Cloud Service Delegation
Huawei Cloud services interwork with each other, and some cloud services are dependent on other services. To delegate a cloud service to access other services and perform resource O&M, create a trust agency for the service. For details about the cloud services that support trust agencies, see Cloud Services for Using Identity Policies and Trust Agencies.
IAM provides two methods to create a trust agency:
- Creating a cloud service trust agency on the IAM console
You need to create a cloud service trust agency for some services on the IAM console and then configure the trust agency for the cloud service.
- Automatically creating (not for all cloud services) a trust agency to use certain resources
The following uses Resource Governance Center (RGC) as an example:
- Click Enable on the RGC console to set up a landing zone.
- During the setup, the system automatically creates a trust agency RGCAdminAgency and grants the RGCServiceAgencyPolicy system-defined policy to it. After enabling API is responded, RGC assumes the trust agency and you can create an organization account and RFS stack set.
- You can view the created trust agency in the agency list on the IAM console.
Creating a Cloud Service Trust Agency on the IAM Console
- Log in to the new IAM console.
- On the IAM console, choose Agencies from the navigation pane, and click Create Trust Agency.
- Enter an agency name.
Figure 1 Name of a cloud service trust agency
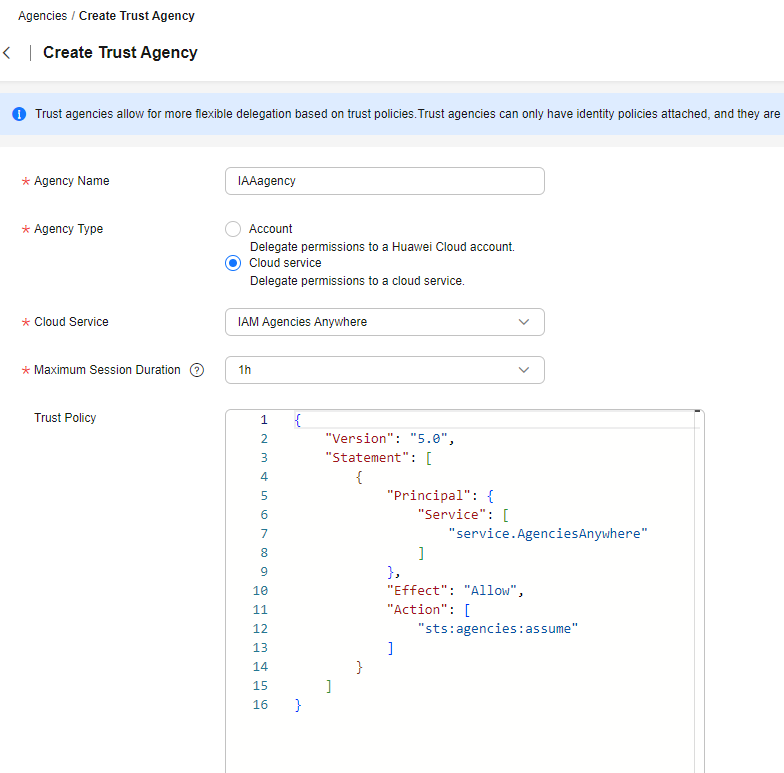
- Select the Cloud service agency type, and then select a cloud service.
- Specify Maximum Session Duration to configure the maximum session duration of the temporary access credentials obtained by programmatic access.
- Edit the trust agency by referring to Deleting or Modifying an Agency (by a Delegated Party).
- (Optional) Enter a description for the trust agency to facilitate identification.
- Click Next.
- Select the permissions to be granted to the trust agency and click OK.
Example Policies
When you delegate another cloud service to manage Huawei Cloud resources, the key is to configure the trust policy and identity policy of the trust agency. This is similar to delegating another account to manage Huawei Cloud resources. Generally, cloud services have specific requirements on identity policies attached to trust agencies based on their own service logic. You can view the relevant documentation of each cloud service for detailed information. The difference between the trust policies of a cloud service trust agency and an account trust agency lies in the "Principal" element. For details about the "Principal" element, see JSON Element Reference.
{
"Version": "5.0",
"Statement": [
{
"Action": [
"sts:agencies:assume"
],
"Effect": "Allow",
"Principal": {
"Service": [
"service.RGC"
]
}
}
]
}
The "Service" element in "Principal" must be set to the service principal of the cloud service. For details about the service principal list, see the "Service Principal" column in Cloud Services for Using Identity Policies and Trust Agencies.
If the cloud service switches the trust agency, the source_identity parameter of the source identity information and the tags parameter of the session tag must be passed. You need to include the sts::setSourceIdentity and sts::tagSession permissions in the trust policy.
When a cloud service manages resources for you, it requires you to add necessary permissions to the trust agency. For example, RGC uses the trust agency to create organization accounts and RFS stack sets. For convenience, the required permissions have been registered as the system-defined identity policy RGCServiceAgencyPolicy. You can search and check the policy on the identity policy list of the new IAM console.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot





