Step 5: Test Dedicated WAF Instances
To ensure that WAF can forward your website requests normally, test WAF locally after you add a website to WAF.
Prerequisites
You have performed operations in Step 1: Add a Website to WAF (Dedicated Mode) to Step 4: Whitelist Back-to-Source IP Addresses of Dedicated WAF Instances.
(Optional) Testing a Dedicated WAF Instance
- Create an ECS that is in the same VPC as the dedicated WAF instance for sending requests.
- Send requests to the dedicated WAF through the ECS created in 1.
- Forwarding test
curl -kv -H "Host: {protection object added to WAF}"{Client protocol in server configuration}://{IP address of the dedicated WAF instance}:{protection port}For example:
curl -kv -H "Host: a.example.com" http://192.168.0.1
If the response code is 200, the request has been forwarded. If the request failed to be forwarded, rectify the fault by referring to How Do I Troubleshoot 404/502/504 Errors?
- Attack blocking test
- Ensure that the block mode for basic web protection has been enabled in the policy used for the protected website.
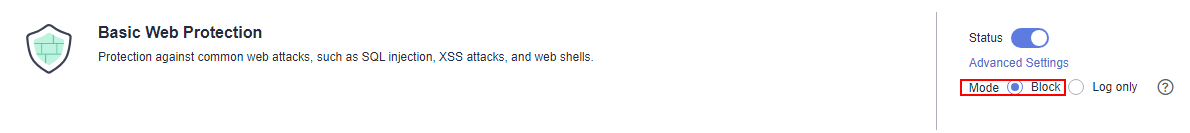
- Run the following command:
curl -kv -H "Host: {protection object added to WAF}"{Client protocol in server configuration}://{IP address of the dedicated WAF instance}:{protection port}--data "id=1 and 1='1"Example:curl -kv -H "Host: a.example.com" http:// 192.168.X.X --data "id=1 and 1='1"
If the response code is 418, the request has been blocked, indicating that the dedicated WAF works properly.
- Ensure that the block mode for basic web protection has been enabled in the policy used for the protected website.
- Forwarding test
Testing the Dedicated WAF Instance and Dedicated ELB Load Balancer
- Forwarding test
curl -kv -H "Host: { protection object added to WAF}"{ELB external protocol}://{Private IP address bound to the load balancer}:{ELB listening port}If an EIP is bound to the load balancer, any publicly accessible servers can be used for testing.
curl -kv -H "Host: {Protected object added to WAF}" {ELB external protocol}://{EIP bound to the load balancer}:{ELB listening port}Example:
curl -kv -H "Host: a.example.com" http://192.168.X.Y curl -kv -H "Host: a.example.com" http://100.10.X.X
If the response code is 200, the request has been forwarded.
If the dedicated WAF instance works but the request fails to be forwarded, check the load balancer settings first. If the load balancer health check result is unhealthy, disable health check and perform the preceding operations again.
- Attack blocking test
- Ensure that the block mode for basic web protection has been enabled in the policy used for the protected website.

- Run the following command:
curl -kv -H "Host: { protection object added to WAF}"{ELB external protocol}://{Private IP address bound to the load balancer}:{ELB listening port}--data "id=1 and 1='1"If an EIP has been bound to the load balancer, any publicly accessible servers can be used for testing.
curl -kv -H "Host: { protection object added to WAF}"{ELB external protocol}://{EIP bound to the load balancer}:{ELB listening port}--data "id=1 and 1='1"Example:
curl -kv -H "Host: a.example.com" http:// 192.168.0.2 --data "id=1 and 1='1" curl -kv -H "Host: a.example.com" http:// 100.10.X.X --data "id=1 and 1='1"
If the response code is 418, the request has been blocked, indicating that both dedicated WAF instance and ELB load balancer work properly.
- Ensure that the block mode for basic web protection has been enabled in the policy used for the protected website.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot








