Using an SSH Client to Log In to Resources for O&M
You can use an SSH client to log in to managed resources via a bastion host. You do not have to change your habits of using an SSH client. Through SSH client, the command rules and operation audit function are still available.
This topic uses Xshell as an example to describe how to use an SSH client to log in to a resource for O&M and how to download the configuration file of the resource.
Constraints
- Logging using an SSH client is used only for hosts using the SSH, Telnet, or Rlogin protocol. For hosts using the Rlogin protocol, only an SSH client can be used for logins.
- Supported SSH clients include SecureCRT 8.0 or later, Xshell 5 or later, PuTTY, and MAC Terminal 2.0 or later.
- The following table lists the servers supported by different algorithm types in different scenarios.
Table 1 Servers supporting SSH O&M Algorithm Type
HTML5 (H5) O&M
SSH Client
Key exchange
- diffie-hellman-group-exchange-sha256
- diffie-hellman-group-exchange-sha1
- diffie-hellman-group14-sha1
- diffie-hellman-group1-sha1
- ecdh-sha2-nistp256
- ecdh-sha2-nistp384
- ecdh-sha2-nistp521
- curve25519-sha256
- curve25519-sha256@libssh.org
- diffie-hellman-group14-sha256
- diffie-hellman-group-exchange-sha256
- diffie-hellman-group-exchange-sha1
- diffie-hellman-group14-sha1
- diffie-hellman-group1-sha1
- ecdh-sha2-nistp521
- ecdh-sha2-nistp384
- ecdh-sha2-nistp256
Encryption
- aes128-ctr
- aes192-ctr
- aes256-ctr
- aes128-cbc
- aes192-cbc
- aes256-cbc
- 3des-cbc
- blowfish-cbc
- arcfour128
- arcfour
- cast128-cbc
- 3des-cbc
- rijndael-cbc@lysator.liu.se
- aes128-ctr
- aes192-ctr
- aes256-ctr
- aes128-cbc
- aes192-cbc
- aes256-cbc
- 3des-cbc
- blowfish-cbc
- arcfour128
- arcfour256
HMAC
- hmac-md5
- hmac-md5-96
- hmac-sha1
- hmac-sha1-96
- hmac-sha2-256
- hmac-sha2-512
- hmac-ripemd160
- hmac-ripemd160@openssh.com
- hmac-md5
- hmac-md5-96
- hmac-sha1
- hmac-sha1-96
- hmac-sha2-256
- hmac-sha2-512
Host Key
- ssh-rsa
- ssh-dss
- ecdsa-sha2-nistp256
- ecdsa-sha2-nistp384
- ecdsa-sha2-nistp521
- ssh-ed25519
- ssh-rsa
- ssh-dss
- rsa-sha2-256
- rsa-sha2-512
- ecdsa-sha2-nistp256
- ecdsa-sha2-nistp384
- ecdsa-sha2-nistp521
Prerequisites
- You have the management permissions for the Host Operations module.
- You have obtained the access permissions for the resources.
- You have installed the client tool.
- The network connection between the managed host and the system is normal, and the account username and password for logging in to the managed host are correct.
Procedure
- Start the local client tool Xshell and choose File > New to create a user session.
- Configure session connections.
- Method 1
- Set Protocol Type to SSH, enter the elastic IP address of your bastion host, set Port to 2222, and click OK.
- Enter the username of your bastion host and click Connect.
- Method 2:
In the newly opened blank session window, run a command in the following format: Protocol type User login name@System login IP address Port number, for example, ssh admin@10.10.10.10 2222.
- Method 3
In the live session window of a Linux host, run a command in the following format: Protocol type User login name@System login IP address-p Port number, for example, ssh admin@10.10.10.10 -p 2222.
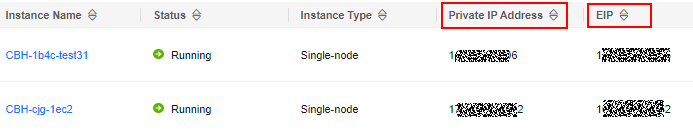
system login IP address indicates the private IP address or EIP of your bastion host. Make sure the network connection between the local PC and the IP address is normal.
- Method 1
- Verify user identity.
- Select Password, enter your password, and click OK.
- Select Public Key, upload the private key file that matches the SSH public key added to the bastion host in the user key area, select the target private key, and click OK.
After the authentication is successful, the user can use the SSH client to log in to the bastion host without having to enter a password.
- Log in to your bastion host.
If an SSH client is used, password, SMS message, mobile token, and OTP can be used for login identity authentication. To use mobile SMS message, mobile OTP, and OTP authentication methods, configure multifactor verification. For details, see Configuring User Login Restrictions.
- Mobile SMS: After logging in to the system using the local password, select Mobile SMS for Multifactor Verification, and enter the SMS verification code.
- Mobile OTP: After logging in to the system using the local password, select Mobile OTP and enter the dynamic password of the mobile phone token.
- One-Time password: After logging in to the bastion host using the local password, select OTP and enter the dynamic token verification code.
- Import accounts of a managed host.
Decompress the configuration file package, open the readme.txt file, and import the resource account. For details about how to download the package, see Downloading Host Configuration File.
- Log in to the managed host using an account.
Select the account to be used for logging, enter the password of the system user, and log in to the host for O&M.
Downloading Host Configuration File
To import host resources in batches using the SSH client, download the configuration files of the hosts to be imported.
- Log in to your bastion host using a web browser.
- Choose Operation > Host Operations to go to the Host Operations page.
- Click Export Host Configuration.
- Select the configuration file of the client and click OK to download the configuration file.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.






