Configuring Kafka Public Access
To access a Kafka instance over a public network, enable public access and configure EIPs for the instance. If you no longer need public access to the instance, you can disable it as required.
Notes and Constraints
Kafka instances only support IPv4 EIPs. IPv6 EIPs are not supported.
Prerequisites
- You can change the public access setting only when the Kafka instance is in the Running state.
Enabling Public IPv4 Access
- Log in to the Kafka console.
- Click
 in the upper left corner to select the region where your instance is located.
in the upper left corner to select the region where your instance is located. - Click the name of a Kafka instance to go to the Basic Information page.
- Click
 next to Public Access to enable public access. For Elastic IP Address, select an EIP for each broker.
next to Public Access to enable public access. For Elastic IP Address, select an EIP for each broker.
If the EIPs are insufficient, do as follows to set them.
- Click Create Elastic IP to go to the Buy EIP page and purchase EIPs. For details, see Assigning an EIP.
- After the purchase is complete, return to the public access enabling page.
- Click
 after Elastic IP Address, select an EIP for each broker and then click
after Elastic IP Address, select an EIP for each broker and then click  . The Background Tasks page is displayed.
. The Background Tasks page is displayed. - If the status of the task turns to Successful, public access is successfully enabled.
Figure 1 Enabling public access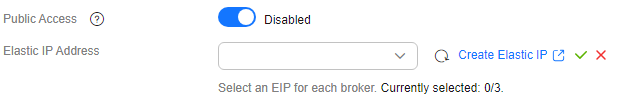
After public access is enabled, configure the access mode (plaintext or ciphertext) and security group rules listed in Table 1 before attempting to access Kafka. For details about accessing Kafka, see Connecting to an Instance.
Table 1 Kafka instance security group rules (public IPv4 access) Direction
Protocol
Type
Port
Source
Description
Inbound
TCP
IPv4
9094
IP address or IP address group of the Kafka client
Public plaintext access to Kafka
Inbound
TCP
IPv4
9095
IP address or IP address group of the Kafka client
Public ciphertext access to Kafka
Disabling Public IPv4 Access
- Log in to the Kafka console.
- Click
 in the upper left corner to select the region where your instance is located.
in the upper left corner to select the region where your instance is located. - Click the name of a Kafka instance to go to the Basic Information page.
- Before disabling public access, disable Plaintext Access and Ciphertext Access next to Public Network Access. Then click
 next to Public Access.
next to Public Access. - Click OK. The Background Tasks page is displayed. If the status of the task turns to Successful, public access is successfully disabled.
After public access is disabled, configure security group rules listed in Table 2 before attempting to access Kafka in a VPC. For details about accessing Kafka, see Connecting to an Instance.
After a security group is created, its default inbound rule allows communication among ECSs within the security group and its default outbound rule allows all outbound traffic. In this case, you can access a Kafka instance within a VPC, and do not need to add rules according to Table 2.
Table 2 Kafka instance security group rules (private access) Direction
Protocol
Type
Port
Source
Description
Inbound
TCP
IPv4
9092
IP address or IP address group of the Kafka client
Accessing a Kafka instance over a private network within a VPC (in plaintext)
Inbound
TCP
IPv4
9093
IP address or IP address group of the Kafka client
Accessing a Kafka instance over a private network within a VPC (in ciphertext)
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.






