Using a Private NAT Gateway and Direct Connect to Enable Communications Between a VPC and an On-premises Data Center
Scenarios
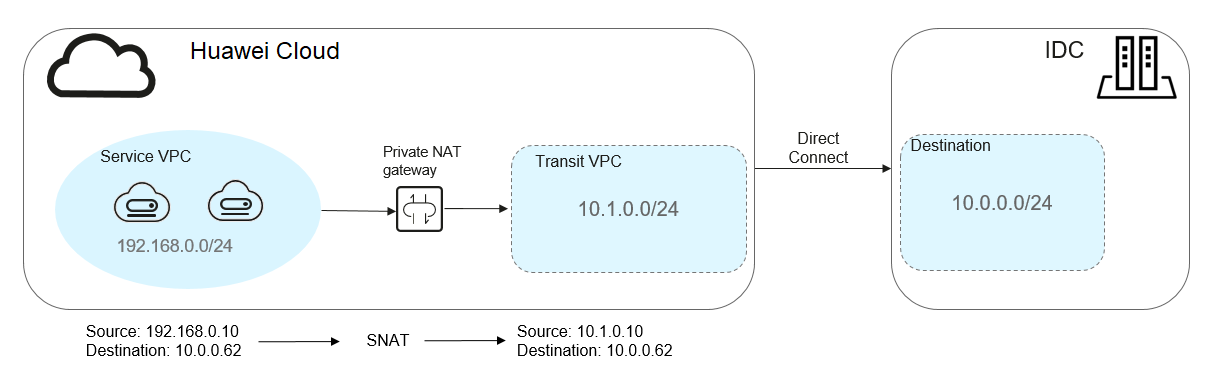
When an ECS in a VPC needs to communicate with an on-premises data center through a Direct Connect connection, the private IP address of the ECS needs to be translated into a private IP address trusted by the on-premises data center.
Solution Architecture
- A Direct Connect connection is used to connect the on-premises data center to the transit VPC.
- A private NAT gateway is configured to translate the private IP address of the ECS in the service VPC into a transit IP address (private IP address trusted by the on-premises data center) in the transit VPC.
Figure 1 Networking diagram
Solution Advantages
In a hybrid cloud scenario, the private IP addresses of ECSs in the VPC need to be mapped to those trusted by the on-premises data center to meet security compliance requirements.
Constraints and Limitations
- The CIDR block of your on-premises data center cannot overlap with the subnet CIDR block of the transit VPC and the CIDR block of the service VPC, or your on-premises data center will be unable to communicate with the service VPC.
- You need to define a CIDR block in the transit VPC that you can map private IP addresses in the service VPC to. Generally, you either use a private CIDR block or use private IP address trusted by your on-premises data center.
Resource and Cost Planning
|
Resource |
Resource Name |
Description |
Quantity |
|---|---|---|---|
|
VPC |
VPC-Test01 |
The service VPC: 192.168.0.0/24 |
1 |
|
VPC-Test02 |
The transit VPC: 10.1.0.0/24 |
1 |
|
|
NAT gateway |
NAT-Private-Test |
A private NAT gateway purchased and deployed in VPC-Test01 |
1 |
|
NAT-Ext-Sub-IP-Test |
The transit IP address. The transit VPC is VPC-Test02, and transit IP address is 10.1.0.10 |
1 |
|
|
Direct Connect connection |
DC-Test |
A Direct Connect connection linking the on-premises data center to the transit VPC |
1 |
|
ECS |
ECS-Test |
An ECS purchased and deployed in VPC-Test01. Private IP address: 192.168.0.10 |
1 |
|
On-premises data center |
IDC-Test |
CIDR block: 10.0.0.0/24; private IP address of the server: 10.0.0.62 |
1 |
- The private IP address (192.168.0.10) of the ECS is mapped to the private IP address (10.1.0.10) trusted by the on-premises data center through the private NAT gateway.
- The VPC, NAT gateway, Direct Connect connection, and ECS must be in the same region.
Tasks
Procedure
- Create a service VPC and a transit VPC.
For detailed operations, see Creating a VPC.
- Configure a Direct Connect connection.
Create a Direct Connect connection between the on-premises data center and the transit VPC. For details, see Overview.
- Buy a private NAT gateway.
- Buy a private NAT gateway in the specified region and select a service VPC.
- Assign a transit IP address by setting Transit VPC to VPC-Test02, selecting Manual for Transit IP Address, and setting IP address to 10.1.0.10.
- On the SNAT Rules tab of the purchased private NAT gateway, click Add SNAT Rule and set Subnet to 192.168.0.0/24, the service subnet with the IP addresses that need to be mapped to those of the on-premises data center. Set Transit IP Address to the address configured in the previous step.
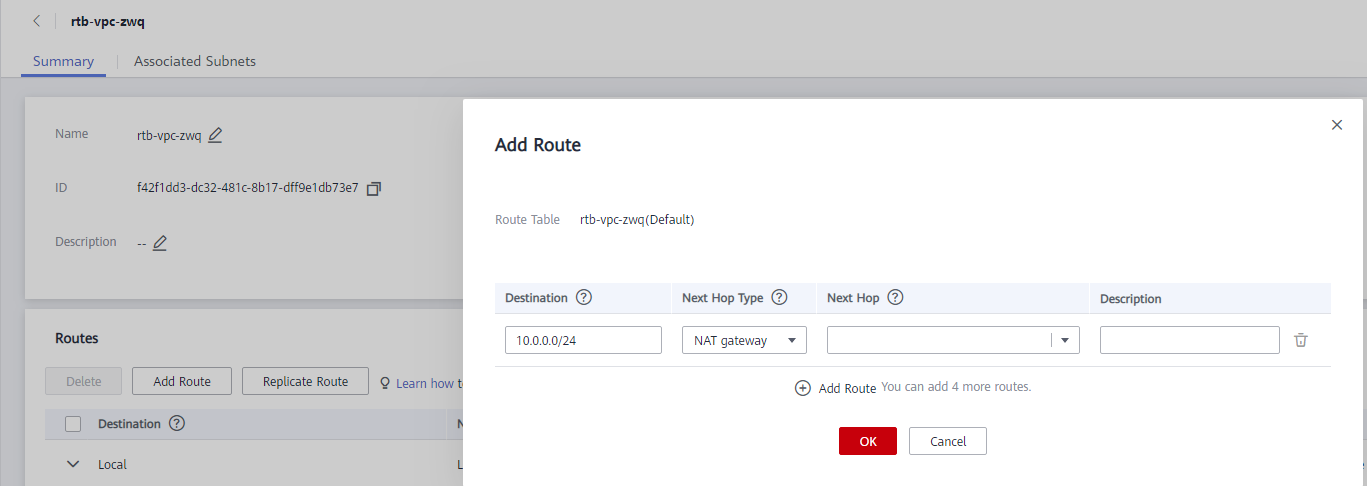
- Add a route pointing to the private NAT gateway in the service VPC. Set Destination to 10.0.0.0/24.
Figure 2 Adding a route
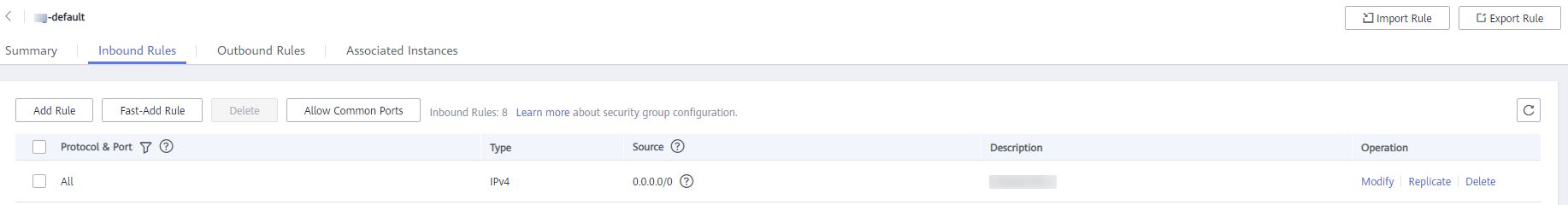
- Add an inbound security group rule for the on-premises server (private IP address: 10.0.0.62).
Figure 3 Adding an inbound security group rule
Verification
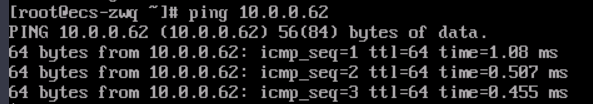
After the configuration is complete, test the network connectivity.
Log in to ECS (ECS-Test) in the service VPC and ping the private IP address (10.0.0.62) of the on-premises data center to confirm the configuration was successful.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot





