Querying Client IP Addresses in ELB Access Logs
Scenarios
When you are using ELB to distribute traffic, you may need to use the client IP addresses for analyzing data and protecting services.
To do this, you can enable access logging for Layer 7 listeners of a load balancer. Then, you can find the client IP addresses in the access logs of the load balancer.
Constraints
Access logging can be configured only for load balancers with HTTP, QUIC, TLS, or HTTPS listeners.
Preparations
- There is a dedicated load balancer with an EIP bound to it. If there is no such a load balancer, you can buy one and bind an IPv4 EIP to the load balancer.
- There is an HTTPS backend server group with an ECS (ECS01) running in it. The ECS is in the same VPC as the load balancer, and an application has been deployed on ECS01. For details about how to deploy an application for testing, see Deploying an Application.
- You have enabled LTS and have created a log group and log stream. For details, see Ingesting ELB Logs to LTS.
- You have set cloud structuring parsing for the log stream and have selected ELB as the system template. For details, see Setting Cloud Structuring Parsing.
Step 1: Upload the Server Certificate to ELB
Before adding an HTTPS listener to a load balancer, you need to upload your certificate to the ELB console.
- Go to the load balancer list page.
- In the navigation pane on the left, choose Certificates.
- Click Add Certificate in the top right corner and set parameters by referring to Table 1.
Table 1 Server certificate parameters Parameter
Description
Certificate Type
Specifies the certificate type. Select Server certificate.
Source
Specifies the source of a certificate. There are two options: SSL Certificate Manager and Your certificate.
SSL Certificate Manager is used in this example, so that you can select the SSL certificates you have purchased on the CCM console.
Certificate
Specifies the certificate that you want to upload to the ELB console.
Enterprise Project
Specifies an enterprise project by which cloud resources and members are centrally managed.
SNI Domain Name (Optional)
All domain names of the SSL certificate will be automatically selected.
If the certificate is intended for SNI, you can select an SNI certificate based on the domain name in the HTTPS requests.
Description (Optional)
Provides supplementary information about the certificate.
- Click OK.
Step 2: Add an HTTPS Listener and Configure One-Way Authentication
- Go to the load balancer list page.
- Locate the target load balancer and click Add Listener in the Operation column.
- On the Add Listener page, select HTTPS for Frontend Protocol and One-way authentication for SSL Authentication.
Select the server certificate uploaded to the ELB console in Step 1.
Transfer Client IP Address is enabled by default for the HTTPS listener of the dedicated load balancer, which means that client IP addresses can be placed in the X-Forwarded-For header and transferred to the backend servers.
Figure 1 Configuring one-way authentication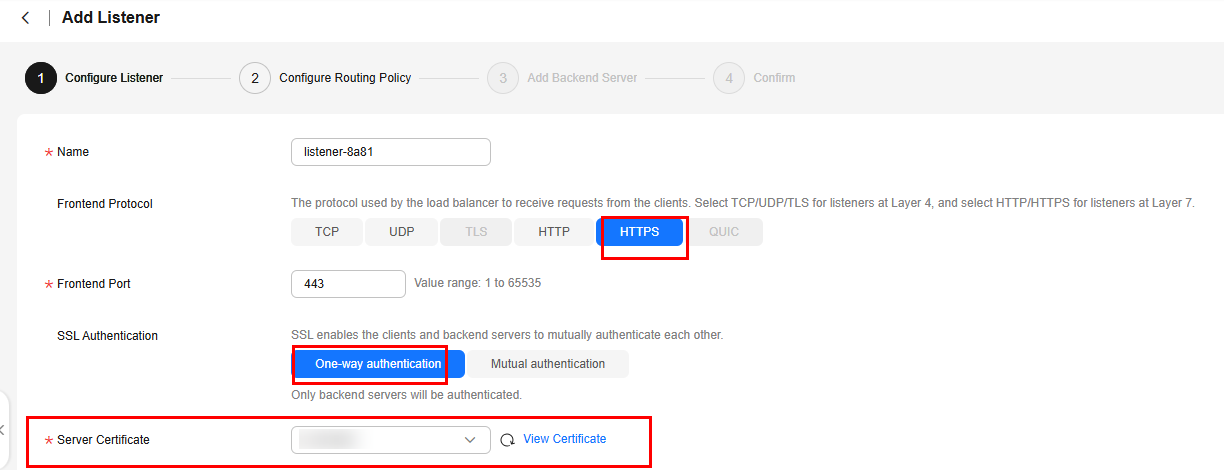
- Click Next: Configure Request Routing Policy and select Use existing for Backend Server Group.
Select an existing backend server group and click Next: Confirm.
- Confirm the configurations and click Submit.
Step 3: Configure Access Logging
- Go to the load balancer list page.
- On the Load Balancers tab, locate the load balancer and click its name.
- Under Access Logs, click Configure Access Logging.
- Enable access logging and select the log group and log stream you have created.
Figure 2 Configuring access logging
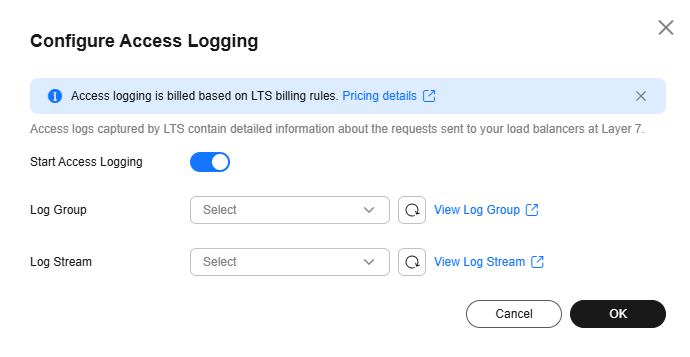
- Click OK.
Step 4: Access the Load Balancer Through Its EIP
Step 5: Check the Client IP Address in Access Logs
- On the Access Logs tab of the load balancer, click View Log Details. The log management page of the LTS console is displayed.
Figure 4 Viewing the log group
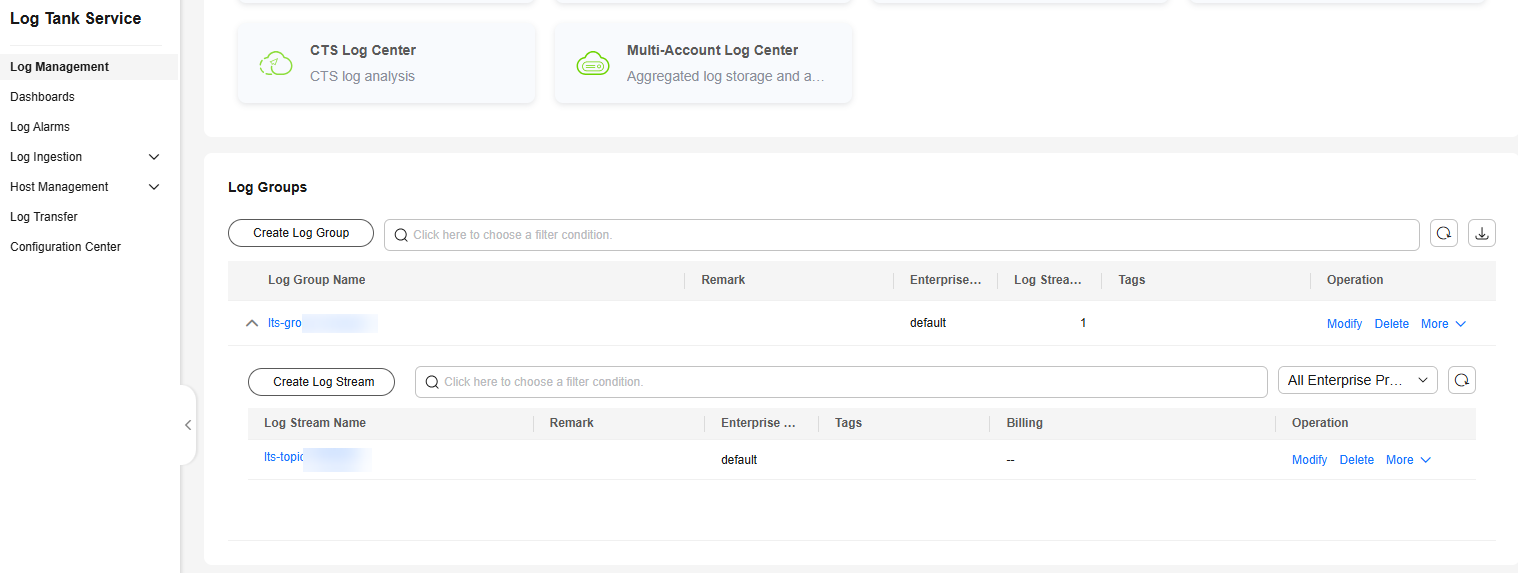
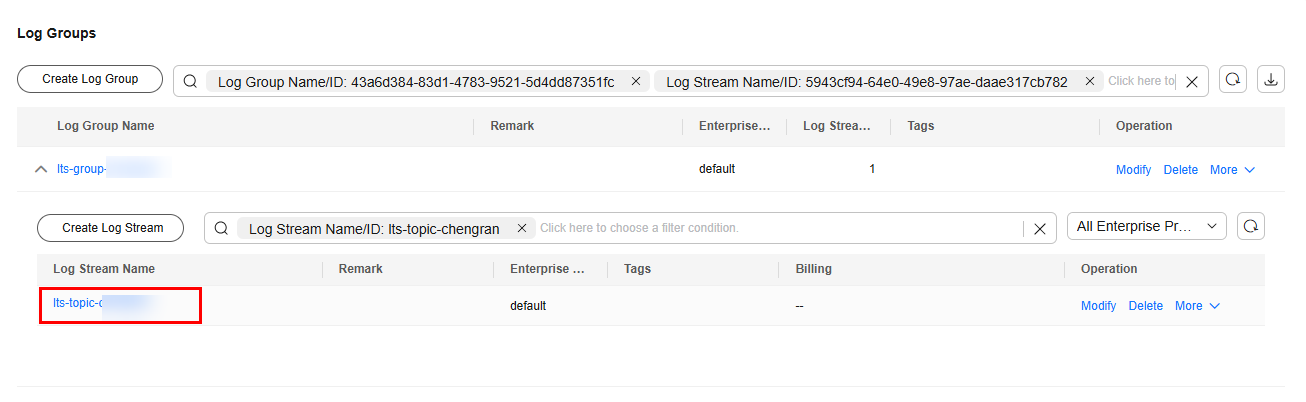
- On the Log Groups page, click the log stream name to go to its details page.
Figure 5 Viewing the log stream
- On the log stream details page, check the client IP address in the log list.
- If the client directly accesses the load balancer, the IP address in the remote_addr field indicates the client IP address.
- If the client accesses the load balancer through a proxy server, the first IP address in the http_x_forwarded_for field indicates the client IP address.
You can search for logs by specific keyword or by time range. For details, see Searching for Logs.
Table 2 Fields in the access log Field
Description
Value Description
remote_addr: remote_port
IP address and port number of the client.
Records the IP address and port of the client.
http_x_forwarded_for
http_x_forwarded_for in the request header received by the load balancer, indicating the request is sent through a proxy server.
Records all the IP addresses along the path through which the request is sent. The first IP address is the client IP address.
Figure 6 Viewing the client IP address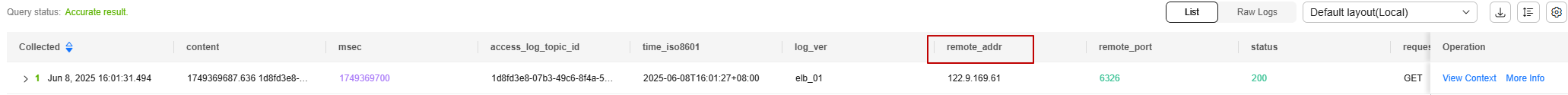
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot