OTA Upgrade for MQTT Devices
Software Upgrade for Devices Using MQTT
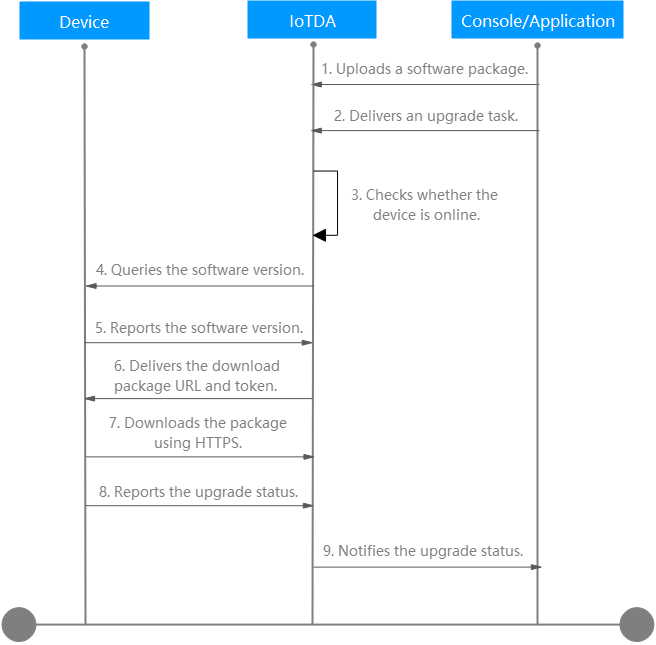
The SOTA process for a device using MQTT is as follows:
1–2: A user uploads a software package on the IoTDA console and creates a software upgrade task on the console or an application.
3. The platform checks whether the device is online and triggers the upgrade negotiation process immediately when the device is online. If the device is offline, the platform waits for the device to go online and subscribes to the upgrade topic. After detecting that the device goes online, the platform triggers the upgrade negotiation process. (The timeout interval for the device to go online is within 25 hours.)
- If the returned software version is the same as the target version, no upgrade is required. The upgrade task is marked successful.
- If the returned software version is different from the target version and this version supports upgrades, the platform continues the upgrade.
6–7: The platform delivers the package download URL, token, and package information. The user downloads the software package using HTTPS based on the package download URL and token. The token is valid for 24 hours. (The timeout interval for package download and upgrade status reporting is 24 hours.)
8. The device upgrades the firmware. After the upgrade is complete, the device returns the upgrade result to the platform. (If the version number returned after the device upgrade is the same as the configured version number, the upgrade is successful.)
9. The platform notifies the IoTDA console or application of the upgrade result.
Firmware Upgrade for Devices Using MQTT

The FOTA process for a device using MQTT is as follows:
1–2: A user uploads a firmware package on the IoTDA console and creates a firmware upgrade task on the console or an application.
3. The platform checks whether the device is online and triggers the upgrade negotiation process immediately when the device is online. If the device is offline, the platform waits for the device to go online and subscribes to the upgrade topic. After detecting that the device goes online, the platform triggers the upgrade negotiation process. (The timeout interval for the device to go online is within 25 hours.)
- If the returned firmware version is the same as the target version, no upgrade is required. The upgrade task is marked successful.
- If the returned firmware version is different from the target version and this version supports upgrades, the platform continues the upgrade.
6–7: The platform delivers the package download URL, token, and package information. The user downloads the software package using HTTPS based on the package download URL and token. The token is valid for 24 hours. (The timeout interval for package download and upgrade status reporting is 24 hours.)
8. The device upgrades the firmware. After the upgrade is complete, the device returns the upgrade result to the platform. (If the version number returned after the device upgrade is the same as the configured version number, the upgrade is successful.)
9. The platform notifies the IoTDA console or application of the upgrade result.
The platform supports resumable download.
Firmware Upgrade Failure Causes
The following table lists the failure causes reported by the platform.
|
Error Message |
Description |
Solution |
|---|---|---|
|
Device Abnormal is not online |
The device is offline or abnormal. |
Check the device. |
|
Task Conflict |
A task conflict occurs. |
Check whether a software upgrade, firmware upgrade, log collection, or device restart task is in progress. |
|
Waiting for the device online timeout |
The device does not go online within the specified time. |
Check the device. |
|
Wait for the device to report upgrade result timeout |
The device does not report the upgrade result within the specified time. |
Check the device. |
|
Waiting for report device firmware version timeout |
The device does not report the firmware version within the specified time. |
Check the device. |
|
Waiting for report cellId timeout |
The device does not report the cell ID within the specified time. |
Check the device. |
|
Updating timeout and query device version for check timeout |
The device does not report the upgrade result or device version within the specified time. |
Check the device. |
|
Waiting for device downloaded package timeout |
The device does not finish downloading the firmware package within the specified time. |
Check the device. |
|
Waiting for device start to update timeout |
The device does not start the update within the specified time. |
Check the device. |
|
Waiting for device start download package timeout |
The device does not start to download the firmware package within the specified time. |
Check the device. |
The following table lists the failure causes reported by devices.
|
Error Message |
Description |
Solution |
|---|---|---|
|
Not enough storage for the new firmware package |
The storage space is insufficient for the firmware package. |
Check the storage space of the device. |
|
Out of memory during downloading process |
The memory was insufficient during the download. |
Check the device memory. |
|
Connection lost during downloading process |
The connection was interrupted during the download. |
Check the device connection status. |
|
Integrity check failure for new downloaded package |
The integrity check on the firmware package fails. |
Check whether the firmware package downloaded is complete. |
|
Unsupported package type |
The firmware package type is not supported. |
Check whether the device status and firmware package provided by the manufacturer are correct. |
|
Invalid URI |
The URI is invalid. |
Check whether the download address of the firmware package is correct. |
|
Firmware update failed |
The firmware fails to update. |
Check the device. |
FAQ
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot





