Monitoring DEW Key Usage Using CTS
DEW provides the key function to help you generate, encrypt, and decrypt data encryption keys (DEKs) to protect sensitive data in cloud services. You can use CTS to monitor DEW key usage, so that you can detect abnormal activities, unauthorized operations, or potential security risks in a timely manner. Effective monitoring and auditing help you better manage and protect DEW keys, meeting data security and compliance requirements.
This section describes how to use the operation audit and trace filtering and querying functions of CTS to monitor DEW key usage.
Preparations
- If you log in to the console using a Huawei Cloud account, go to Enabling CTS and Configuring a System Tracker.
- If you log in to Huawei Cloud as an IAM user, first contact your CTS administrator (account owner or a user in the admin user group) to obtain the CTS FullAccess permission. For details, see Assigning Permissions to an IAM User.
Enabling CTS and Configuring a System Tracker
- Log in to the CTS console.
- In the navigation pane, choose Tracker List.
- Click Enable CTS in the upper right corner. A management tracker named system is automatically created.
- Click Configure in the Operation column in the row of the management tracker (named system).
Figure 1 Configuring the tracker
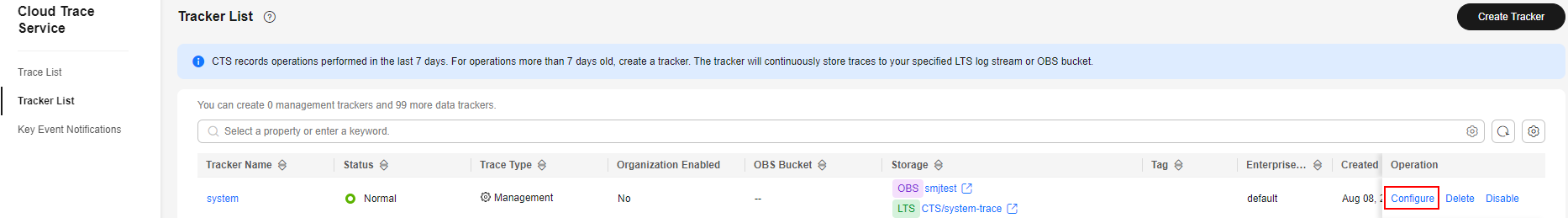
- Configure the basic information of the tracker and click Next.
Parameter
Description
Requirements
Tracker Name
The default value is system and cannot be changed.
system
Enterprise Project
If you have enabled enterprise project management for your account, select an enterprise project.
NOTE:Enterprise projects allow you to manage cloud resources and users by project.
For details about how to enable enterprise projects, see Creating an Enterprise Project.
default
Exclude DEW traces
Deselected by default. If this option is selected, the createDataKey and decryptDatakey operations on DEW will not be transferred to OBS/LTS.
NOTE:For details about DEW audit operations, see Operations supported by CTS.
Deselect
- On the transfer configuration page, you can set the transfer function. You do not need to use the transfer function in this practice. Therefore, disable Transfer to OBS and Transfer to LTS.
- Click Next and Configure to complete the system tracker configurations. You can then check the tracker details on the Tracker List page.
Scenario 1: Querying Records for Creating, Deleting, Enabling, or Disabling DEW Keys
- On the CTS console, choose Trace List in the navigation pane on the left.
- In the upper part of the page, click Last 1 hour to set the query time range.
- Search for DEW key operations in the search box, including creation, deletion, enabling, and disabling.
- Creating a DEW key: Choose Trace Source: DEW > Resource Type: cmk > Trace Name: createKey.

- Deleting a DEW key: Choose Trace Source: DEW > Resource Type: cmk > Trace Name: scheduleKeyDeletion.
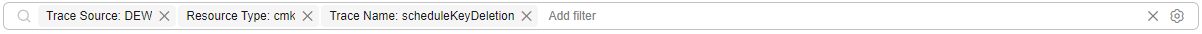
- Enabling a DEW key: Choose Trace Source: DEW > Resource Type: cmk > Trace Name: enableKey.

- Disabling a DEW key: Choose Trace Source: DEW > Resource Type: cmk > Trace Name: disableKey.

- Creating a DEW key: Choose Trace Source: DEW > Resource Type: cmk > Trace Name: createKey.
- Check the query result in the trace list.
Scenario 2: Querying the Usage of Specified DEW Keys
- On the CTS console, choose Trace List in the navigation pane on the left.
- In the upper part of the page, click Last 1 hour to set the query time range.
- Enter the key ID of the specified DEW key to be queried in the search box: Resource ID:{resource_id}.

Replace {resource_id} with the key ID of the DEW key to be queried. In CTS, the resource ID is the key ID of the DEW key.
- Check the query result in the trace list.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot





