Configuring Security Group Rules for a FlexusL Instance
Scenarios
A security group is a collection of access control rules and consists of inbound and outbound rules. You can add security group rules to allow or deny the traffic to reach and leave the FlexusL instances in the security group.
Security group rules allow or deny network traffic from specific sources over specific protocols or specific ports.
- For details about configuration examples, see Security Group Examples.
- For details about how to configure security group rules for FlexusL application images, see Configuring Security Groups for FlexusL Application Images.
Precautions
- Before configuring security group rules, you need to plan rules for communications among instances in the security group.
- Add as fewer rules as possible. For details about the constraints on the number of rules in a security group, see Notes and Constraints.
- After allowing traffic over a port in a security group rule, ensure that the port is opened in the instance. For details, see Verifying Security Group Rules.
- Generally, all FlexusL instances created by the same account in the same region are in the same security group and they can communicate with each other by default.
Procedure
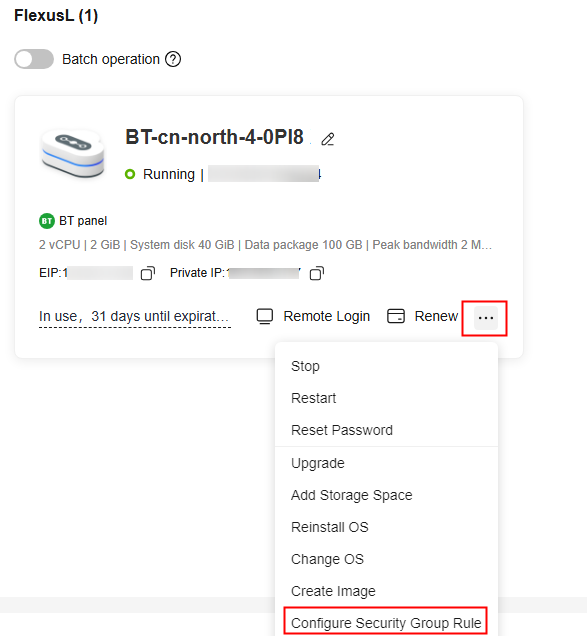
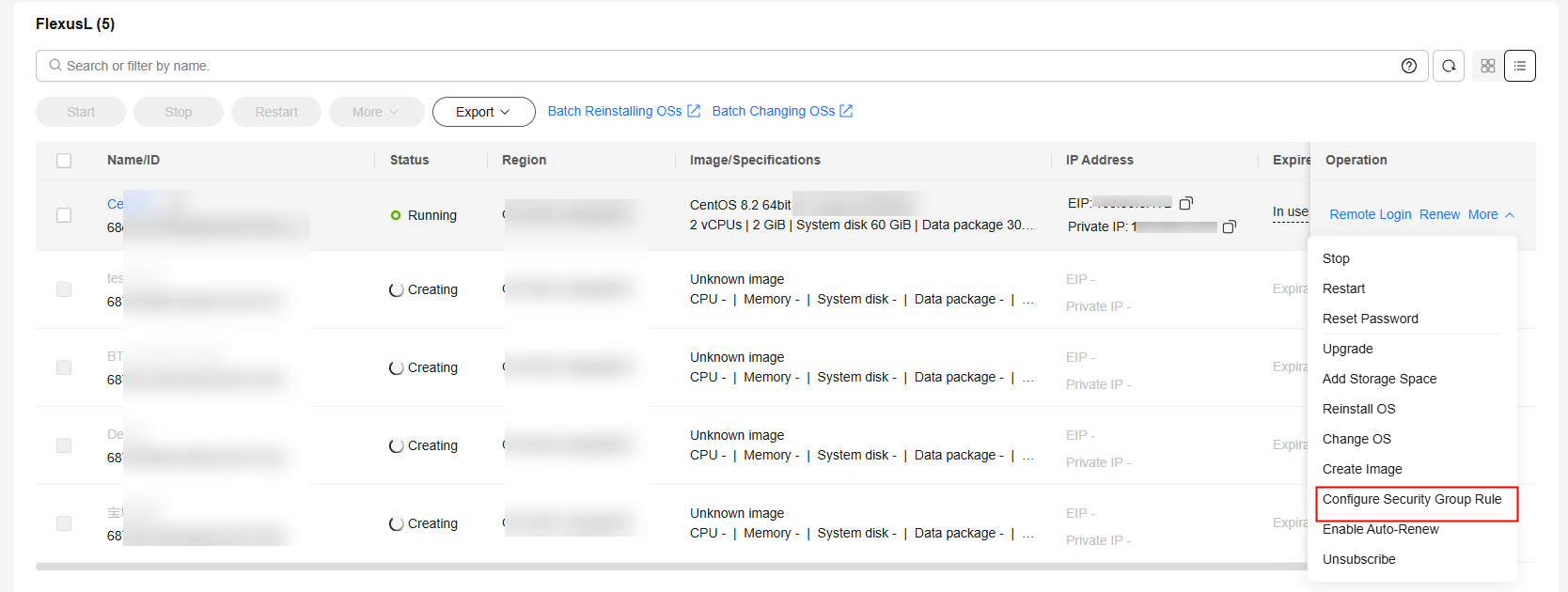
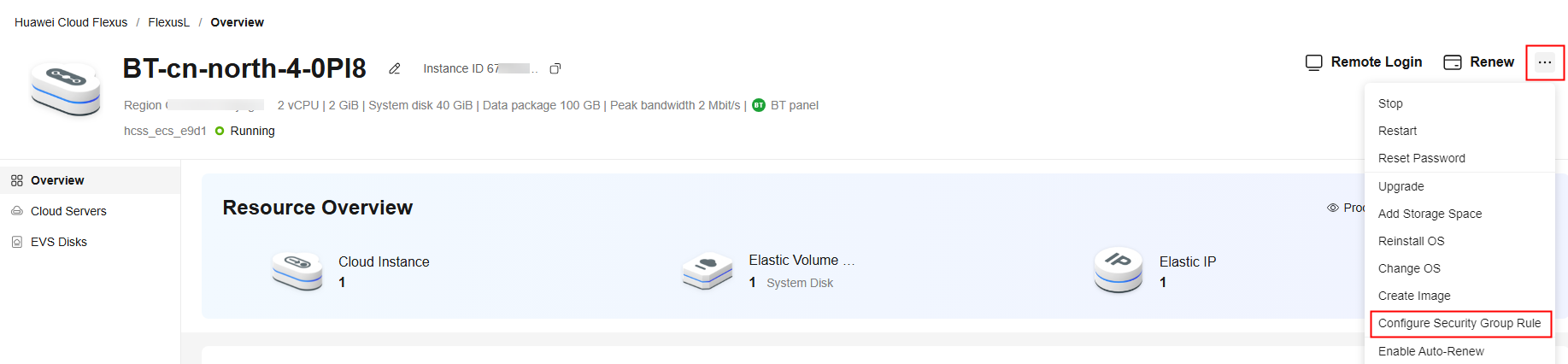
- Log in to the FlexusL console.
By default, FlexusL instances are displayed in the card view. You can also click
 to switch to the list view.
to switch to the list view. - Configure security group rules using any of the following methods:
- Select Inbound rules from the drop-down list and click Add Rule.
You can click + to add more inbound rules. For details about the parameters, see Adding a Security Group Rule.
Figure 4 Adding an inbound rule
- Select Outbound rules from the drop-down list and click Add Rule.
You can click + to add more outbound rules. For details about the parameters, see Adding a Security Group Rule.
- Click OK.
After allowing traffic over a port in a security group rule, ensure that the port is opened in the instance. For details, see Verifying Security Group Rules.
Related Operations
On the Inbound Rules and Outbound Rules tab pages, you can also modify, replicate, or delete existing rules.
Deleting security group rules will disable some functions.
- If you delete a rule with Protocol & Port specified as TCP: 20-21, you will not be able to upload files to or download them from servers using FTP.
- If you delete a rule with Protocol & Port specified as ICMP: All, you will not be able to ping the servers.
- If you delete a rule with Protocol & Port specified as TCP: 443, you will not be able to connect to websites on the servers using HTTPS.
- If you delete a rule with Protocol & Port specified as TCP: 80, you will not be able to connect to websites on servers using HTTP.
- If you delete a rule with Protocol & Port specified as TCP: 22, you will not be able to remotely connect to Linux server using SSH.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot