Configuring an Encryption Task
- If you are familiar with the database table structure, add it on the Encryption Task Management page. After encryption is configured, unauthorized users can view only the ciphertext when querying the database information.
- If you are not familiar with sensitive data distribution, you can use the Sensitive Data Discovery function to scan your database, create an encryption task in the result, and encrypt database tables. For details, see Creating an Encryption Task in the Result.
Prerequisites
Before configuring the encryption task, you are advised to perform a simulation encryption test to check whether any problem occurs during the process. Rectify the fault. For details, see Simulated Encryption Test.
Procedure
- Log in to a database encryption and access control instance as the sysadmin user.
- In the navigation tree on the left, choose Data Encryption > Encryption Task Management.
- Click Add Encryption Task in the upper right corner.
- In the displayed dialog box, set encryption information. For details about the related parameters, see Table 1.
Table 1 Adding an encrypted task Parameter
Description
Data Source Name
Name of an asset.
Schema
Name of the schema of the asset.
Table
Table name of an asset.
Encryption Algorithm
Select an encryption algorithm from the drop-down list box.
You can view the supported algorithm types on the Checking the Encryption Algorithm page.
Verification Algorithm
Select a verification algorithm from the drop-down list.
The verification algorithm is used to verify the integrity of important data. You can view the supported algorithm types on the Checking the Encryption Algorithm page.
Batch Size
Set the amount of data processed of each batch in the encryption task.
Number of Threads
Number of threads occupied by the encryption task.
Start Task
If this parameter is selected, the task is automatically started after being created.
Figure 1 Adding an encrypted task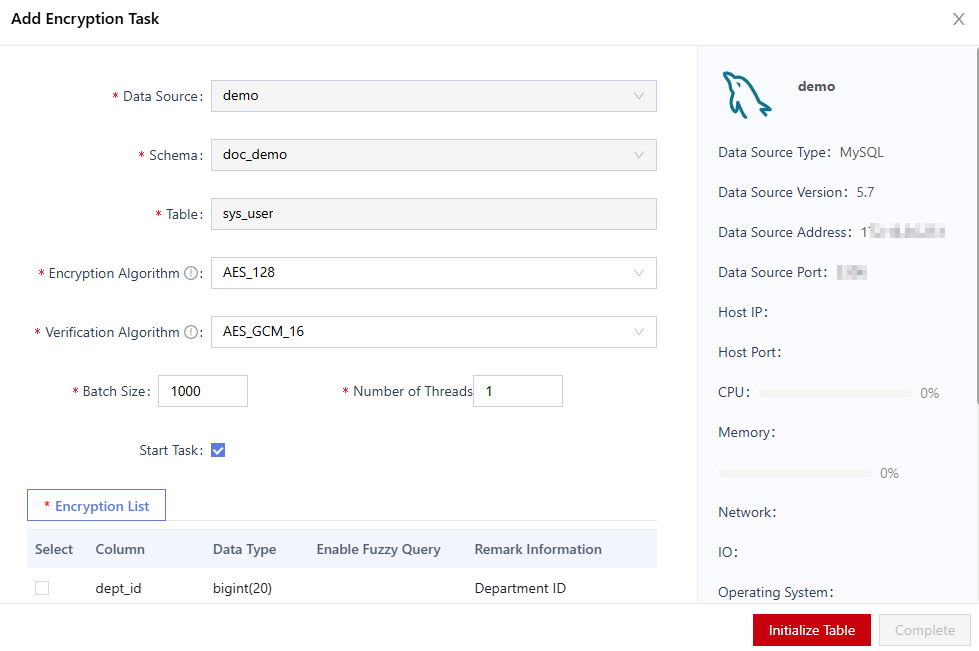
- Click the Encryption List tab, select columns to be encrypted, and set whether to enable fuzzy search.
Figure 2 Selecting encrypted column
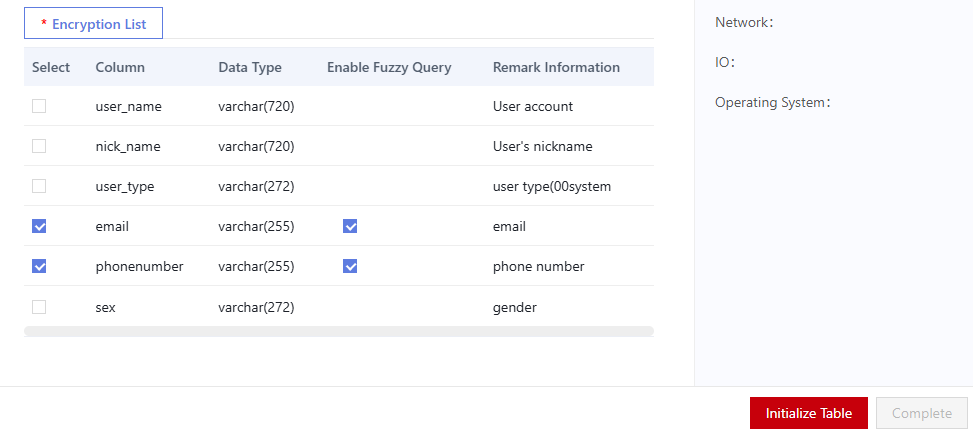 After encryption, fuzzy search cannot be performed by default. In the following cases, you can select Enable Fuzzy Query to perform fuzzy search, which supports % and _ characters.
After encryption, fuzzy search cannot be performed by default. In the following cases, you can select Enable Fuzzy Query to perform fuzzy search, which supports % and _ characters.- The ciphertext is encoded in hexadecimal format and does not support BASE64 encoding. For details, see Setting Encryption Parameters.
- The field is of the string type, for example, varchar and text. Other types are not supported.
- Click Initialize Table to initialize the data table.
- Click Complete.
- If Start Task is not selected during the configuration, click
 to start encryption.
to start encryption.
If the encryption is interrupted, you can click
 to continue the encryption.
to continue the encryption.
Operation Result
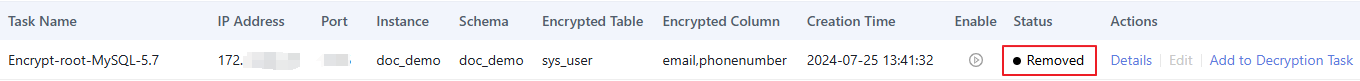
- After the encryption task is created, you can view and manage it in the list. The encryption task is automatically removed after inventory data is encrypted. In this case, the task is in the Removed state, but the system continues to encrypt data.
Figure 3 Encryption task
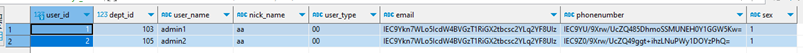
- After the encryption is complete, only encrypted data can be queried by unauthorized users.
Figure 4 Encrypted data
Related Operations
In the task list, you can manage encrypted tasks.
- Click Details to view Encryption Task State, Task Name, Encrypted Table, Encrypted Column, and Encryption Algorithm.
- Click Edit to modify information such as Encrypted Column.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot





