Using IAM Roles or Policies to Grant Access to Cloud Eye
You can use IAM for fine-grained permissions control for your Cloud Eye resources. With IAM, you can:
- Create IAM users for employees based on your enterprise's organizational structure. Each IAM user will have their own security credentials for accessing Cloud Eye resources.
- Grant only the minimum permissions required for users to perform a given task.
- Entrust an account of Huawei Cloud or a cloud service to perform efficient O&M on your Cloud Eye resources.
If your Huawei Cloud account does not require individual IAM users, skip this topic.
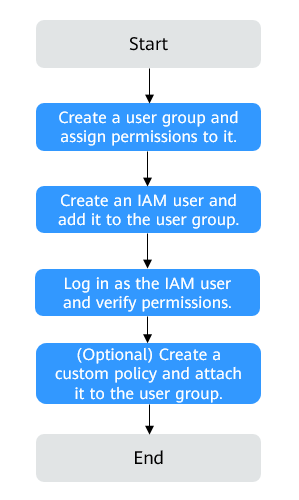
This topic describes the procedure for granting permissions (see Figure 1).
Prerequisites
Before assigning permissions to a user group, you need to understand the Cloud Eye system policies that can be added to the user group and select a policy as required.
For details about the system policies supported by Cloud Eye and comparison between these policies, see Permissions Management. For the permissions of other services, see System Permissions.
Process Flow
- Create a user group and assign permissions
Create a user group on the IAM console, and attach the CES Administrator, Tenant Guest, and Server Administrator policies to the group.
- Cloud Eye is a region-specific service and must be deployed in specific physical regions. Cloud Eye permissions can be assigned and take effect only in specific regions. If you want the permissions to take effect for all regions, assign them in all these regions. The global permission does not take effect.
- The preceding permissions are all Cloud Eye permissions. For more refined Cloud Eye permissions, see Permissions Management.
- Create an IAM user.
Create a user on the IAM console and add it to the group created in 1.
- Log in as the IAM user and verify permissions.
After you log in to the Cloud Eye management console as the created user, verify that the user has the CES Administrator permissions. If no authentication failure message is displayed, the authorization is successful.
Example Custom Policies for Cloud Eye
Custom policies can be created to supplement the system-defined policies of Cloud Eye. For the actions that can be added to custom policies, see Permissions Policies and Supported Actions.
You can create custom policies in either of the following two ways:
- Visual editor: Select cloud services, actions, resources, and request conditions. This does not require knowledge of policy syntax.
- JSON: Edit JSON policies from scratch or based on an existing policy.
For details, see Creating a Custom Policy. The following lists examples of common Cloud Eye custom policies.
- Example 1: Granting permissions to modify an alarm rule
{ "Version": "1.1", "Statement": [ { "Action": [ "ces:alarms:put" ], "Effect": "Allow" } ] } - Example 2: Denying alarm rule deletion
A policy with only "Deny" permissions must be used together with other policies. If the permissions assigned to a user contain both "Allow" and "Deny", the "Deny" permissions take precedence over the "Allow" permissions.
The following method can be used if you need to assign permissions of the CES FullAccess policy to a user but you want to prevent the user from deleting alarm rules. Create a custom policy for denying alarm rule deletion, and attach both policies to the group the user belongs. Then the user can perform all operations on alarm rules except deleting alarm rules. The following is an example of a deny policy:{ "Version": "1.1", "Statement": [ { "Action": [ "ces:alarms:delete" ], "Effect": "Deny" } ] } - Example 3: Allowing users to have all operation permissions on alarm rules, including creating, modifying, querying, and deleting alarm rules
A custom policy can contain the actions of multiple services that are of the global or project-level type. The following is a policy with multiple actions:
{ "Version": "1.1", "Statement": [ { "Action": [ "ces:alarms:put", "ces:alarms:create", "ces:alarms:list", "ces:alarms:delete" ], "Effect": "Allow" } ] }
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot