Creating a Login User and Associating a Role with the User
A user in a CBH system represents a natural person who can log in to the CBH system. You can create users in your CBH system, batch import users from other platforms into your CBH system, and synchronize users from an Active Directory (AD) server to your CBH system. All those users then can log in to your CBH system.
The admin user has the highest permissions for the corresponding bastion host. It is also the first user who can log in to the bastion host. This means all other system users are created by user admin.
Constraints
To set Department to a superior department for a user, you must have management permissions for the Department module. For details about how to edit the role permissions of a user, see Editing Role Information.
Prerequisites
- You have obtained the permissions to create or import users on the User module.
- You have obtained the permissions to synchronize users from the AD domain server to the System module.
Creating a User
- Log in to your bastion host.
- In the navigation pane on the left, choose User > User to go to the user list page.
- In the upper right corner of the page, click New. In the displayed New User dialog box, complete required parameters.
Figure 1 New User
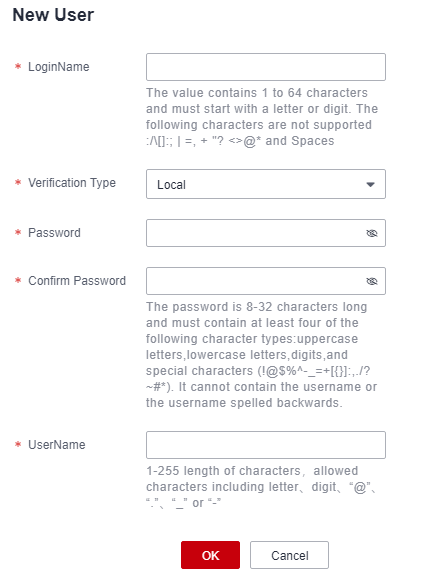
Table 1 Parameters for creating a user Parameter
Description
LoginName
Specifies the username for logging in to the system.
The LoginName must be unique in a system and cannot be changed once created.
Verification Type
Specifies how the user is verified for logging in to the bastion host.
- Local: The user is verified against the account management system of the bastion host. This method is the default method.
- AD: The user is verified against the Windows AD domain server.
- LDAP: The user is verified against the third-party authentication server through the LDAP protocol.
- RADIUS: The user is verified against the third-party authentication server through the RADIUS protocol.
- Azure AD: The user is verified against the Azure platform based on Security Assertion Markup Language (SAML) configuration.
NOTE:
If you want to verify the user against a remote AD domain, LDAP, or RADIUS servers or verify the user against the Azure AD service, configure the remote authentication server in the bastion host. For details, see Authentication Configuration.
Domain name
This parameter is mandatory if you select Azure AD for Verification Type.
Provide the suffix you registered with the Azure platform.
Password/Confirm Password
A password must be configured for the user to log in to the bastion host if you select Local for Verification Type.
UserName
Specifies the user-defined user name.
This name indicates the name of the person who uses the account so that system users can be distinguished from each other.
Mobile
Specifies the mobile number of the user.
This number is used for SMS authentication logins and password resetting.
Email
Specifies the email address of the user.
The bastion host sends notifications to this email address.
Role
Specifies the role to be assigned to the user. Only one role can be assigned.
By default, system roles include DepartmentManager, PolicyManager, AuditManager, and User.
- DepartmentManager: responsible for managing departments. Except the User and Role modules, this role has the configuration permissions for all other modules.
- PolicyManager: responsible for configuring policy permissions. This role has the configuration permissions for the User Group, Account Group, and ACL Rules modules.
- AuditManager: responsible for auditing system and maintenance data. This role has the configuration permission for Live Session, History Session, and System Log modules.
- User: common system users and resource operators. This role has the permissions for the Host Operations, App Operations, and Ticket approval modules.
- User-defined role: Only the admin user can customize a new role or edit permissions of a default role.
Department Name
Specifies the department to which the user belongs. For details about how to create a department, see Creating a Department.
Remarks
(Optional) Provides supplementary information about the user.
- Click OK. You can then view the new system user on the user list page.
Batch Importing Users
- Log in to your bastion host.
- In the navigation pane on the left, choose User > User to go to the user list page.
- Click
 in the upper right corner.
in the upper right corner. - Click Download next to Download template.
- Enter the information of users according to the configuration requirements in the template.
Table 2 Template parameters Parameter
Description
LoginName
(Mandatory) Specifies the username for the user to log in to the bastion host.
Verification Type
(Mandatory) Specifies the authentication method. Only one authentication method can be entered.
You can select Local, RADIUS, AD Domain, LDAP, Azure AD, or IAM.
Password
(Mandatory) Specifies the user-defined login password. This parameter is required when Verification Type is set to Local.
Authentication server/Domain name
(Mandatory) Specifies the authentication server. This parameter is required if Verification Type is set to AD, LDAP, or Azure AD. Note that the value must be entered in required format.
- For AD domain authentication, the value must be in the format of IP:PORT, for example, 10.10.10.10:389.
- For LDAP authentication, the value must be in the format of IP:'PORT/ou=test,dc=test,dc=com', for example, 10.10.10.10:'389/ou=test,dc=com'.
- For Azure AD authentication, provide the domain name.
UserName
Enter the name of a system user.
Mobile
Enter the mobile number of a system user.
Email
Enter the email address of the system user.
Role
(Mandatory) Enter the system role of the user.
- Only one role type can be entered.
- There are four default roles for your choice: DepartmentManager, PolicyManager, AuditManager, and User.
- Only the role that has been created in the system can be entered.
Department Name
(Mandatory) Enter the department to which the user belongs. The department structure must be complete.
- Only one department structure can be entered, and a user can belong to only one department.
- By default, the department can be set to HQ. Use a comma (,) to separate a department and its lower-level department.
- Only the department that has been created in the system can be entered.
Remarks
Provides supplementary information about the user account.
User Groups
Specifies the user group that a user belongs to.
- A user account can belong to multiple user groups in the same department. Use a comma (,) to separate every two user groups.
- Only the user group that has been created in the system can be entered.
- Click Upload and select the completed template file.
- (Optional) Select Override existing user.
- Selected: If an existing user account and the user account being imported have the same LoginName, the existing one will be overwritten. The user account information in the bastion host is updated accordingly.
- Deselected: If an existing user account and the user account being imported have the same LoginName, the existing one will be skipped and kept unchanged.
- Click OK. You can then view the new system user on the user list page.
Synchronizing AD Domain Users
You can configure Sync Mode for the AD authentication to let the system synchronize existing user information on the AD domain server to your bastion host. When a user logs in to the bastion host, the AD domain server provides the identity authentication service.
- Log in to your bastion host.
- Choose System > System Config > Authenticate.
- Click Add in the AD Settings area.
- Set the AD domain authentication Mode to Sync Mode.
Table 3 AD settings for synchronizing users Parameter
Description
Server
Specifies the IP address of the AD domain server.
Status
Specifies whether to enable AD domain remote authentication. AD domain remote authentication is enabled by default.
- Enabled: AD domain authentication is enabled. If the configuration information is valid, AD domain authentication is enabled or AD domain users are synchronized to the bastion host when the user performs a login.
- Disabled: AD domain authentication is disabled.
SSL
Specifies whether to enable SSL encryption. SSL encryption is disabled by default.
- Disabled: SSL encryption is disabled.
- After SSL encryption is enabled, data transmitted by synchronized users or authenticated users is encrypted.
Mode
Specifies the working mode of AD domain. Select Sync Mode.
Port
Specifies the access port of the remote server of AD domain. The default port number is 389.
LoginName
Specifies the username of the account for logging in to the AD domain server.
Password
Specifies the password of the account for logging in to the AD domain server.
Domain
Specifies the domain of the AD service.
Base DN
Specifies the base DN for the remote AD domain server.
Dept Filter
Specifies the departments to be filtered out for the remote AD domain server.
User Filter
Specifies the users to be filtered out for the remote AD domain server.
Login Name Filter
Specifies the login name to be filtered out. Separate multiple login names with vertical bars (|).
UserName
Specifies the attribute name of user names on the remote AD domain server, for example, name.
Email
Specifies the attribute name of the user mailbox on the AD domain remote server, for example, mail.
Mobile
Specifies the attribute name of user's mobile phone on the AD domain remote server, for example, mobile.
Sync
Specifies the AD user synchronization method. The options include Manual and Auto.
- Manual: After you complete required configurations, manually synchronize the user information from the AD server.
- Auto: After you complete required configurations, user information is automatically synchronized. You are also required to configure Start time of sync, Duration, and End time for auto synchronization.
Department
Specifies the department to which the synchronized user account belongs.
Options
- Override existing
- Selected: If an existing user account and the user account being imported have the same LoginName, the existing one will be overwritten. The user account information in the bastion host is updated accordingly.
- Deselected: If an existing user account and the user account being imported have the same LoginName, the existing one will be skipped and kept unchanged.
- Sync user status: If you select this, the current user status will be synchronized to the bastion host. This option is recommended.
- (Optional) If you want to synchronize users from the AD domain server, click Next to obtain the source department structure of the AD domain server.
- Sync All Users is enabled by default.
- If you select a superior department of the user source, all users in the lower-level department are included in the source.
- Create new dept is disabled by default. You can enable it to let system create departments based on the department structure in the AD domain and synchronize users from the AD domain departments.
- Click OK. You can then view AD authentication configurations in the AD server list.
- In the AD Settings area, locate the AD server row. In the Operation column, click Start to synchronize AD domain users to a bastion host. You can view the synchronized user information in the user list.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.






