Configuring TLS for a LoadBalancer Service
TLS can be used if ultra-high performance and large-scale TLS offloading are required. You can use TLS to forward encrypted TCP requests from clients for a Service.

Service TLS relies on ELB. Before enabling TLS on a Service, check whether TLS is supported in the current region.
Prerequisites
- A Kubernetes cluster is available and the cluster version meets the following requirements:
- v1.23: v1.23.14-r0 or later
- v1.25: v1.25.9-r0 or later
- v1.27: v1.27.6-r0 or later
- v1.28: v1.28.4-r0 or later
- Other clusters of later versions
- To create a cluster using commands, ensure kubectl is used. For details, see Accessing a Cluster Using kubectl.
Notes and Constraints
When TLS is used, sticky session is not allowed.
Creating a LoadBalancer Service and Configuring TLS
- Log in to the CCE console and click the cluster name to access the cluster console.
- In the navigation pane, choose Services & Ingresses. In the upper right corner, click Create Service.
- Configure Service parameters. In this example, only mandatory parameters required for using TLS are listed. For details about how to configure other parameters, see Using the CCE Console.
- Service Name: Specify a Service name, which can be the same as the workload name.
- Service Type: Select LoadBalancer.
- Selector: Add a label and click Confirm. The Service will use this label to select pods. You can also click Reference Workload Label to use the label of an existing workload. In the dialog box that is displayed, select a workload and click OK.
- Load Balancer: Select a load balancer type and creation mode.
- In this example, only dedicated load balancers are supported, and the type of the load balancer must be Network (TCP/UDP/TLS) or Network (TCP/UDP/TLS) & Application (HTTP/HTTPS). Otherwise, TLS cannot be enabled on the listener port.
- This section uses an existing load balancer as an example. For details about the parameters for automatically creating a load balancer, see Table 1.
- Port
- Protocol: Select TCP. If you select UDP, TLS will be unavailable.
- Service Port: the port used by the Service. The port ranges from 1 to 65535.
- Container Port: the port that the workload listens on. For example, Nginx uses port 80 by default.
- Frontend Protocol: In this example, select TLS for the Service. For a dedicated load balancer, to use TLS, the type of the load balancer must be Network (TCP/UDP/TLS).
- Listener
- SSL Authentication: Select this option if HTTPS/TLS is enabled on the listener port. This parameter is available only in clusters of v1.23.14-r0, v1.25.9-r0, v1.27.6-r0, v1.28.4-r0, or later versions.
- One-way authentication: Only the backend server is authenticated. If you also need to authenticate the identity of the client, select two-way authentication.
- Two-way authentication: Both the clients and the load balancer authenticate each other. This ensures only authenticated clients can access the load balancer. No additional backend server configuration is required if you select this option.
- CA Certificate: If SSL Authentication is set to Two-way authentication, add a CA certificate to authenticate the client. A CA certificate is issued by a certificate authority (CA) and used to verify the certificate issuer. If two-way authentication is required, connections can be established only when the client provides a certificate issued by a specific CA.
- Server Certificate: Select a server certificate. If no certificate is available, create one on the ELB console. For details, see Adding a Certificate.
- ProxyProtocol: transfers the source IP addresses of clients to backend servers.

Ensure the backend servers support ProxyProtocol. Otherwise, services may be interrupted.
- Security Policy: If TLS is enabled on the listener port, you can select a security policy. This parameter is available only in clusters of v1.23.14-r0, v1.25.9-r0, v1.27.6-r0, v1.28.4-r0, or later versions.
- Backend Protocol: If TLS is enabled on the listener port, TCP or TLS can be used to access the backend server. The default value is TCP. This parameter is available only in clusters of v1.23.14-r0, v1.25.9-r0, v1.27.6-r0, v1.28.4-r0, or later versions.
- SSL Authentication: Select this option if HTTPS/TLS is enabled on the listener port. This parameter is available only in clusters of v1.23.14-r0, v1.25.9-r0, v1.27.6-r0, v1.28.4-r0, or later versions.
Figure 1 Configuring TLS
- Click OK.
apiVersion: v1
kind: Service
metadata:
name: test-tls
labels:
app: nginx
namespace: default
annotations:
kubernetes.io/elb.class: performance # Load balancer type, which can only be performance (dedicated load balancer) supported by a TLS listener
kubernetes.io/elb.id: 35cb350b-23e6-4551-ac77-10d5298f5204 # ID of an existing load balancer
kubernetes.io/elb.protocol-port: tls:443 # Port on which TLS is to be enabled
kubernetes.io/elb.cert-id: 98e91cb03dea418582a438a212b461d5 # TLS server certificate
kubernetes.io/elb.tls-certificate-ids: e59934f5bc7044f58693de79f1cb4b6d # TLS SNI certificate
kubernetes.io/elb.client-ca-cert-id: 5b5178323a2f4eddbafed065945d9069 # Client CA certificate in TLS two-way authentication
kubernetes.io/elb.proxy-protocol-enable: 'true' # ProxyProtocol for transferring the IP addresses of clients to backend servers
kubernetes.io/elb.security-pool-protocol: 'on' # Backend security protocol. If this function is enabled, the backend protocol is TLS. Otherwise, the backend protocol is TCP.
kubernetes.io/elb.security-policy-id: 175318e0-b6cb-44c5-80a2-0dc372f20df5 # ID of the custom security policy, whose priority is higher than that of the preset security policy
kubernetes.io/elb.tls-ciphers-policy: tls-1-2-fs # Preset security policy
spec:
selector:
app: nginx
externalTrafficPolicy: Cluster
ports:
- name: cce-service-0
targetPort: 80
nodePort: 0
port: 443
protocol: TCP
type: LoadBalancer
loadBalancerIP: **.**.**.**
|
Parameter |
Type |
Description |
|---|---|---|
|
kubernetes.io/elb.protocol-port |
String |
If a Service is TLS/HTTP/HTTPS-compliant, configure the protocol and port number in the format of "protocol:port". where,
For example, to create a TLS listener, the Service protocol must be tls and the Service port must be 443. Therefore, the parameter value is tls:443. |
|
kubernetes.io/elb.cert-id |
String |
ID of an ELB certificate, which is used as the TLS/HTTPS server certificate. To obtain the certificate, log in to the CCE console, choose Service List > Networking > Elastic Load Balance, and click Certificates in the navigation pane. In the load balancer list, copy the ID under the target certificate name. |
|
kubernetes.io/elb.tls-certificate-ids |
String |
In ELB, the IDs of SNI certificates that must contain a domain name are separated by commas (,). To change an ID, remove the SNI certificate by specifying an empty string "". To obtain the certificate, log in to the CCE console, choose Service List > Networking > Elastic Load Balance, and click Certificates in the navigation pane. In the load balancer list, copy the ID under the target certificate name. |
|
kubernetes.io/elb.client-ca-cert-id |
String |
ID of an ELB CA certificate. A CA certificate is issued by a certificate authority (CA) and used to verify the certificate issuer. If TLS/HTTPS two-way authentication is required, TLS/HTTPS connections can be established only when the client provides a certificate issued by a specific CA. To change an ID, remove the CA certificate by specifying an empty string "". To obtain the certificate, log in to the CCE console, choose Service List > Networking > Elastic Load Balance, click Certificates in the navigation pane, and filter CA certificates. In the load balancer list, copy the ID under the target certificate name. |
|
kubernetes.io/elb.security-pool-protocol |
String |
If the frontend protocol of a listener is TLS or HTTPS, you can enable the backend security protocol TLS or HTTPS. The backend security protocol of an existing listener cannot be changed. The modification takes effect only on new listeners that are created by changing the protocol or port.
|
|
kubernetes.io/elb.security-policy-id |
String |
ID of a custom security policy, whose priority is higher than that of a preset security policy. To change an ID, remove the policy by specifying an empty string "". To obtain a security policy, log in to the CCE console, choose Service List > Networking > Elastic Load Balance > TLS Security Policies, and click the Custom Security Policies tab. In the security policy list, copy the ID under the target policy. |
|
kubernetes.io/elb.tls-ciphers-policy |
String |
Preset security policy, which is tls-1-0 by default. To obtain a security policy, log in to the CCE console, choose Service List > Networking > Elastic Load Balance > TLS Security Policies, and click the Default Security Policies tab. In the security policy list, copy the name of the target policy. |
|
kubernetes.io/elb.proxy-protocol-enable |
String |
ProxyProtocol is enabled, which is available only when the frontend protocol is TLS. ProxyProtocol can be used to transfer the IP addresses of clients to backend servers.
NOTE:
Ensure the backend servers support ProxyProtocol. Otherwise, services may be interrupted. |
Verifying Configuration
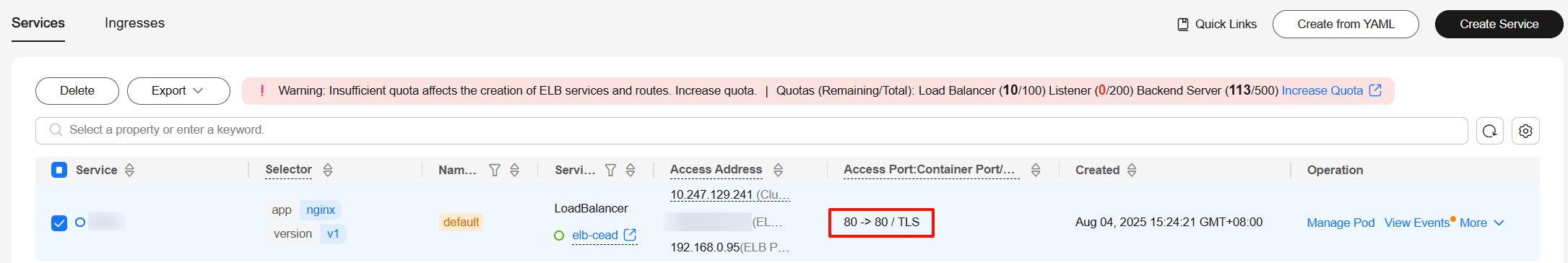
- Log in to the CCE console and click the cluster name to access the cluster console.
- In the navigation pane, choose Services. Locate the row that contains the created Service. The access protocol of the port should be TLS.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot





