Building a Ransomware Protection System Using CBR and HSS
Application Scenarios
Ransomware is special malware. The difference between ransomware and other viruses is that ransomware launches organized network attacks and asks for ransom after it encrypts data.
Ransomware has already been a critical global cyber threat. It severely hinders the growth of the digital economy. In the face of ransomware, most enterprises do not have a comprehensive and effective way to deal with it. They had to pay the ransom to ask hackers to unlock encrypted data. If enterprises are attacked, many unpredictable consequences may occur. For example, enterprise important data may be lost. Their services and production may be stopped. They may have to breach the contract. Their brand image may be affected. Enterprise managers may resign.
The Huawei Cloud Cloud Backup and Recovery (CBR) ransomware protection solution works with Host Security Service (HSS) to protect customers from ransomware and secure their data on the cloud, meeting customer requirements for data security.
Video Tutorial
Solution Architecture
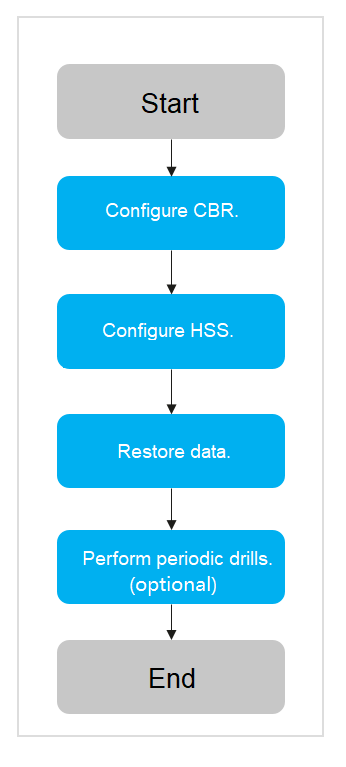
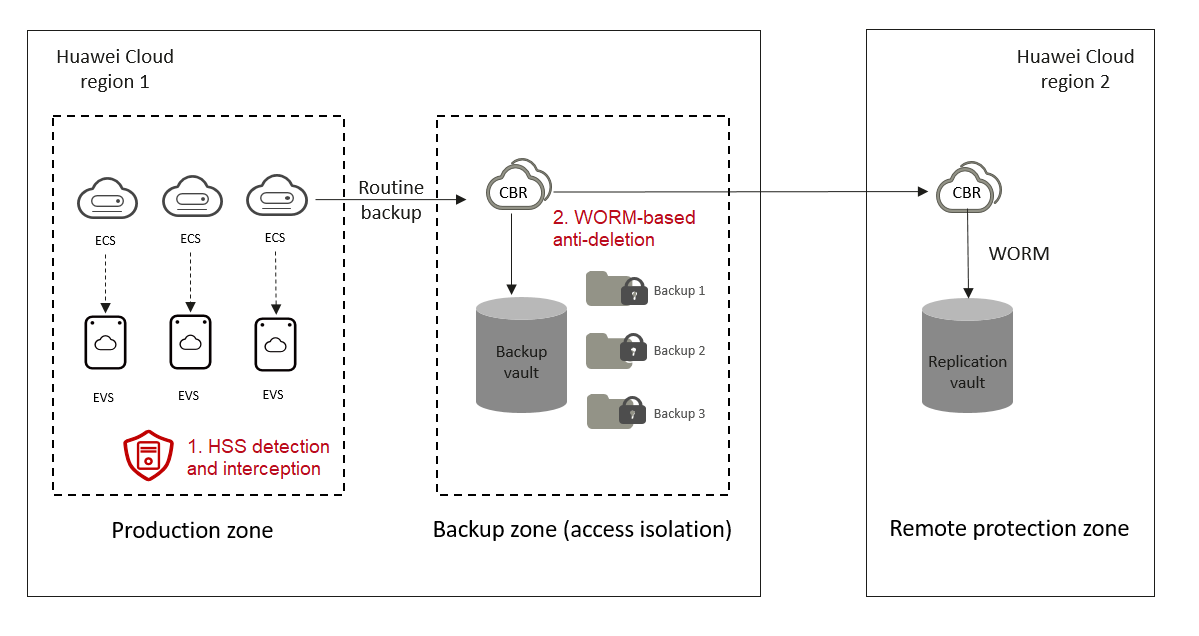
The CBR ransomware protection solution is tailored to actual service scenarios and data security needs of customers. It helps customers establish a secure and reliable system for ransomware protection so that customer data assets can be safeguarded and potential losses minimized. With access isolation and write once read many (WORM), vaults can provide at least one copy of clean, available, and tamper-proof data for restoration when a ransomware attack occurs.
Solution Advantages
- CBR works with HSS to back up data immediately if a virus is detected. This minimizes data loss risks.
- CBR backup vaults support access isolation and WORM to prevent backup data from being tampered with or deleted by mistake.
- CBR backups can be replicated to other regions. With WORM, remote backups can avoid being tampered with or deleted by mistake.
Process
The process of using the cloud backup ransomware protection solution is shown in Figure 2.
Configuring CBR and Enabling Backup Locking
Purchasing a server backup vault
Before using CBR, you must purchase a backup vault. You can purchase a backup vault with the capacity you desire. If the purchased capacity is used up, backup cannot be performed. To avoid backup failures due to insufficient capacity, enable auto expansion for your backup vault.
- Log in to the CBR console.
- Log in to the management console.
- Click
 in the upper left corner and select a region.
in the upper left corner and select a region. - Click
 and choose Storage > Cloud Backup and Recovery. Choose a backup type from the left navigation pane.
and choose Storage > Cloud Backup and Recovery. Choose a backup type from the left navigation pane.
- In the upper right corner of the page, click Buy Server Backup Vault.
- Select a billing mode.
- Yearly/monthly is a prepaid billing mode. You are billed based on the subscription duration you specify. This mode is ideal when the resource use duration is predictable. A longer subscription often means a lower cost.
- Pay-per-use is a postpaid billing mode. You are billed based on your resource usage and you can increase or delete resources anytime. Fees are deducted from your account balance.

If you purchase a pay-per-use vault, select Configure for Auto Capacity Expansion to avoid backup failures due to insufficient capacity.
- Determine whether to enable backup locking. You can also enable backup locking after you purchase the vault.
If backup locking is enabled, backups in the vault will not be deleted maliciously or by mistake. This improves data reliability.
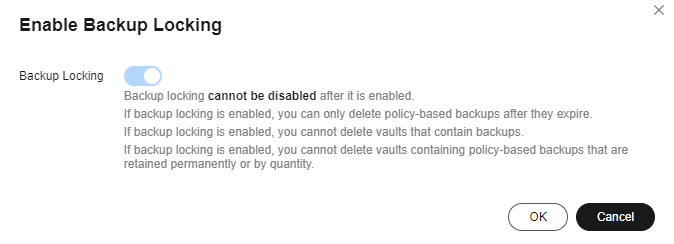

- Backup locking cannot be disabled after it is enabled. After backup locking is enabled, policy-based backups can only be deleted after they expire, and vaults that contain backups cannot be deleted. Manual backups are not affected by backup locking and can be manually deleted.
- You are advised to enable backup locking.
- If you do not enable backup locking when purchasing a vault, you can locate the vault you desire on any backup page and choose More > Enable Backup Locking in the Operation column. In the displayed dialog box, enable backup locking. For details, see Enabling Backup Locking.
- Finish other configurations as needed. For details, see Purchasing a Server Backup Vault.
After purchasing a vault, you can create and apply a backup or replication policy to the vault. You can also modify or delete the policy. For details, see Policy Management.
Configuring HSS
HSS is used in the Huawei Cloud CBR Ransomware Protection Solution. For details, see Using HSS and CBR to Defend Against Ransomware.
Restoring from a Backup
Currently, there is no effective tool to handle ransomware. The only solution is to quickly restore data from backups. When restoring a cloud server using a backup, check whether the backup is infected with ransomware. If the backup is normal, restore the cloud server from a cloud server backup. If the backup is encrypted for ransomware protection, perform the following operations.
- Log in to the management console as an IAM administrator.
- Click
 in the upper left corner and select a region.
in the upper left corner and select a region. - In the service list, choose Compute > Elastic Cloud Server.
- Purchase an ECS in an independent VPC.

An independent VPC is used to prevent ransomware infection in clean areas.
- In the service list, choose Storage > Cloud Backup and Recovery.
- In the left navigation pane, click Cloud Server Backups. On the page displayed, click the Backups tab above the list. In the search box, search for the cloud server backup to be used for restoration. You can search for the backup by backup name, vault ID, server name, server ID, or other criteria.
Figure 3 Filtering backups
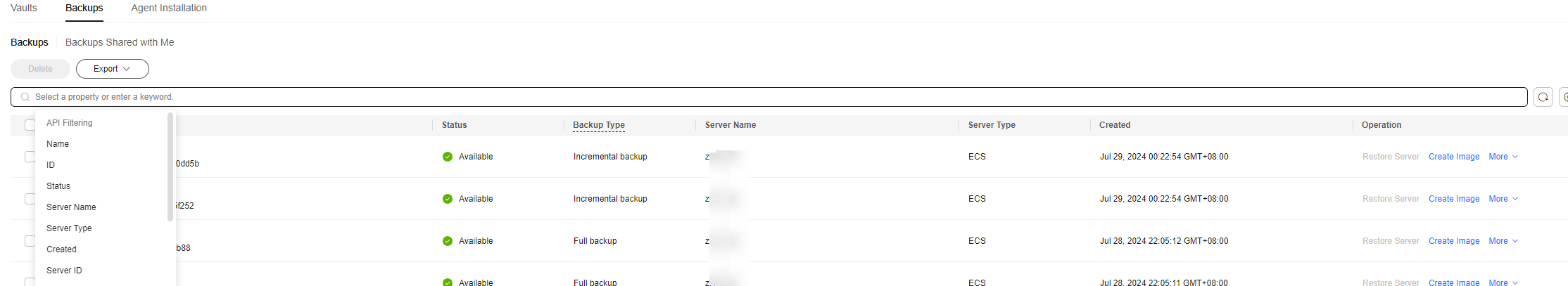
- Click the name of the selected cloud server backup. On the details page, click the Disk Backup tab.
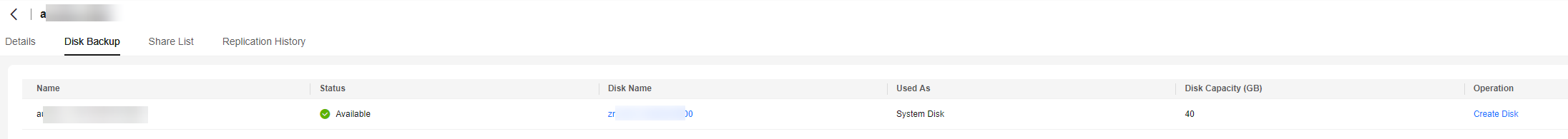
- Click Create Disk in the Operation column. On the Buy Disk page displayed, purchase a disk as required.
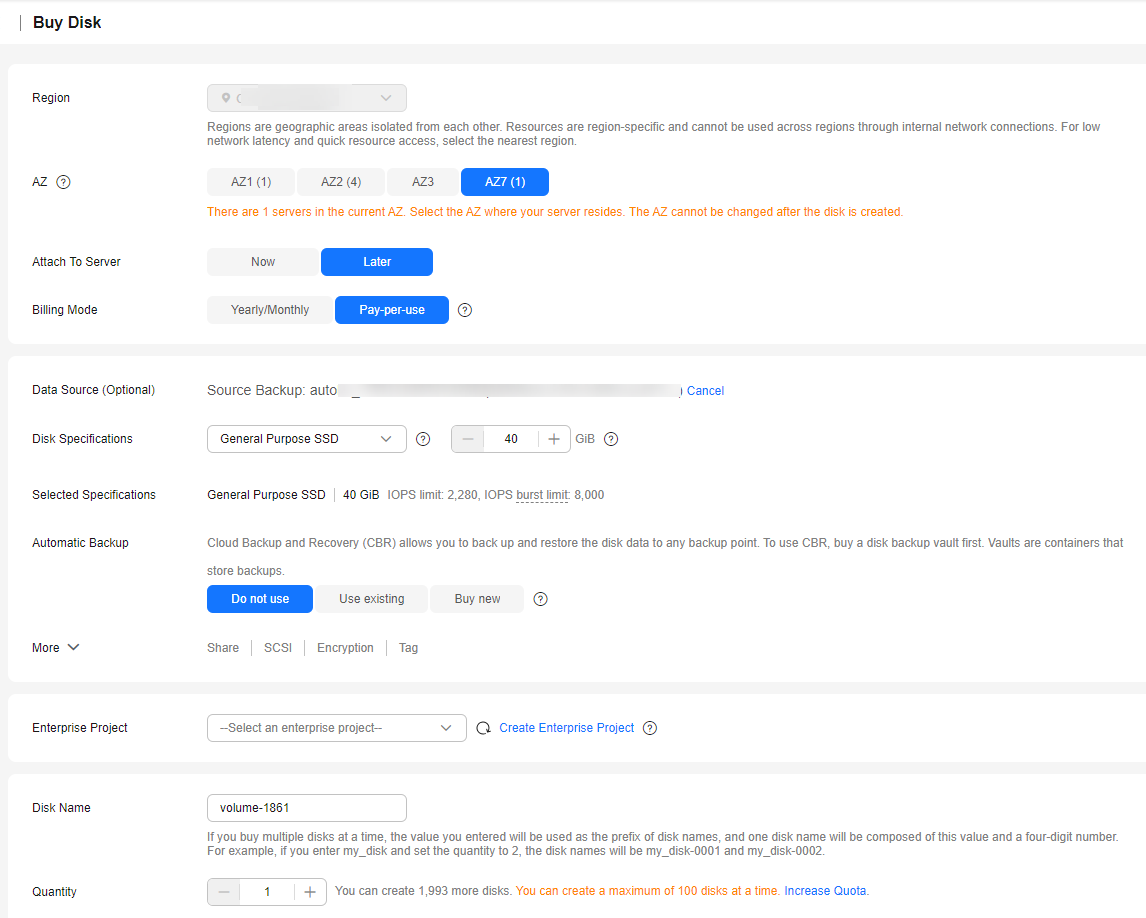
- Attach the created disk to the ECS created in step 4. Log in to the ECS to check whether the data on the disk is normal.
- Normal data can be uploaded to an object storage bucket by obsutil.
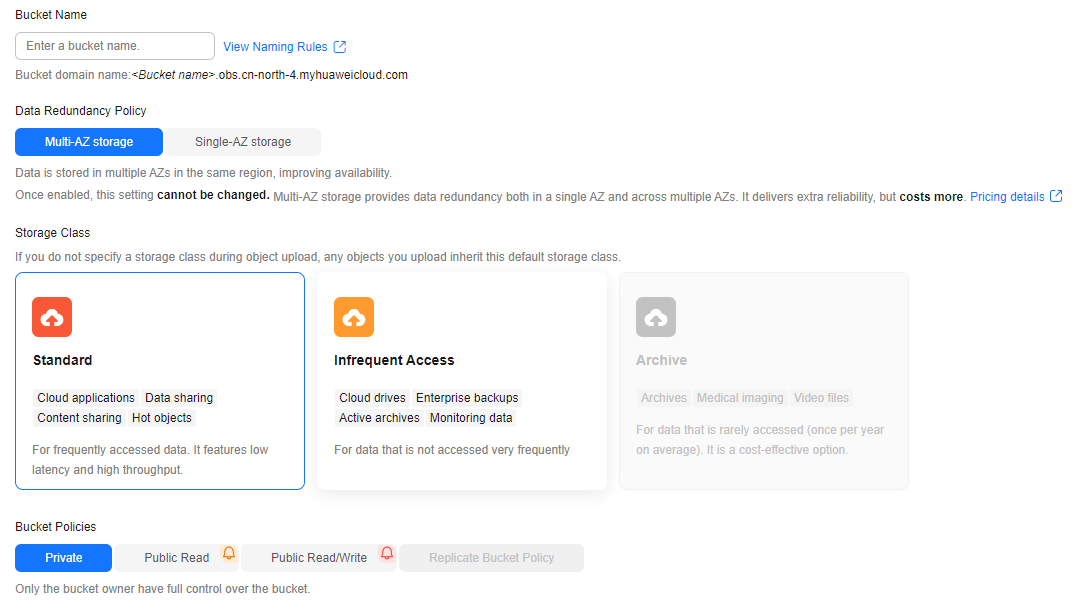
Log in to the OBS console. In the left navigation pane, click Object Storage. On the displayed page, click Create Bucket in the upper right corner. On the page displayed, create a temporary bucket named ransomware_anti_bucket_tmp to temporarily store the data. For details, see Creating a Bucket.Figure 4 Creating a bucket
- In the service list, choose Management & Governance > Identity and Access Management.
- On the page displayed, choose Permissions > Policies/Roles. Click Create Custom Policy. Set Policy Name to ransomware_anti_access. Set Policy View to JSON. Enter the following statements:
{ "Version": "1.1", "Statement": [ { "Effect": "Allow", "Action": [ "obs:object:GetObject", "obs:bucket:HeadBucket", "obs:object:GetObjectAcl", "obs:object:PutObject" ], "Resource": [ "OBS:*:*:object:*", "OBS:*:*:bucket:ransomware_anti_bucket_tmp" ] } ] }Click OK.
- Click User Groups. On the page displayed, click Create User Group. Set Name to ransomware_anti_group. Click OK. In the Operation column of the user group, click Authorize. Select the ransomware_anti_access policy, and click OK.
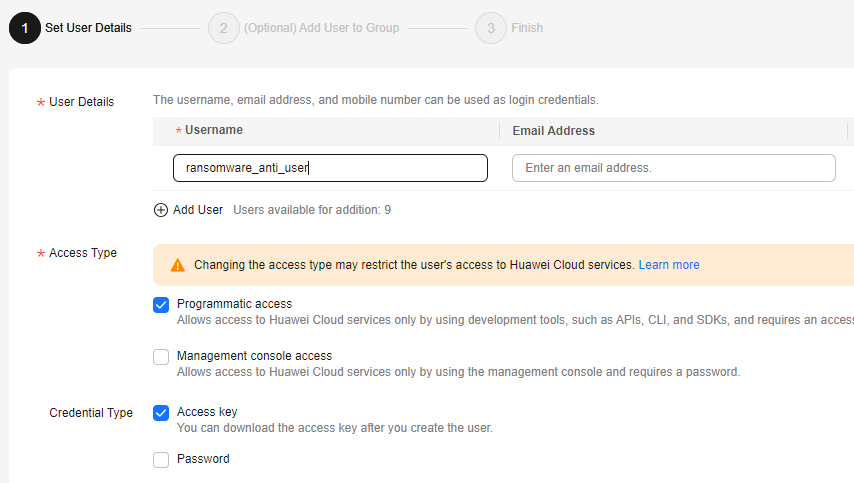
- Click Create User. Set Username to ransomware_anti_user. Select Programmatic access for Access Type. Select Access key for Credential Type. Click Next. Select the ransomware_anti_group user group. Click Create.
- After the user is created, obtain the AK/SK information of the user. Upload the data files to the temporary bucket, and download the files. For details, see uploading an object using obsutil.
- After the file is uploaded, release the temporary ECS, IAM user, user group, and bucket.
(Optional) Performing Periodic Drills
According to the data security law, data recovery tests must be performed periodically for the backup and DR data. Recovery means that the backup software is used to restore the backup data to the data source. As the service system is running in most of the time, it is not a good practice to perform recovery tests in the production environment. You can create new backup resources to verify the availability of the backup data, the integrity and reliability of the backup solution, and the system capability to deal with emergencies.
For details, see Performing a Recovery Drill Using a Cloud Server Backup.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot