Why Can't I Delete My VPCs and Subnets?
Symptom
VPCs and subnets cannot be deleted.
The VPC service has different resources. Some (such as VPCs and subnets) are free, while some are not. For details about VPC resource pricing, see Pricing Details.
Possible Causes
- VPC:
- The VPC has only subnets that are not in use by other resources, default route tables, and network ACLs. Also, the VPC is not in use by resources, such as subnets that are in use, custom route tables, ECSs, public NAT gateways, private NAT gateways, VPC endpoints, VPC endpoint services, Direct Connect connections, VPC peering connections, VPNs, and enterprise routers.
- If you want to delete the last VPC in a region:
- Delete all custom security groups in the region. The default security group does not affect the deletion of VPCs.
- Release all EIPs in the region.
- Subnet: No IP address in the subnet is being used by other resources, such as virtual IP addresses, elastic network interfaces, supplementary network interfaces, ECSs, SNAT rules of NAT gateways, VPC endpoints, VPC endpoint services, and load balancers.

If a VPC or subnet cannot be deleted, delete the resources that are using the VPC or subnet as instructed in this section, and try again. If your VPC or subnet still cannot be deleted, submit a service ticket.
Deleting Resources That Are Using a VPC or Subnet
- If a VPC or subnet cannot be deleted, record the ID of the resource in the VPC or subnet, and go to the resource console to delete the resource as prompted. Then, delete the VPC or subnet again.
- VPC: Delete the resources that may use a VPC by referring to Table 1.
When you delete a VPC, the console may display a message indicating that this is the last VPC in this region and there are custom security groups in this VPC. The system will prompt you to delete the custom security groups. You need to record the security group IDs to delete them.
Figure 1 Deleting a VPC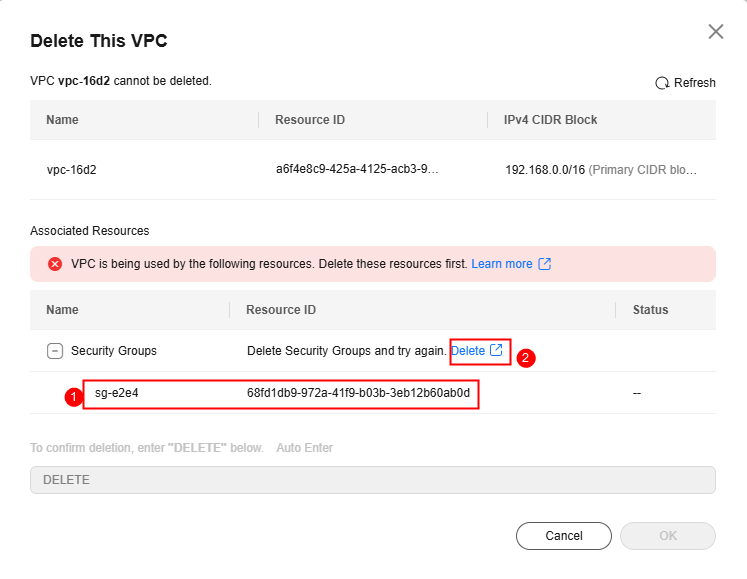
- Subnet: Delete the resources that may use a subnet by referring to Table 2.
When you delete a subnet, if a message is displayed indicating that the subnet is being used by a cloud server, you need to go to the cloud server console through the link and locate the target cloud server by resource ID.Figure 2 Deleting a subnet
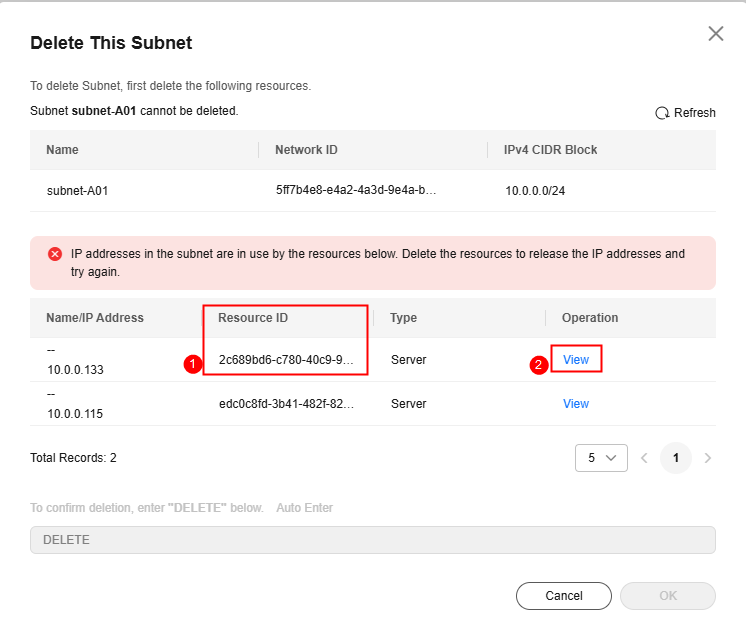
Table 1 Deleting resources in a VPC Resource
Deletion Method
Security group
On the VPC security group console, locate the target custom security group and delete it.
EIP
On the EIP console, locate the target EIP and release it.
Custom route table
On the VPC route table console, locate the target custom route table and delete it.
ECS
On the ECS console, locate the target ECS and delete it.
Public NAT gateway
On the public NAT gateway console, locate the target public NAT gateway and delete it.
Private NAT gateway
On the private NAT gateway console, locate the target private NAT gateway and delete it.
VPC endpoint
On the VPC endpoint console, locate the target VPC endpoint and delete it.
VPC endpoint service
On the VPC endpoint service console, locate the target VPC endpoint service and delete it.
Direct Connect virtual gateway
On the Direct Connect console, locate the virtual gateway and delete it.
VPN gateway
On the VPN console, locate the VPN gateway and delete it.
VPC peering connection
On the VPC peering connection console, locate the target VPC peering connection and delete it.
Enterprise router
On the enterprise router console, locate the target VPC attachment and delete it.
Table 2 Deleting resources in a subnet Resource
Deletion Method
Virtual IP address
On the VPC console, locate the target virtual IP address and release it.
Elastic network interface
On the VPC subnet details page, locate the target elastic network interface and delete it.
Supplementary network interface
On the VPC supplementary network interface console, locate the target supplementary network interface and delete it.
Cloud server
The cloud server may be an ECS or BMS. You need to locate the cloud server that uses the subnet on the VPC subnet details page and delete it.
SNAT rule of a public NAT gateway
On the public NAT gateway console, locate the target public NAT gateway and delete the SNAT rule.
SNAT rule of a private NAT gateway
On the private NAT gateway console, locate the target private NAT gateway and delete the SNAT rule.
VPC endpoint
On the VPC endpoint console, locate the target VPC endpoint and delete it.
VPC endpoint service
On the VPC endpoint service console, locate the target VPC endpoint service and delete it.
Load balancer
On the VPC subnet details page, locate the target load balancer and delete it.
- VPC: Delete the resources that may use a VPC by referring to Table 1.
- If you cannot be redirected to the target resource, use the resource ID to view and search for the target resource on the resource overview page. For details, see Searching for Cloud Resources.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.