Web UI Mode
After logging in to the partner sales platform, a customer can directly switch to HUAWEI CLOUD to purchase cloud services and manage cloud service resources. The partner sales platform must complete SAML authentication to establish a trust relationship with HUAWEI CLOUD.
Prerequisites
The partner has performed steps in Access Configuration.
SAML Authentication
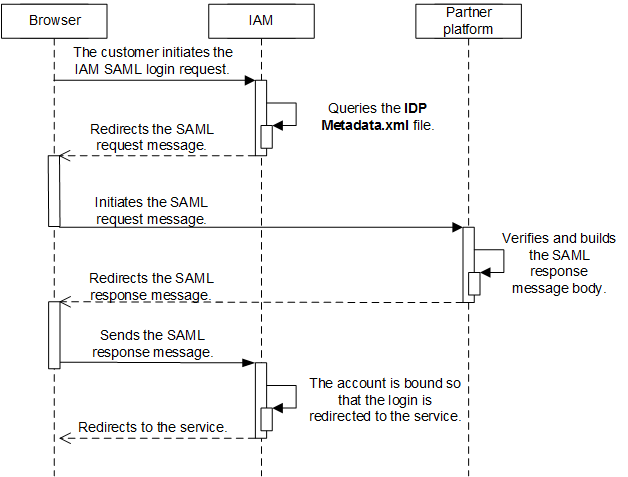
Figure 1 shows the SAML authentication process.
- A partner's customer uses a browser to call the HUAWEI CLOUD login link. IAM sends the SAML request.
- The customer uses a browser to call the HUAWEI CLOUD login link.
https://auth-intl.huaweicloud.com/authui/saml/login?xAccountType=ZXT&isFirstLogin=false&service=https%3a%2f%2fconsole-intl.huaweicloud.com%2fiam%2f
Parameter
Mandatory
Description
Example
xAccountType
Yes
Indicates the identifier of the partner sales platform, which is globally unique. The value is provided by Huawei. After the partner configures the access parameters on the Partner Center page, the partner ID is generated. For details about how to obtain the platform ID, see How Do I Obtain the xaccountType Value?
ZXT
isFirstLogin
No
If no HUAWEI CLOUD account is bound, this parameter is mandatory and must be set to true. Otherwise, the value can be left empty or set to false.
After the account creation API is successfully called to create a customer account, HUAWEI CLOUD CBC has bound the customer account on the partner sales platform with the customer HUAWEI CLOUD account.
false
service
Yes
Indicates the redirection address after login.
The encodeURIComponent function is used for coding.
https%3a%2f%2fconsole-intl.huaweicloud.com%2fiam%2f
- IAM receives the login request of the partner's customer, locates the SingleSignOnService configuration item in the IDP Metadata.xml file based on the xAccountType value, and sends the samlRequest request to the required path.

Parameter
Description
SAMLRequest
Indicates the response message body.
The response message is in XML format. IAM then compresses the message, encodes the message using Base64, and URL encodes the message.
- If the partner uses the SAML toolkits, this parameter can be directly used. The partner does not need to parse the XML file.
- If the partner needs to parse the XML file, the partner needs to URL decode the message, decode the message using Base64, and decompress the message (zip.inflate). For details, see Sample Code for Parsing the SAMLRequest.
RelayState
Indicates the response parameters for SAML.
SigAlg
Indicates the signature algorithm. Huawei uses SHA256 for signatures by default.
HTTP://WWW.W3.ORG/2001/04/XMLDSIG-MORE#RSA-SHA256
Signature
Indicates the signature. The signature is used to verify the initiator of a request.
When initiating a request, HUAWEI CLOUD uses the private key to sign SAMLRequest={ SAMLRequest }&RelayState={ RelayState } &SigAlg={ SigAlg } in request https://www.test.com/saml/login?SAMLRequest={SAMLRequest }&RelayState={ RelayState} &SigAlg={ SigAlg}&Signature={ Signature } and then performs Base64 coding to obtain the signature value.
The signature algorithm is specified by the SigAlg field.
When receiving the request, the receiver verifies the signature value using the public key provided by HUAWEI CLOUD (the value in the <ds:X509Certificate></ds:X509Certificate> tag in the SP Metadata.xml file).
If the signature verification succeeds, the request is sent by HUAWEI CLOUD, and the follow-up operations can be performed. Otherwise, the request is invalid.
- The customer uses a browser to call the HUAWEI CLOUD login link.
- The partner sales platform generates the SAML response message and sends it to HUAWEI CLOUD IAM.
- The partner sales platform obtains the HUAWEI CLOUD public key and the response message path of samlResponse from the SP Metadata.xml file. For details, see Example, Public Key, and Response Path in Obtaining the SP Metadata File.
- The partner sales platform generates the SAML response message.
The response message body is in XML format. For the correct response message body and its parameter description, see the following displayed content.

The following content is for reference only. The description in the comments must be modified. The time and ID defined by SAML vary depending on the message. Therefore, it is recommended that you should not directly modify the response message content. Instead, you shall use the SAML toolkits to generate the response message.
<?xml version="1.0" encoding="UTF-8"?> <!-- Parameter InResponseTo needs to be the same as the ID configuration item of AuthnRequest in the SAML request message. --> <!-- Parameter Destination needs to be the same as the Location value in the AssertionConsumerService tag in the SP Metadata.xml file. --> <saml2p:Response Consent="urn:oasis:names:tc:SAML:2.0:consent:unspecified" ID="_d794dc393ae6724e236003bf0b917cf0" Destination="https://auth.huaweicloud.com/authui/saml/SAMLAssertionConsumer" InResponseTo="_dck4mm08qmdhc8k4nuir07hghetdqqg8umg5" IssueInstant="2018-10-30T08:21:41.740Z" Version="2.0" xmlns:saml2p="urn:oasis:names:tc:SAML:2.0:protocol"> <!-- Must be the same as the entityID value in the IDP Metadata.xml file. --> <saml2:Issuer Format="urn:oasis:names:tc:SAML:2.0:nameid-format:entity" xmlns:saml2="urn:oasis:names:tc:SAML:2.0:assertion">https://www.test.com</saml2:Issuer> <saml2p:Status> <saml2p:StatusCode Value="urn:oasis:names:tc:SAML:2.0:status:Success" /> <saml2p:StatusMessage>urn:oasis:names:tc:SAML:2.0:status:Success</saml2p:StatusMessage> </saml2p:Status> <saml2:Assertion ID="_2320c40ac7b5e857b2d0d4ea0c8758c3" IssueInstant="2018-10-30T08:21:41.740Z" Version="2.0" xmlns:saml2="urn:oasis:names:tc:SAML:2.0:assertion" xmlns:xsd="http://www.w3.org/2001/XMLSchema"> <!-- Must be the same as the entityID value in the IDP Metadata.xml file. --> <saml2:Issuer>https://www.test.com</saml2:Issuer> <ds:Signature xmlns:ds="http://www.w3.org/2000/09/xmldsig#"> <ds:SignedInfo> <ds:CanonicalizationMethod Algorithm="http://www.w3.org/2001/10/xml-exc-c14n#" /> <ds:SignatureMethod Algorithm="http://www.w3.org/2001/04/xmldsig-more#rsa-sha256" /> <!-- The value after "URI #" must be the same as the ID in the Assertion tag. --> <ds:Reference URI="#_2320c40ac7b5e857b2d0d4ea0c8758c3"> <ds:Transforms> <ds:Transform Algorithm="http://www.w3.org/2000/09/xmldsig#enveloped-signature" /> <ds:Transform Algorithm="http://www.w3.org/2001/10/xml-exc-c14n#"> <ec:InclusiveNamespaces PrefixList="xsd" xmlns:ec="http://www.w3.org/2001/10/xml-exc-c14n#" /> </ds:Transform> </ds:Transforms> <ds:DigestMethod Algorithm="http://www.w3.org/2001/04/xmlenc#sha256" /> <!-- The value of DigestValue is the digest of the Assertion tag object. The digest algorithm is the same as that of DigestMethod. --> <ds:DigestValue>rFxrycznfGNYOnprZIFJJou4ro0Mz65+43MIR5F0+H4=</ds:DigestValue> </ds:Reference> </ds:SignedInfo> <!-- Partner signature value. For details about how to obtain the value, see the following description. --> <ds:SignatureValue> YqTWQngAPfGqQmWa610PM7LeefqWdKuveUVINrqL67NoHJIDa2WxLwdVzoJIlJh64QiNPr6+ndmL DCMgIC5F/9ijuzhIICZcc6lHNIjy6EsPkKRjfo9oeoVAqLgG/kmVQYeHLBID0y11RNXXpAVY4nhJ 26KiIVGt7ywyKAmhichE+eW/UYAGiOI5vkfgD2gZUGV+yPkv64k7xK4yAH3mL2NaCPuw/90e4enm iUx0YuazDwM5FiRUSMpcJs0rcNmS6clWAUcCzbOx+y2vJGtTjHb7k3UsmpnTop5eYNp94+sDPEat 8FaV4SgafMEL5z54gpe8+//9yOWEvlBs1b0RYg== </ds:SignatureValue> <ds:KeyInfo> <ds:X509Data> <!-- Partner public key certificate. The certificate must be the one specified in the IDP Metadata.xml file. --> <ds:X509Certificate> MIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAhK3L160NjP9EhBGQOC2s4r+Wc62bkRkc nUxfhiZwCwJdQCykzuLOAoATnfoEamV5W25xtSS5kFs+4OC0mYVpKcI3SWoydX+UE5Qik5UfJ8Dt G1AvSEKhSluyO9axrV5Uv089jMxBnlm/R+xND73WcZM11yIbKJEZSTCEDfh+KnFbMw108umFMden RZCrNWUJoSp/90XeG0V2Nmj7Fkq72skSifwIASLRq9KqLbmh1QwUX+AoWpHK/jRUBustMBmG1n1i AqpD4EBjjBOB27k1wXZ30+IoJt8IZmfSZRFoNn5VFWXNeEmZ1aQvGSvd3Tyyw2/Wr+w/8Mags69C mpeX6QIDAQAB </ds:X509Certificate> </ds:X509Data> </ds:KeyInfo> </ds:Signature> <saml2:Subject> <!-- The value of NameQualifier must be the same as the entityID value in the SP Metadata.xml file. --> <saml2:NameID Format="urn:oasis:names:tc:SAML:2.0:nameid-format:transient" NameQualifier="https://auth.huaweicloud.com/">Some NameID value</saml2:NameID> <saml2:SubjectConfirmation Method="urn:oasis:names:tc:SAML:2.0:cm:bearer"> <!-- Parameter InResponseTo needs to be the same as the ID configuration item of AuthnRequest in the samlRequest message. --> <saml2:SubjectConfirmationData InResponseTo="_dck4mm08qmdhc8k4nuir07hghetdqqg8umg5" NotBefore="2018-10-28T08:21:41.740Z" NotOnOrAfter="2018-11-01T08:21:41.740Z" Recipient="https://auth.huaweicloud.com/authui/saml/SAMLAssertionConsumer" /> </saml2:SubjectConfirmation> </saml2:Subject> <saml2:Conditions NotBefore="2018-10-28T08:21:41.740Z" NotOnOrAfter="2018-11-01T08:21:41.740Z"> <saml2:AudienceRestriction> <!-- Must be the same as the entityID value in the SP Metadata.xml file. --> <saml2:Audience>https://auth.huaweicloud.com/</saml2:Audience> </saml2:AudienceRestriction> </saml2:Conditions> <saml2:AttributeStatement> <!-- For values between<saml2:AttributeValue> and </saml2:AttributeValue>, see the following table. --> <saml2:Attribute FriendlyName="xUserId" Name="xUserId" NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:uri"> <saml2:AttributeValue xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xsi:type="xsd:string">*******</saml2:AttributeValue> </saml2:Attribute> <!-- The values of xAccountId and xUserId must be the same. --> <saml2:Attribute FriendlyName="xAccountId" Name="xAccountId" NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:uri"> <saml2:AttributeValue xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xsi:type="xsd:string">********</saml2:AttributeValue> </saml2:Attribute> <saml2:Attribute FriendlyName="bpId" Name="bpId" NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:uri"> <saml2:AttributeValue xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xsi:type="xsd:string">******</saml2:AttributeValue> </saml2:Attribute> <saml2:Attribute FriendlyName="email" Name="email" NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:uri"> <saml2:AttributeValue xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xsi:type="xsd:string" /> </saml2:Attribute> <saml2:Attribute FriendlyName="name" Name="name" NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:uri"> <saml2:AttributeValue xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xsi:type="xsd:string">******</saml2:AttributeValue> </saml2:Attribute> <saml2:Attribute FriendlyName="mobile" Name="mobile" NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:uri"> <saml2:AttributeValue xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xsi:type="xsd:string">*****</saml2:AttributeValue> </saml2:Attribute> </saml2:AttributeStatement> <saml2:AuthnStatement AuthnInstant="2018-10-30T08:21:41.741Z"> <!-- Must be the same as the entityID value in the SP Metadata.xml file. --> <saml2:SubjectLocality Address="https://auth.huaweicloud.com/" /> <saml2:AuthnContext> <saml2:AuthnContextClassRef>urn:oasis:names:tc:SAML:2.0:ac:classes:unspecified</saml2:AuthnContextClassRef> </saml2:AuthnContext> </saml2:AuthnStatement> </saml2:Assertion> </saml2p:Response>The partner signature value is in standard XML format, and the signature type is enveloped-signature. You are advised to use the SAML library provided by a third party for signature.
The signature procedure is as follows.
- Obtain the signature object (Assertion).
<saml2:Assertion ID="_2320c40ac7b5e857b2d0d4ea0c8758c3" IssueInstant="2018-10-30T08:21:41.740Z" Version="2.0" xmlns:saml2="urn:oasis:names:tc:SAML:2.0:assertion" xmlns:xsd="http://www.w3.org/2001/XMLSchema"> ...... </saml2:Assertion> - Obtain the tag object (Signature).
<ds:Signature xmlns:ds="http://www.w3.org/2000/09/xmldsig#"> <ds:SignedInfo> <ds:CanonicalizationMethod Algorithm="http://www.w3.org/2001/10/xml-exc-c14n#" /> <ds:SignatureMethod Algorithm="http://www.w3.org/2000/09/xmldsig#rsa-sha256" /> <ds:Reference URI="#_2320c40ac7b5e857b2d0d4ea0c8758c3"> <ds:Transforms> <ds:Transform Algorithm="http://www.w3.org/2000/09/xmldsig#enveloped-signature" /> <ds:Transform Algorithm="http://www.w3.org/2001/10/xml-exc-c14n#"> <ec:InclusiveNamespaces xmlns:ec="http://www.w3.org/2001/10/xml-exc-c14n#" PrefixList="xs" /> </ds:Transform> </ds:Transforms> <ds:DigestMethod Algorithm="http://www.w3.org/2000/09/xmldsig#sha256" /> <ds:DigestValue>......</ds:DigestValue> </ds:Reference> </ds:SignedInfo> <!-- Third-party signature value --> <ds:SignatureValue> ...... </ds:SignatureValue> <ds:KeyInfo> <ds:X509Data> <!-- Third-party public key certificate --> <ds:X509Certificate> ...... </ds:X509Certificate> </ds:X509Data> </ds:KeyInfo> </ds:Signature> - Generate the DigestValue value for the signature object Assertion.
- Convert Assertion according to the algorithm defined in Transform of Signature.
- Generate a digest for the object obtained in 1) according to the algorithm specified in DigestMethod.
- Place the generated digest value in the DigestValue tag.
- Use the private key in Step 6 in Generating a Certificate to generate the SignatureValue value for the SignedInfo object signature.
- Convert SignedInfo according to the algorithm defined in CanonicalizationMethod
- Generate the signature value for the object obtained in 1) according to the signature algorithm defined in SignatureMethod. Place the obtained signature value in SignatureValue.
- Combine the values of DigestValue and SignatureValue to form the final Signature object. Place the value in Assertion as its sub-element.
The signature is displayed as follows.
<saml2:Assertion ID="_2320c40ac7b5e857b2d0d4ea0c8758c3" IssueInstant="2018-10-30T08:21:41.740Z" Version="2.0" xmlns:saml2="urn:oasis:names:tc:SAML:2.0:assertion" xmlns:xsd="http://www.w3.org/2001/XMLSchema"> ...... <ds:Signature xmlns:ds="http://www.w3.org/2000/09/xmldsig#"> ...... <!-- Third-party signature value --> <ds:SignatureValue> ...... </ds:SignatureValue> <ds:KeyInfo> <ds:X509Data> <!-- Third-party public key certificate --> <ds:X509Certificate> ...... </ds:X509Certificate> </ds:X509Data> </ds:KeyInfo> </ds:Signature> </saml2:Assertion>Table 1 Description of parameters between <saml2:AttributeValue> and </saml2:AttributeValue> Parameter
Description
xUserId
Indicates the user ID of the partner's customer on the partner sales platform. This parameter value equals the value of xAccountId.
xAccountId
Indicates the account ID of the partner's customer on the partner sales platform.
bpId
Indicates the partner ID.
For details, see How Do I Check the Partner ID?
email
Indicates the email address.
This parameter is optional.
The parameter must meet the following requirements:
- Must be unique for each customer.
- A maximum of 64 characters
- Passes the verification using the following regular expression: ^[azA-Z0-9.!#$%&'*+\\/=?^_`{|}~-]+@[a-zA-Z0-9](?:[a-zA-Z0-9-]{0,61}[a-zA-Z0-9])?(?:\\.[azA-Z0-9](?:[a-zA-Z0-9-]{0,61}[a-zA-Z0-9])?)*$
name
Indicates the account name transferred on the partner sales platform.
This parameter is optional.
The account name must be the same as the value of domain_name in the request for API in Creating a Customer.
Table 1 involves the account ID and user ID because HUAWEI CLOUD IAM has the account and user concepts. For details about the two concepts, see "Account" and "IAM User" in Basic Concepts.
- Obtain the signature object (Assertion).
- If the customer has logged in to the partner sales platform, the SAML response message is returned directly. Otherwise, the SAML response message is displayed after the login.
Send a POST request to the HUAWEI CLOUD response path AssertionConsumerService in 2.a. The parameters must be in the Form Data format.

Parameter
Description
SAMLResponse
Identifies the string obtained by encoding the SAML response message body in 2.b using Base64.
RelayState
The value of this parameter is the same as that in the SAML request message.
- IAM parses the SAMLResponse. When the customer account creation API is called to create an account, HUAWEI CLOUD CBC binds the customer account on the partner sales platform with the HUAWEI CLOUD account. Therefore, the customer can be redirected to the service page and purchase and manage the cloud services.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot