Viewing and Downloading Sensitive Data Identification Results
After a sensitive data identification task is complete, you can view the result on the result details page. You can also download the generated identification result to your local PC. This section explains how to view and download the identification result.
Prerequisites
At least one sensitive data identification task has been executed. For details about how to create a sensitive data identification task, see Creating an Identification Task.
View the sensitive data identification result.
- Log in to the DSC console.
- Click
 in the upper left corner of the management console and select a region or project.
in the upper left corner of the management console and select a region or project. - In the navigation pane on the left, choose Sensitive Data Identification > Identification Task.
- Click Identification Result in the Operation column of the target task. The result details page is displayed.
- DSC collects statistics on the total number of sensitive information records, risk level distribution, and top 10 matched rules.
Additionally, DSC provides a detailed identification results list for scanned objects. You can click the filter box in the upper-left corner of the list and select filter criteria to filter sensitive data identification results.
- In the row containing the desired scan object, click View Classification and Grading Result Details in the Operation column. The Classification and Grading Result Details dialog box is displayed. View the result details and sample data.
- On the Result Details tab, click Add Rule in the upper left corner of the result details list. In the Add Rule dialog box, select a new rule from the New rule drop-down list and click OK. A message is displayed, indicating that the rule is added successfully.
- Click Replace in the Operation column. In the dialog box that is displayed, select a new rule from the New rule drop-down list to replace the rule in the identification result. Click OK. A message is displayed, indicating that the original rule has been replaced with the new rule.
- Click Remove in the Operation column to delete unnecessary rules.
- On the Sample Data tab, view Data Content, NLP Optimization, and Rule.
- The Categorization and leveling result details page displays the identification object details, result details, and sample data.
- The Result Details area displays the number of hits/hit rate, matching rules, grading results, classification results, and classification and grading templates.
- Click the Sample Data tab to view the sample data that matches the rule. Currently, sample data of the big data and LTS types cannot be viewed.
Downloading the Identification Result
- Log in to the DSC console.
- Click
 in the upper left corner of the management console and select a region or project.
in the upper left corner of the management console and select a region or project. - In the navigation pane on the left, choose Sensitive Data Identification > Identification Task.
- Click Identification Result in the Operation column of the target task. The result details page is displayed.
- Click Generate Result File in the upper left corner. The Generate Result File dialog box is displayed.
- Identification task: Name of the scan task.
- Object Type: Scan object type. You can click the drop-down list in the upper left corner of the result details page to filter the types of scanned objects to be exported.
- Scan Object: Scan object. You can select the scan objects to be exported from the drop-down list in the upper left corner of the result details page.
- Export Target Bucket: Select a bucket for storing the identification result from the drop-down list box. If no bucket is available in the drop-down list box, create a bucket by referring to Creating an OBS Bucket. The scan-results folder is created in the root directory of the bucket to store the identification result.
- Sample data masking: The sample data masking function is applicable only to assets that support sample data viewing, such as databases and OBS. If sample data masking is not enabled, the identification result sample data will be exported in plaintext. Download the data and delete it in a timely manner.
The identification result list supports filtering.
OBS storage occupies certain storage space, which may incur fees. For details, see OBS Billing Overview.
Figure 1 Confirming the generation of the result file
- Select OK to initiate the generation of the sensitive data scan report for the selected asset. A notification will appear in the upper right corner confirming the successful export of the identification result file. Subsequently, the status of the result file will be updated to Queuing or Running.
- The status of the generated result file is as follows:
- Running: The result report is being generated.
- Queuing: The generated task is queuing.
- If the Download Identification Result from OBS button is dimmed and the message "No file available. Please generate a file first." is displayed, click Generate Result File and download it again.
Result files from various subtasks within the same identification task will replace one another upon generation.
- The status of the generated result file is as follows:
- Click Download Identification Result from OBS. In the displayed dialog box, view the file path and other information. Click OK to go to the OBS Buckets page. Find the corresponding bucket based on the bucket name in the File Path, click the bucket name to go to the bucket, and select the identification result file, click Download in the Operation column to download the identification result file to the local PC.
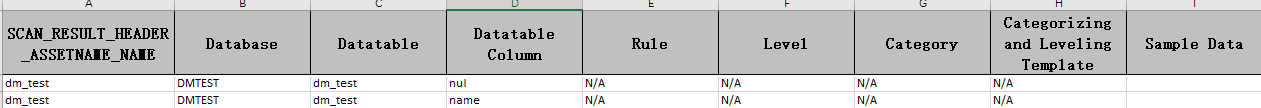
- On the identification result report Excel file, identification results are displayed on the Asset Name and Asset Type sheets. The key fields include Rule, Level, Category, and Classification and Grading Template.
Figure 2 Example of the identification result report
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot





