Security Best Practices
Huawei Cloud and you share the responsibility for security. Huawei Cloud is responsible for the security of cloud services for a secure cloud. As a tenant, you should utilize the security capabilities provided by cloud services to protect data and securely use the cloud. For details, see Shared Responsibilities.
This section provides actionable guidance for enhancing the overall security of CodeArts Deploy. You can use multiple security capabilities provided by CodeArts Deploy by referring to this document, improving the overall security defense and preventing data leakage and tampering during transmission.
You can evaluate the usage of CodeArts Deploy and make security configurations from the following dimensions as required.
- Optimizing Network Configurations to Reduce Network Attack Risks
- Properly Managing Host Accounts and Passwords/Keys to Reduce Data Leakage Risks
- Strengthening Permissions Management to Reduce Related Risks
- Enabling the CTS Log Audit Function for Backtracking
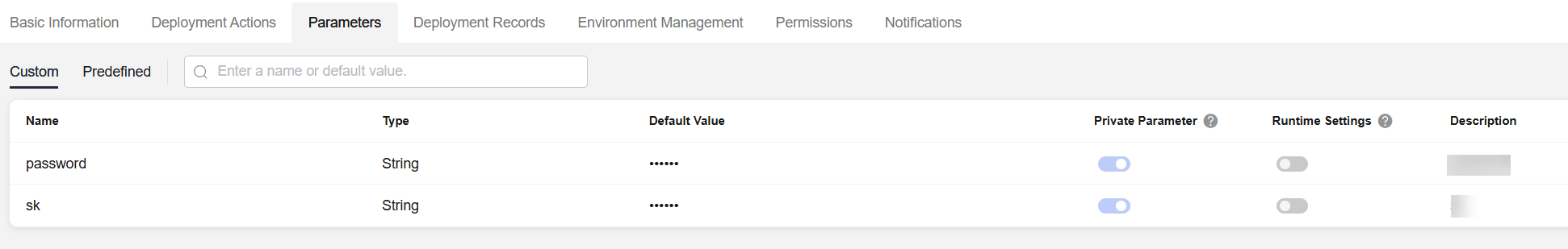
- Hardening Sensitive Deployment Parameters
Optimizing Network Configurations to Reduce Network Attack Risks
- Deploy target hosts on the internal network.
Target hosts carry your services. You should deploy target hosts on the internal network and use routers or firewalls to protect target hosts. Service nodes cannot be accessed from the Internet by EIP binding. In this way, unauthorized access and DDoS attacks can be prevented.
You can deploy services on the internal network by referring to the agent mode.
- Configure security group for target hosts in the direct connection mode.
For target hosts that are directly connected using EIPs, SSH is used to connect to the target hosts during task execution. The default port is 22 (Windows hosts use WinRM to connect to target hosts. The default port is 5986). Related ports are vulnerable to attacks. To prevent ports from being exposed to the public network, you need to configure a security group for your target hosts. The target hosts can be accessed only by using IP addresses related to CodeArts Deploy.
For details about the external IP address of CodeArts Deploy, see Notes and Constraints.
Properly Managing Host Accounts and Passwords/Keys to Reduce Data Leakage Risks
- Periodically change the host passwords/keys.
The host passwords or keys managed by CodeArts Deploy have high permissions. You are advised to periodically change the passwords or keys.
- Set Password Complexity.
Target hosts are easy to be attacked. Keep your database accounts and passwords secure.
Set password complexity for your hosts to avoid weak passwords.
Strengthening Permissions Management to Reduce Related Risks
Do not manage hosts as the root user.
CodeArts Deploy uses the account passwords or keys set during host management for deployment task execution. The root user has high system permissions. Therefore, do not manage hosts as the https://support.huaweicloud.com/intl/en-us/usermanual-cts/cts_02_0004.htmlOverviewroot user.
Enabling the CTS Log Audit Function for Backtracking
After CodeArts Deploy interconnects with CTS, key operations performed on CodeArts Deploy can be recorded in CTS for future audit.
For details about how to enable and configure CTS, see Enabling CTS.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot