Suggestions on RDS for MySQL Metric Alarm Configurations
You can set alarm rules on Cloud Eye to customize the monitored objects and notification policies and keep track of the instance status. This topic describes how to configure RDS for MySQL metric alarm rules.
Creating a Metric Alarm Rule
- Log in to the management console.
- Click
 in the upper left corner and select a region and a project.
in the upper left corner and select a region and a project. - Click Service List. Under Management & Governance, click Cloud Eye.
- In the navigation pane, choose Alarm Management > Alarm Rules.
- Click Create Alarm Rule in the upper right corner.
- On the displayed page, configure required parameters.
Figure 1 Configuring alarm rule information
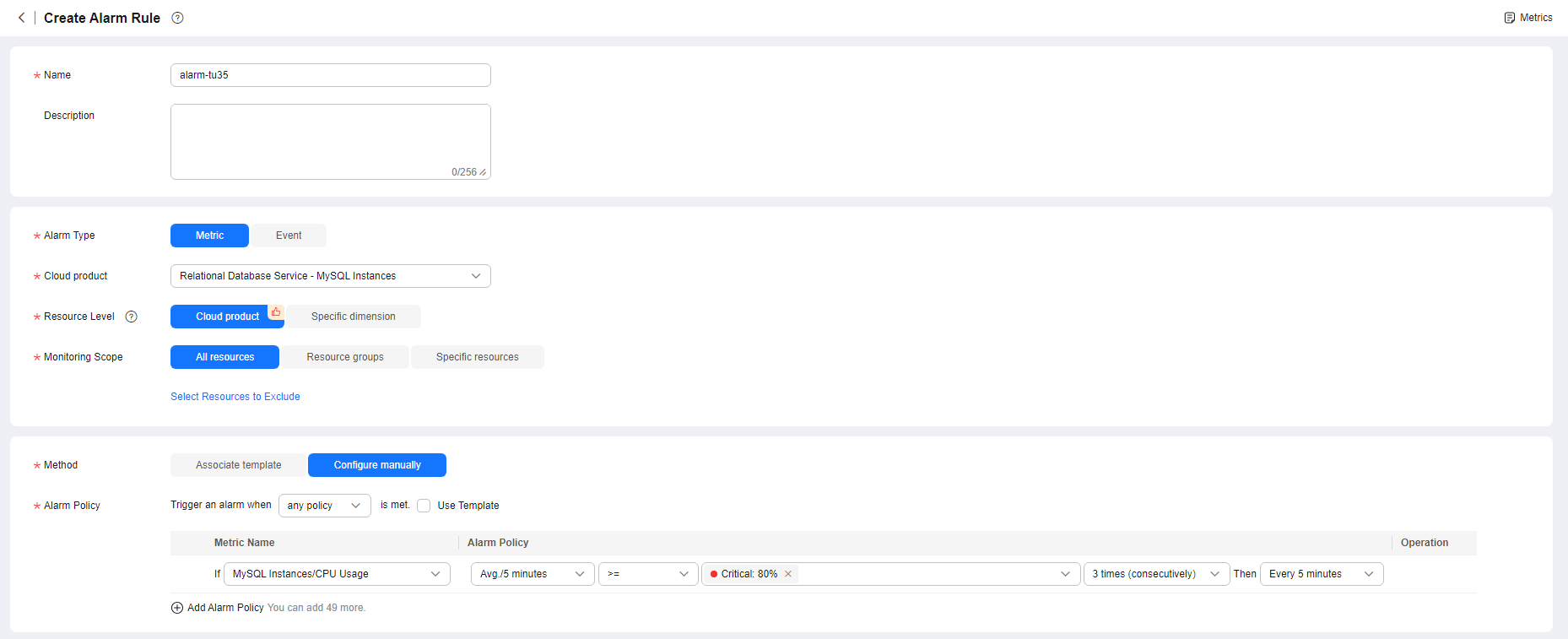
Table 1 Alarm rule information Parameter
Description
Name
Alarm rule name. The system generates a random name, which you can modify.
Description
Description about the rule.
Alarm Type
Select Metric.
Cloud product
Select Relational Database Service - MySQL Instances.
Resource Level
Cloud product is recommended.
Monitoring Scope
- All resources: An alarm will be triggered if any resource of the current cloud product meets the alarm policy. To exclude resources that do not require monitoring, click Select Resources to Exclude.
- Resource groups: An alarm will be triggered if any resource in the selected resource group meets the alarm policy.
- Specific resources: Click Select Specific Resources to select resources.
Method
- Associate template: After an associated template is modified, the policies contained in this alarm rule to be created will be modified accordingly.
You are advised to select Use existing template. The existing templates already contain three common alarm metrics: CPU usage, memory usage, and storage space usage.
- Configure manually: Configure alarm policies manually.
Template
If you select Associate template for Method, you need to select a template.
You can select a default alarm template or create a custom template.
Alarm Policy
If you select Configure manually for Method, you need to configure alarm policies.
Whether to trigger an alarm depends on whether the metric data in consecutive periods reaches the threshold. For example, Cloud Eye triggers an alarm every 5 minutes if the average CPU usage of the monitored object is 80% or more for three consecutive 5-minute periods.
NOTE:A maximum of 50 alarm policies can be added to an alarm rule. If any one of these alarm policies is met, an alarm is triggered.
Alarm Severity
The alarm severity can be Critical, Major, Minor, or Informational.
Figure 2 Configuring alarm notification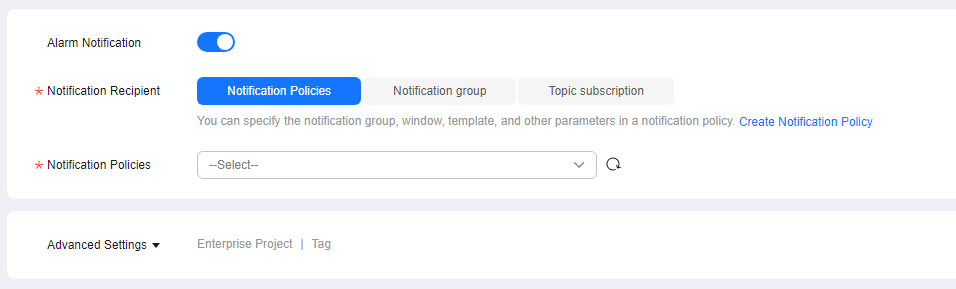
Table 2 Alarm notification Parameter
Description
Alarm Notification
Whether to notify users when alarms are triggered. Notifications can be sent by email, text message, or HTTP/HTTPS message.
Notification Recipient
You can select a notification group or topic subscription as required.
Notification Group
Notification group the alarm notification is to be sent to.
Notification Object
Object the alarm notification is to be sent to. You can select the account contact or a topic.
- The account contact is the mobile phone number and email address of the registered account.
- A topic is used to publish messages and subscribe to notifications.
Notification Window
Cloud Eye sends notifications only within the notification window specified in the alarm rule.
If Notification Window is set to 08:00-20:00, Cloud Eye sends notifications only within 08:00-20:00.
Trigger Condition
Condition for triggering an alarm notification. You can select Generated alarm (when an alarm is generated), Cleared alarm (when an alarm is cleared), or both.
Enterprise Project
Enterprise project that the alarm rule belongs to. Only users with the enterprise project permissions can view and manage the alarm rule.
Tag
A tag is a key–value pair. Tags identify cloud resources so that you can easily categorize and search for your resources.
- Click Create. The alarm rule is created.
For details about how to create alarm rules, see Creating an Alarm Rule in the Cloud Eye User Guide.
Metric Alarm Configuration Suggestions
|
Metric ID |
Metric Name |
Metric Description |
Threshold in Best Practices |
Alarm Severity in Best Practices |
Handling Suggestion |
|---|---|---|---|---|---|
|
rds001_cpu_util |
CPU Usage |
CPU usage of the monitored object |
Raw data > 80% for three consecutive periods |
Major |
|
|
rds002_mem_util |
Memory Usage |
Memory usage of the monitored object |
Raw data > 90% for three consecutive periods |
Major |
|
|
rds039_disk_util |
Storage Space Usage |
Storage space usage of the monitored object |
Raw data > 80% for three consecutive periods |
Major |
|
|
rds072_conn_usage |
Connection Usage |
Percent of used MySQL connections to the total number of connections |
Raw data > 80% for three consecutive periods |
Major |
|
|
rds073_replication_delay |
Real-Time Replication Delay |
Real-time replication delay between standby DB instances or read replicas and primary DB instances, corresponding to seconds_behind_master |
Raw data > 600s for three consecutive periods |
Major |
|
|
rds_mdl_lock_count |
MDL Locks |
Number of MDL locks |
Set the threshold based on your workloads. |
Major |
|
|
rds_long_transaction |
Long Transaction |
Maximum duration for starting a transaction A complete long transaction is counted only when the BEGIN and COMMIT commands exist before and after the related operation commands, respectively. |
Set the threshold as required. |
Major |
|
|
rds075_avg_disk_ms_per_read |
Disk Read Time |
Average time required for each disk read in a specified period |
Raw data > 50 ms for three consecutive periods |
Major |
|
|
rds076_avg_disk_ms_per_write |
Disk Write Time |
Average time required for each disk write in a specified period |
Raw data > 50 ms for three consecutive periods |
Major |
|
|
Metric ID |
Metric Name |
Metric Description |
Threshold in Best Practices |
Alarm Severity in Best Practices |
Handling Suggestion |
|---|---|---|---|---|---|
|
rds001_cpu_util |
CPU Usage |
CPU usage of the monitored object |
Raw data > 75% for three consecutive periods |
Major |
Upgrade the proxy specifications or add proxy nodes. For details, see Changing the Instance Class of a DB Proxy Instance and Changing the Number of Proxy Nodes. |
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot





