Creación de un usuario y concesión de permisos de TaurusDB
En esta sección se describe cómo utilizar IAM para un control detallado de los permisos sobre los recursos de TaurusDB. Con IAM, usted puede:
- Crear usuarios de IAM para empleados en función de la estructura organizativa de su empresa. Cada usuario de IAM tendrá sus propias credenciales de seguridad para acceder a los recursos de TaurusDB.
- Otorgar únicamente los permisos necesarios para que los usuarios realicen tareas específicas.
- Confiar una cuenta de servicio en la nube para realizar tareas de O&M eficientes en sus recursos de TaurusDB.
Si su cuenta no requiere usuarios individuales de IAM, omita esta sección.
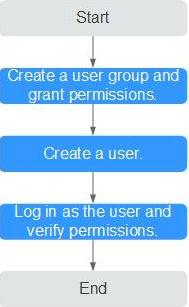
En Figura 1 se describe el procedimiento para otorgar permisos.
Requisitos previos
Obtenga información acerca de los permisos (véase permisos definidos por el sistema) admitidos por TaurusDB y elija roles o políticas según sus requisitos. Para conocer los permisos de otros servicios, véase Permisos definidos por el sistema.
- Cree un grupo de usuarios y asígnele permisos.
Cree un grupo de usuarios en la consola de IAM y adjunte la política de GaussDB FullAccess al grupo.
Para utilizar algunas funciones de otros servicios, se deben configurar los permisos del GaussDB FullAccess y los permisos de los servicios correspondientes. Por ejemplo, cuando se utiliza DAS para conectarse a una instancia de base de datos, debe configurar los permisos de GaussDB FullAccess y de DAS FullAccess.
- Cree un usuario de IAM.
Cree un usuario en la consola de IAM y agregue el usuario al grupo creado en 1.
- Inicie sesión y verifique los permisos.
Inicie sesión en la consola de TaurusDB con el usuario creado y compruebe que el usuario solo tiene permisos de lectura para TaurusDB.
Seleccione Service List > TaurusDB y haga clic en Buy DB Instance. Si puede comprar una instancia, la política de permisos requerida ya se ha aplicado.