Allowing Internet Traffic Only to a Specified Port
Application Scenarios
For security purposes, you need to allow traffic only from certain ports (such as ports 80 and 443) to access cloud resources.
This section describes how to configure CFW for refined management and control on cloud resources, allowing all EIPs to access port 80 of an EIP (xx.xx.xx.1).
Configuring CFW to Allow the Access Traffic from the Internet to a Specified Port
- Purchase the CFW standard or professional edition. For details, see Purchasing CFW.
- In the navigation pane on the left, click
 and choose . The Dashboard page will be displayed.
and choose . The Dashboard page will be displayed. - (Optional) Switch to another firewall instance. Select a firewall from the drop-down list in the upper left corner of the page.
- Enable protection for the EIP (xx.xx.xx.1).
- In the navigation pane, choose . The EIPs page is displayed. The EIP information (both IPv4 and IPv6) is automatically updated to the list.
- In the row of the EIP (xx.xx.xx.1), click in the Operation column.
- Configure protection rules.
- In the navigation pane, choose .
- On the Protection Rules > EIP tab page, click Add Rule. On the Add Rule page, configure protection information and set other parameters as needed.
Configure the following protection rules:
- One rule blocks all traffic and has the lowest priority.
- Direction: Inbound
- Source: Any
- Destination: Any
- Service: Any
- Application: Any
- Action: Block
Figure 1 Blocking all traffic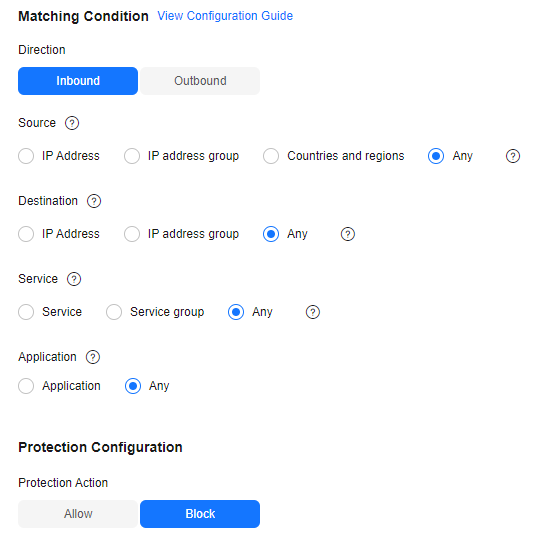
- The other rule allows the traffic from port 80 of EIP (xx.xx.xx.1) and has the highest priority.
Figure 2 Allowing access traffic to port 80 of xx.xx.xx.1
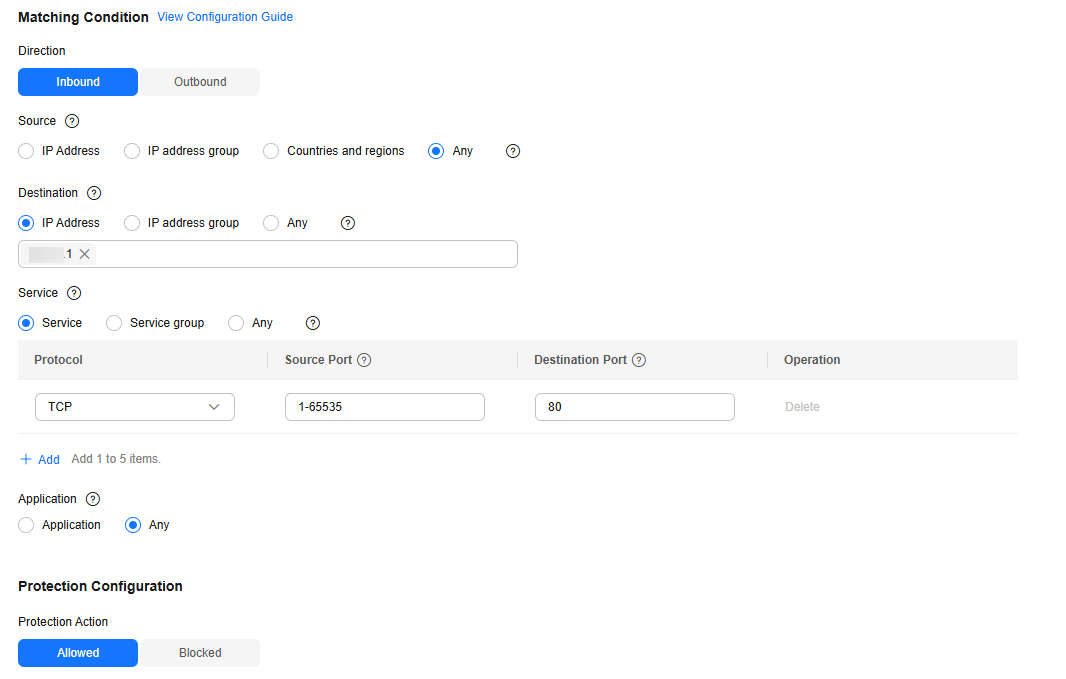
Table 1 Allowing access traffic to port 80 of xx.xx.xx.1 Parameter
Example Value
Description
Direction
Inbound
Direction of the protected traffic.
Source
Any
Origin of network traffic.
Destination
Select IP address and enter xx.xx.xx.1.
Receiver of network traffic.
Service
TCP/1-65535/80
Protocol, source port, and destination port of network traffic.
Application
Any
Protection policy for application layer protocols.
Action
Allow
Action taken when traffic passes through the firewall.
- One rule blocks all traffic and has the lowest priority.
- View the rule hits in access control logs.
In the navigation pane, choose Log Audit > Log Query. Click the Access Control Logs tab.

In the rows where Destination IP is xx.xx.xx.1, the corresponding Action is Block.
References
For details about how to add other protection rules, see the parameter description in Adding a Protection Rule.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot





