, passwords, or policies are not used for more than the specified number of days specified in the tracking period when you create an unused access analyzer, new findings will be generated for access.
For an unintended unused access finding, you need to delete the unused access keys, agencies, trust agencies, passwords, or policies on the IAM console. For an intended unused access finding, you can archive it and view the finding in the archived finding list.
- For details about how to delete access keys, see Managing Access Keys for an IAM User.
- For details about how to delete agencies and trust agencies, see Deleting or Modifying an Agency (by a Delegated Party).
- For details about how to delete the password of an IAM user, see Changing the Password of an IAM User.
- For details about how to delete policies, see Modifying or Deleting a Custom Identity Policy.
After you delete unused access keys, agencies, trust agencies, passwords, or policies. The access analyzer rescans the resource, and the finding changes from Active to Resolved. You can view the finding in the resolved finding list.
Resolving Best Practice Compliance Findings
If a finding indicates that a configuration does not comply with security best practices, you need to modify the configurations according to the analysis. For example, if account test does not have an MFA device, add one for the account on the IAM console. The finding changes from Active to Resolved after the analyzer scans the resources again. You can view the finding in the resolved finding list.
- Log in to the new IAM console.
- In the navigation pane, choose Access Analyzer > Best Practice Compliance.
- In the upper left corner of the displayed page, select a target analyzer from the drop-down list.
- In the finding list, click the ID of the target finding to view its details.
- In the Unintended Access area, click Add MFA Device, Delete Access Keys of User Root, Enable Login Protection, Remove High-Risk Permissions from Agency, or Remove High-Risk Permissions from User.
Figure 3 Modify configurations

- Go back to the finding details page and click Rescan in the upper right corner. The analyzer will analyze the policy again.
Figure 4 Rescanning

Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot





