SSE-C
SSE-C is recommended if you want to store and manage keys by yourself.
Billing
You are not billed for using SSE-C. However, requests for configuring SSE-C for objects will incur costs.
Important Notes
- Requests for SSE-C must be sent over HTTPS to enhance the security of your keys. OBS denies SSE-C-related requests that are not sent over HTTPS.
- OBS does not store your keys. If you lose your keys, you may lose the objects encrypted with them.
- The ETag value of an encrypted object is the MD5 value of the ciphertext, rather than that of the plaintext.
- You need to keep track of which key goes with which object or object version, since each version may be encrypted using a different key.
- You are advised to take necessary measures to protect your keys on the client, such as key rotation, to ensure data security.
Constraints
- SSE-C only supports the AES-256 algorithm.
- SSE-C can be configured for objects only.
- When uploading an object using multipart upload, you must include the key in the requests for initiating the multipart upload, uploading parts, and copying parts. All operations within the same multipart upload must use the same key. The key is not required for completing the multipart upload. The complete object is encrypted using SSE-C.
How SSE-C Works
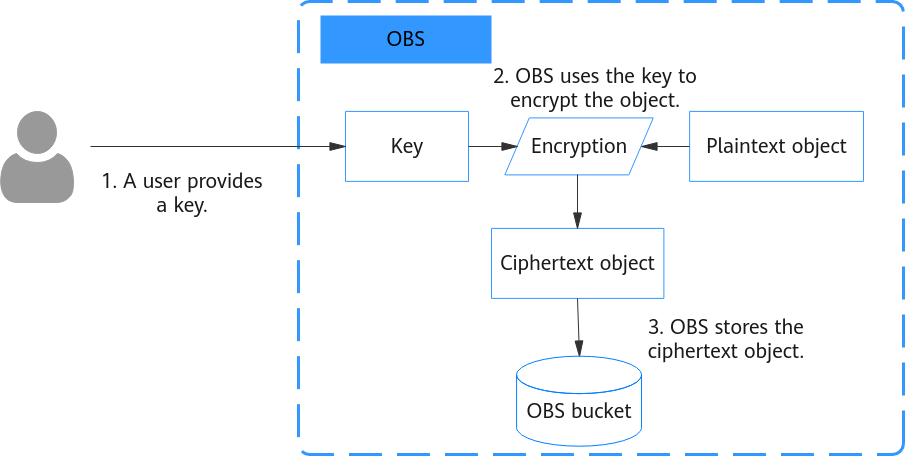
Figure 1 shows how SSE-C encryption works:
- A user sends the key to OBS when making an API call.
- OBS uses the key to encrypt the object and then deletes the key from memory.
- OBS stores the encrypted object.
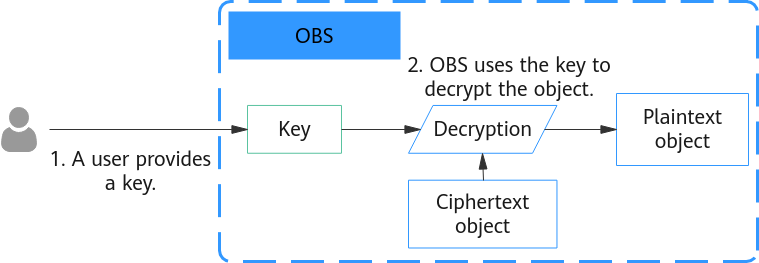
Figure 2 shows how SSE-C decryption works:
- When downloading an object, a user sends the key to OBS when making an API call.
- OBS uses the key to decrypt the object, obtains the plaintext object, and then deletes the key from memory.
Permissions Configuration
- To set a bucket's encryption method to SSE-C, you must be the bucket owner or have the required permissions (obs:bucket:PutEncryptionConfiguration and obs:bucket:GetEncryptionConfiguration in IAM or PutEncryptionConfiguration and GetEncryptionConfiguration in a bucket policy). For details, see OBS Permissions Control Overview, IAM Custom Policies, and Creating a Custom Bucket Policy.
- To use SSE-C to encrypt the object you are uploading, you must have the upload permission (obs:object:PutObject in IAM or PutObject in a bucket policy).
- To download objects encrypted using SSE-C, you must have the download permission (obs:object:GetObject in IAM or GetObject in a bucket policy).
- You can configure a bucket policy to enforce a specific server-side encryption method for objects uploaded to that bucket. For example, to ensure that objects uploaded to bucket ExampleBucket via PUT are encrypted using SSE-C, you can configure a bucket policy that denies any upload requests lacking the x-obs-server-side-encryption-customer-algorithm:"AES256" header:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16
{ "Statement": [ { "Sid": "DenyUnEncryptedObjectUploads", "Effect": "Deny", "Principal": "*", "Action": "PutObject", "Resource": "ExampleBucket/*", "Condition": { "StringNotEquals": { "x-obs-server-side-encryption-customer-algorithm": "AES256" } } } ] }
Configuring SSE-C for an Object
You can use APIs or SDKs to configure SSE-C for an object.
Related Operations
By copying an existing object to itself, you can apply encryption or change its encryption method. For details, see Changing the Encryption Status of an Existing Object.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot