Fast-Adding Security Group Rules
Scenarios
The fast-adding rule function of security groups allows you to quickly add rules with common ports and protocols for remote login, ping tests, common web services, and database services.
For details about common ports used by cloud servers, see Common ECS Ports.
Procedure
- Go to the security group list page.
- Locate the row that contains the target security group and click Manage Rules in the Operation column.
The page for configuring security group rules is displayed.
- On the Inbound Rules tab, click Fast-Add Rule.
The Fast-Add Inbound Rule dialog box is displayed.
- Configure required parameters.
Figure 1 Fast-Add Inbound Rule
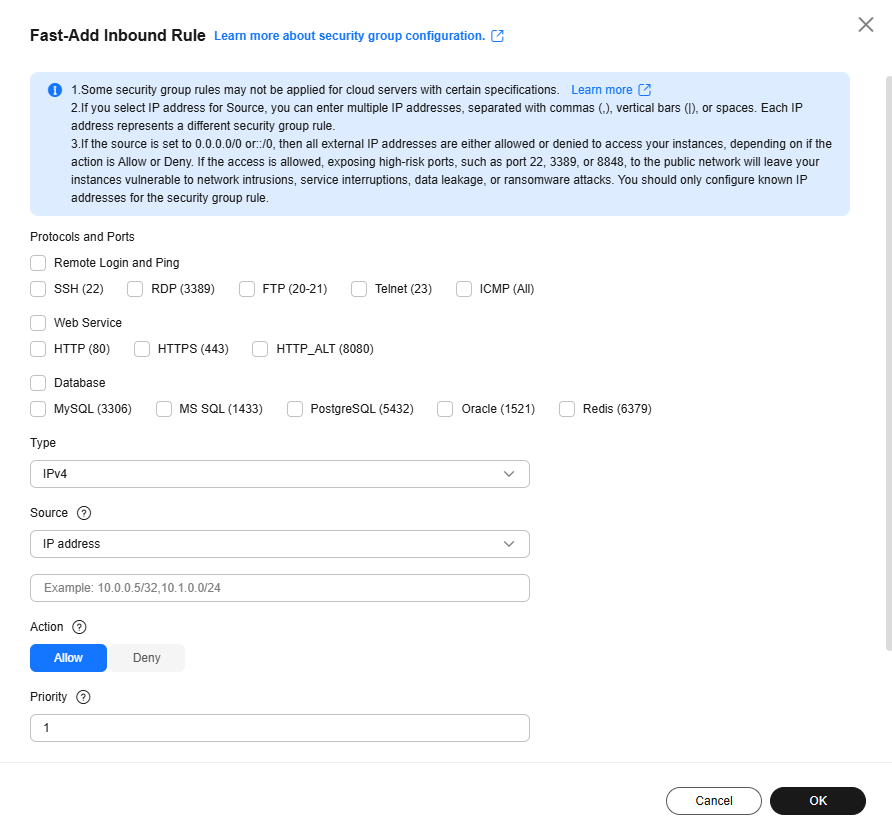
Table 1 Inbound rule parameter description Parameter
Description
Example Value
Protocols and Ports
Common protocols and ports are provided for:
- Remote login and ping
- Web services
- Databases
SSH (22)
Type
Source IP address version. You can select:- IPv4
- IPv6
IPv4
Source
Source of the security group rule. The value can be a single IP address or a security group to allow access from the IP addresses or the instances in the security group. You can specify:- Single IP address: 192.168.10.10/32 (IPv4); 2002:50::44/127 (IPv6)
- IP address range: 192.168.1.0/24 (IPv4); 2407:c080:802:469::/64 (IPv6)
- All IP addresses: 0.0.0.0/0 (IPv4); ::/0 (IPv6)
- Security group: sg-abc
If the source is a security group, this rule will apply to all instances associated with the selected security group.
192.168.0.0/24
Action
The value can be Allow or Deny.- If the Action is set to Allow, traffic is allowed to access the cloud servers in the security group over specified ports.
- If the Action is set to Deny, traffic is denied to access the cloud servers in the security group over specified ports.
Security group rules are matched by priority and then by action. Deny rules take precedence over allow rules. For more information, see How Traffic Matches Security Group Rules.
Allow
Priority
Security group rule priority.
The priority value is from 1 to 100. The default value is 1 and has the highest priority. The security group rule with a smaller value has a higher priority.
1
Description
(Optional) Supplementary information about the security group rule.
The description can contain a maximum of 255 characters and cannot contain angle brackets (< or >).
-
- Click OK.
The inbound rule list is displayed and you can view your added rule.
- On the Outbound Rules tab, click Fast-Add Rule.
The Fast-Add Outbound Rule dialog box is displayed.
- Configure required parameters.
Figure 2 Fast-Add Outbound Rule
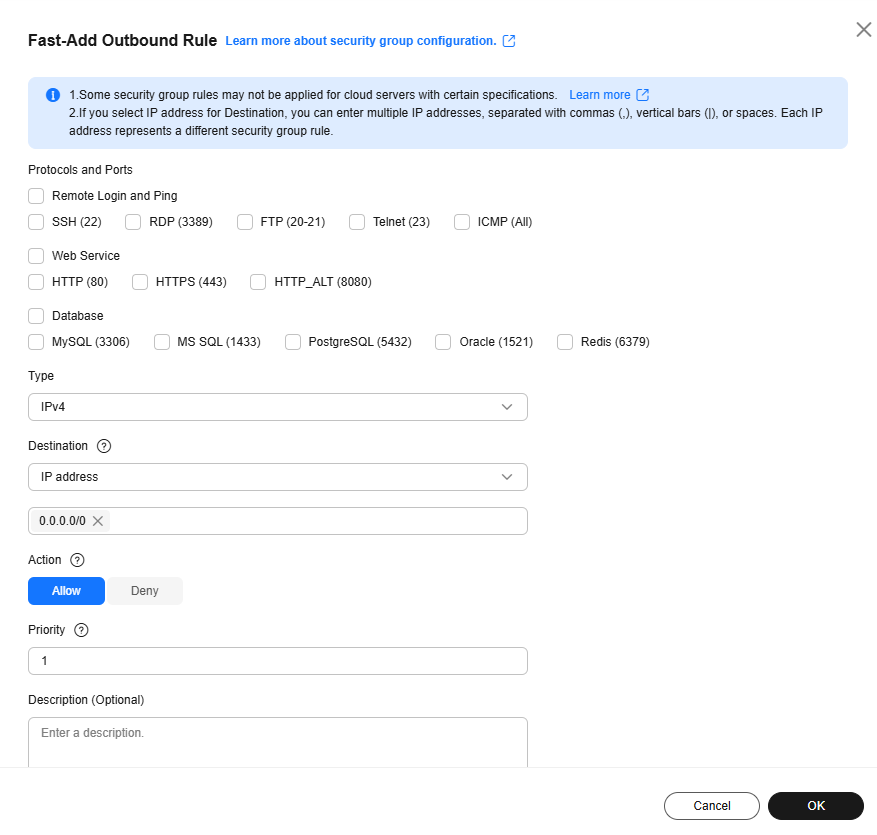
Table 2 Outbound rule parameter description Parameter
Description
Example Value
Protocols and Ports
Common protocols and ports are provided for:
- Remote login and ping
- Web services
- Databases
SSH (22)
Type
Source IP address version. You can select:- IPv4
- IPv6
IPv4
Destination
Destination of the security group rule. The value can be a single IP address or a security group to allow access to the IP addresses or the instances in the security group. You can specify:- xxx.xxx.xxx.xxx/32 (IPv4 address)
- xxx.xxx.xxx.0/24 (IPv4 address range)
- 0.0.0.0/0 (all IPv4 addresses)
- sg-abc (security group)
- Single IP address: 192.168.10.10/32 (IPv4); 2002:50::44/127 (IPv6)
- IP address range: 192.168.1.0/24 (IPv4); 2407:c080:802:469::/64 (IPv6)
- All IP addresses: 0.0.0.0/0 (IPv4); ::/0 (IPv6)
- Security group: sg-abc
0.0.0.0/0
Priority
Security group rule priority.
The priority value is from 1 to 100. The default value is 1 and has the highest priority. The security group rule with a smaller value has a higher priority.
1
Action
The value can be Allow or Deny.- If the Action is set to Allow, access from ECSs in the security group is allowed to the destination over specified ports.
- If the Action is set to Deny, access from ECSs in the security group is denied to the destination over specified ports.
Security group rules are matched by priority and then by action. Deny rules take precedence over allow rules. For more information, see How Traffic Matches Security Group Rules.
Allow
Description
(Optional) Supplementary information about the security group rule.
The description can contain a maximum of 255 characters and cannot contain angle brackets (< or >).
-
- Click OK.
The outbound rule list is displayed and you can view your added rule.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.






