Help Center/
Host Security Service/
User Guide/
Risk Management/
Container Image Security/
Local Image Security Scan/
Viewing and Handling Local Image Scan Results
Updated on 2025-12-12 GMT+08:00
Viewing and Handling Local Image Scan Results
Scenarios
HSS can present image security statistics in the risk view and image view, helping you comprehensively learn, locate, and fix image risks.
- Risk view: View all the scan results of a risk. Local image risks include system vulnerabilities, application vulnerabilities, and common weak passwords.
- Image view: View the scan results of a single image. Local image scan results include system vulnerabilities, application vulnerabilities, software information, and common weak passwords.
You can view and handle local image scan results in Risk View or Image View.
Viewing and Handling Local Scan Results in the Risk View
- Log in to the HSS console.
- Click
 in the upper left corner and select a region or project.
in the upper left corner and select a region or project. - In the navigation pane on the left, choose Risk Management > Container Images.
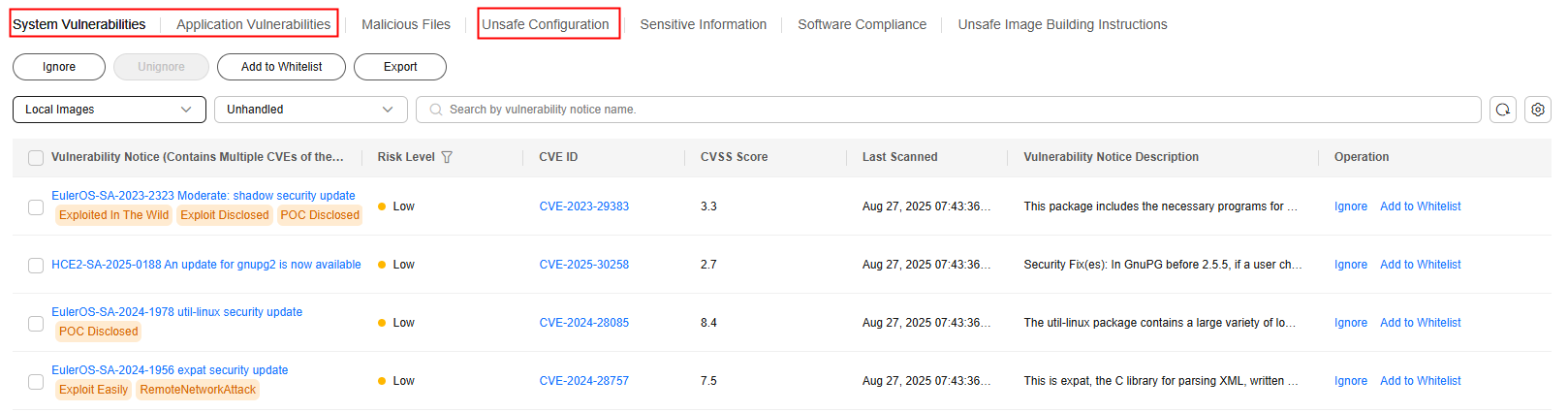
- In Risk View, click Unsafe Configuration > Common Weak Passwords, System Vulnerabilities or Application Vulnerabilities. Filter Local images, and view and handle the scan results. For details, see Table 1.
Figure 1 Local image risk view
Viewing and Handling Local Scan Results in the Image View
- Log in to the HSS console.
- Click
 in the upper left corner and select a region or project.
in the upper left corner and select a region or project. - In the navigation pane on the left, choose Risk Management > Container Images.
- Click the Image View tab.
Figure 2 Image view
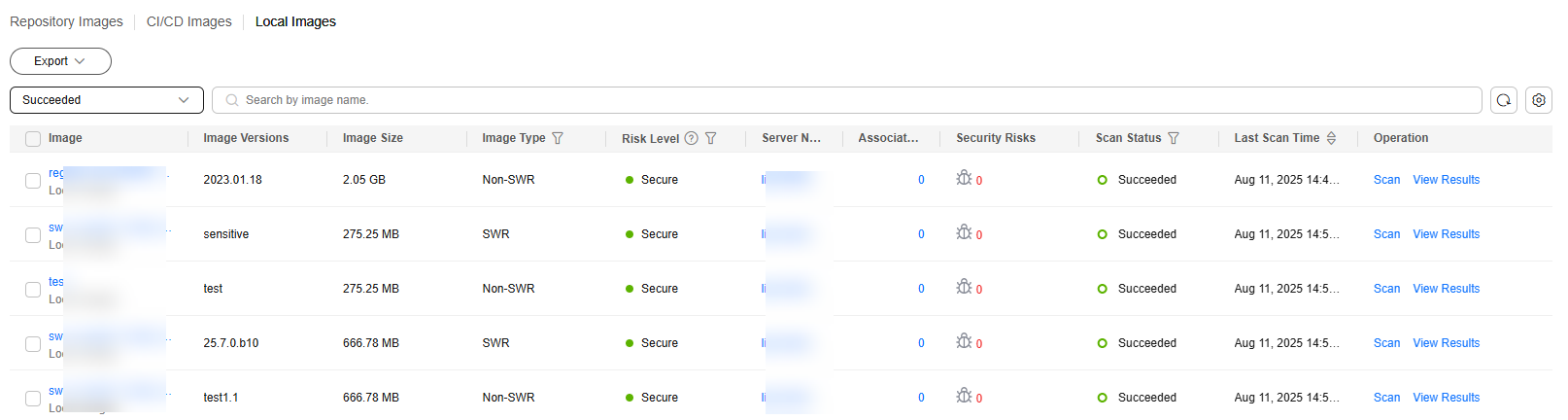
- Click the Local Images tab.
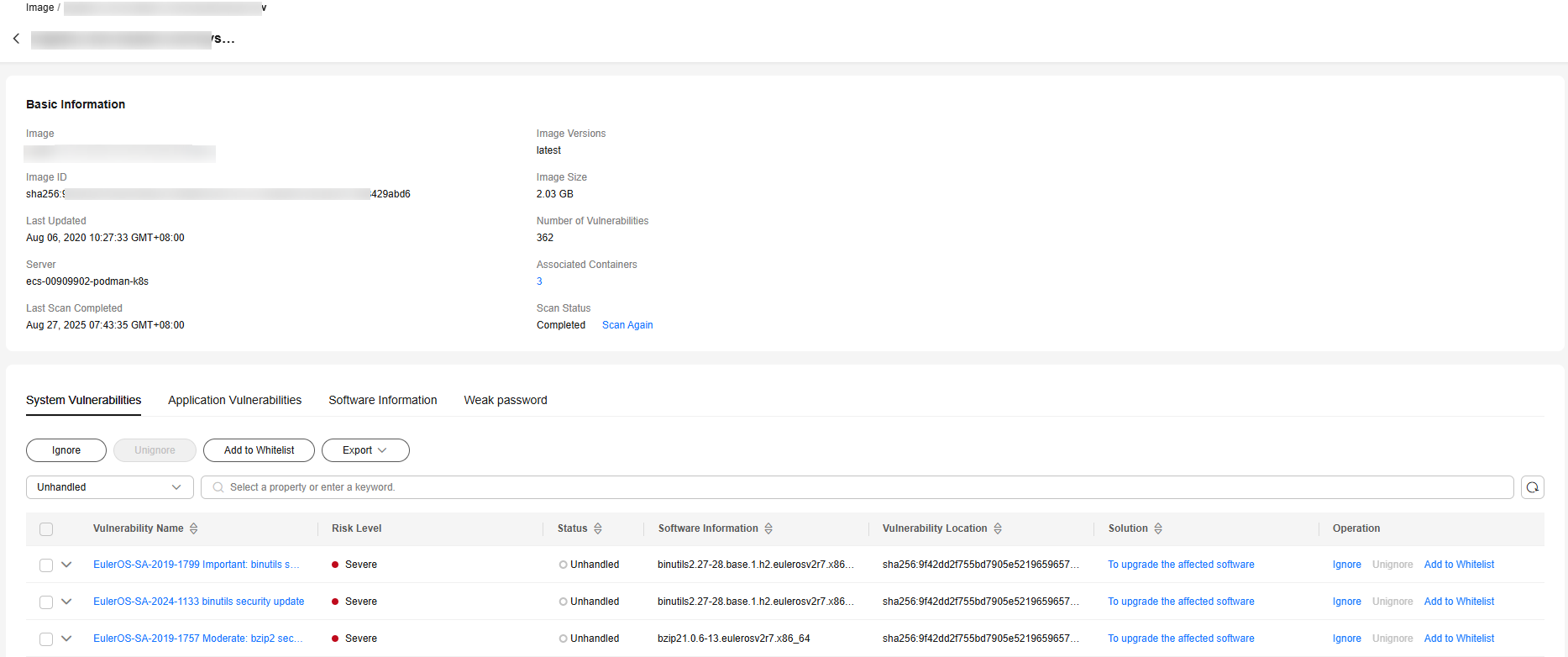
- In the Operation column of an image, click View Results to go to the image details page.
- View and handle risk scan results. For details, see Table 2.
Figure 3 Local image scan details
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
The system is busy. Please try again later.
For any further questions, feel free to contact us through the chatbot.
Chatbot






