Switching the Role (by a Delegated Party)
When another account establishes a trust agency relationship with your account, you become a delegated party. The root user of your account and all the users you have authorized can switch to the role of the delegating account and manage resources under this account based on assigned permissions.
Prerequisites
- An account has established a trust agency relationship with your account.
- You have obtained the name of the delegating account and the trust agency name.
Procedure
- Log in to the Huawei Cloud console using your account or the IAM user created in 2.
- Move the cursor to the username in the upper right corner and choose Switch Role > Switch to Another Role.
Figure 1 Switching the role
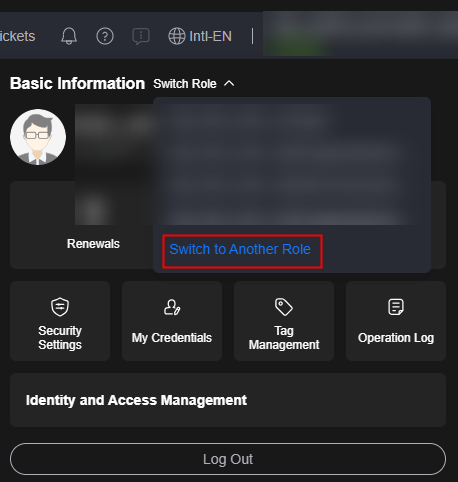
- On the Switch Role page, enter the account name of the delegating party.
Figure 2 Specifying the account name and trust agency name of the delegating account
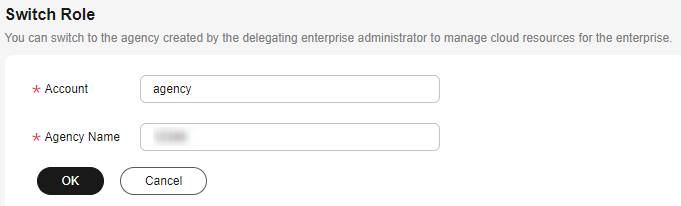

If you enter a name of an unauthorized agency, the system displays a message indicating insufficient permissions.
- Click OK to switch to the delegating account.
Follow-Up Procedure
To return to your account, hover over the username in the upper right corner, choose Switch Role, and select your account.
Differences Between Switching an Agency on the Console and Using an API
|
Method |
Operator |
Credential Validity Period |
|---|---|---|
|
Console |
Account root users and IAM users |
After you switch an agency on the console, the credentials will be automatically renewed. You only need to focus on the session validity period because it is subjective to the session timeout policy of the delegating account. For example, if the session timeout policy set for the delegating account is that a user will be logged out if no operation is performed within 1 hour, the user will be logged out forcibly if no operation is performed within 1 hour after you switch an agency. |
|
AssumeAgency API |
Account root users, IAM users, and trust agencies |
When you use the AssumeAgency API to switch to a trust agency, you will obtain a temporary security credential. The validity period of the credential is determined by the duration_seconds parameter of the API, the maximum session duration set for the trust agency, and whether the API is called for an agency chain. The value of duration_seconds ranges from 900 to 43200 seconds. The default value is 3600 seconds. The value must be less than the maximum session duration of the trust agency. Otherwise, an error will be reported. The value of duration_seconds cannot exceed 3600 seconds if the agency chain is used. |

Using an agency chain means that you call the AssumeAgency API as the root user or an IAM user to obtain temporary security credentials of a trust agency, and then use that temporary security credentials to call the API again to obtain temporary security credentials of another trust agency. Temporary security credentials contain a temporary AK/SK and a session token (AK/SK/SecurityToken). When temporary security credentials are used to call the AssumeAgency API, the X-Security-Token header is passed, which is not passed when the permanent AK/SK of an account root user or IAM user is used. For more information about temporary security credentials, see Obtaining Temporary Security Credentials.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot





