Why Can't I Ping the EIP After It Is Bound to My Instance?
Fault Location
- Check security group rules.
- Check network ACLs.
- Ping the EIP from a DB instance in the same region.
Solution
- Check security group rules.
- To connect to your DB instance through an EIP, add the EIP and port to an inbound rule of security group sg-default-smb. For details, see Adding a Security Group Rule.
Figure 1 Adding an inbound rule
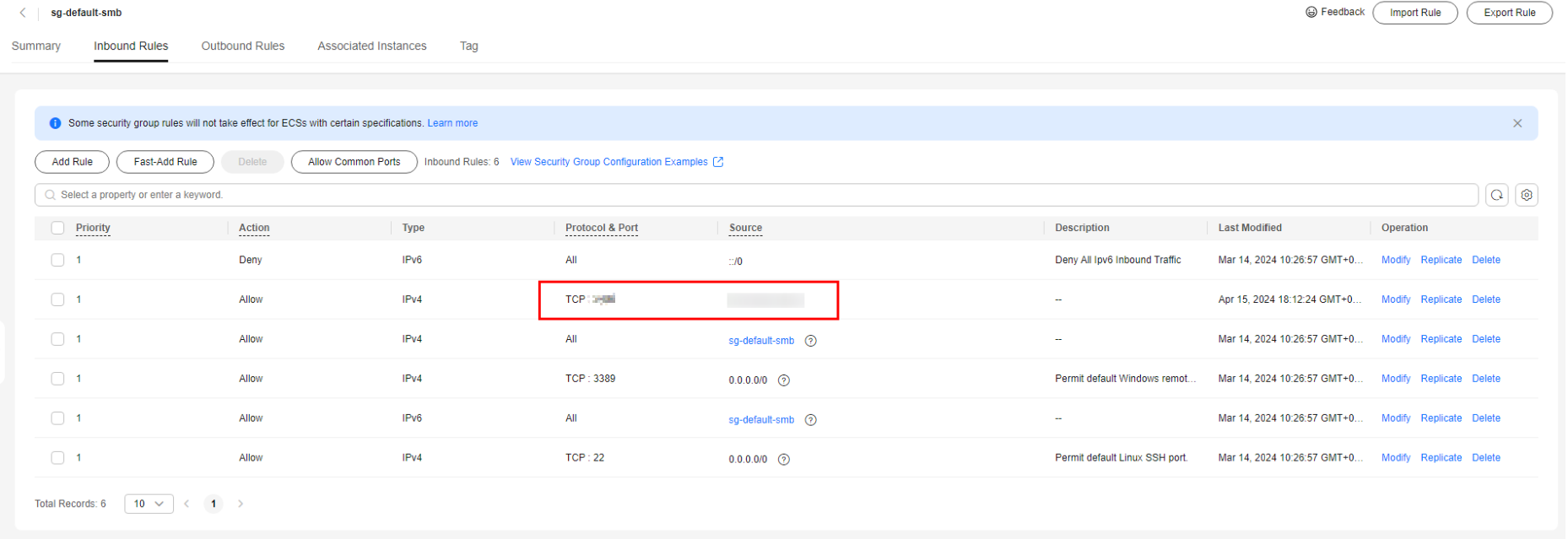
- To connect to your DB instance through an EIP, add the EIP and port to an inbound rule of security group sg-default-smb. For details, see Adding a Security Group Rule.
- Check network ACLs.
- Check the network ACL status.
- Check whether the NIC to which the EIP bound belongs to the subnet associated with the network ACL.
- If the network ACL is enabled, add an ICMP rule to allow traffic.
The default network ACL rule denies all incoming and outgoing packets. If the network ACL is disabled, the default rule still takes effect.
- Ping the EIP from a FlexusX instance in the same region.
Use the FlexusX instance in the same region to ping the EIP. If the EIP can be pinged, the virtual network is normal. Contact customer service.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot





