Example 3: Allowing Traffic from a Service to a Platform
This section describes how to allow traffic from a service to a platform. For more parameter settings, see Configuring Protection Rules to Block or Allow Internet Border Traffic.
Domain Name Group Types
CFW provides two types of domain name groups: application domain name groups (layer 7 protocol parsing) and network domain name groups (layer 4 protocol parsing). Table 1 describes the differences between them.
|
- |
Application Domain Name Group (Layer 7 Protocol Parsing) |
Network Domain Name Group (Layer 4 Protocol Parsing) |
|---|---|---|
|
Protected object |
|
|
|
Protocol Type |
Application layer protocols, including HTTP, HTTPS, TLS, SMTPS, and POPS. |
Network layer protocols. All protocol types are supported. |
|
Match rule |
The match is based on domain name. The service compares the HOST field in sessions with the application domain names. If they are consistent, the corresponding protection rule is hit. |
The filtering is based on the resolved IP addresses. The service obtains the IP addresses resolved by DNS every 15 seconds, if the four-tuple of a session matches the network domain name rule and the resolved address has been saved (that is, the IP address has been obtained from the DNS server), the corresponding protection rule is hit. |
|
Suggestion |
You are advised to use the application domain name group (for example, the domain name accelerated by CDN) for the domain names that have a large number of mapping addresses or rapidly changing mapping results. |
|
Allowing Traffic from a Service to a Platform
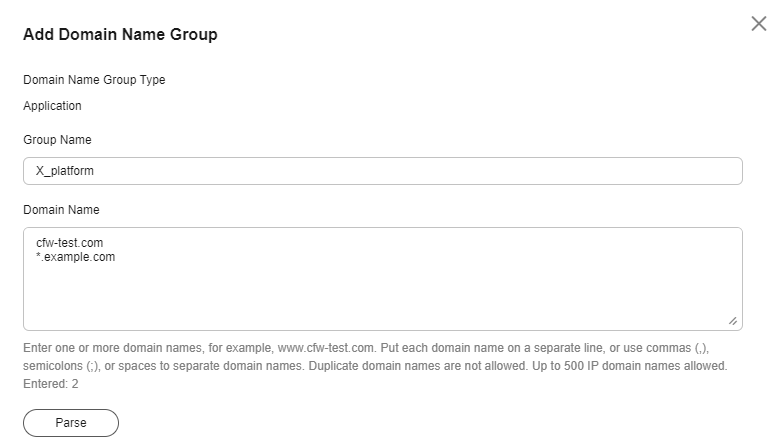
- Create an application domain name group and configure the platform domain names, as shown in Figure 1.
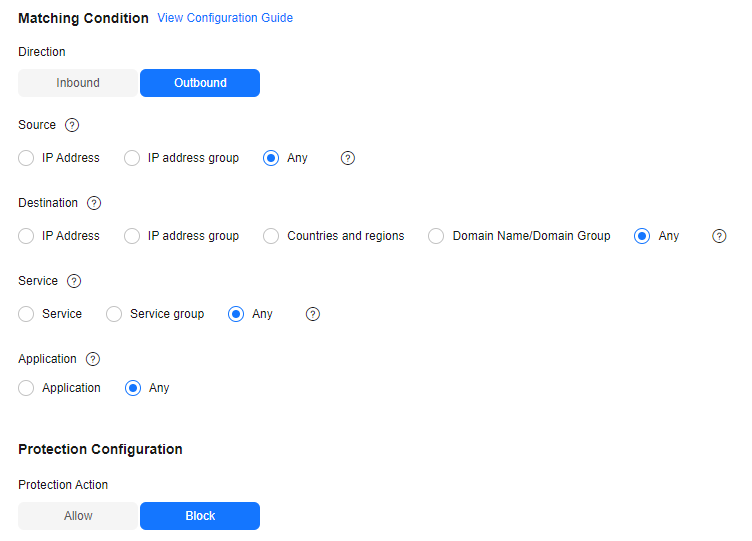
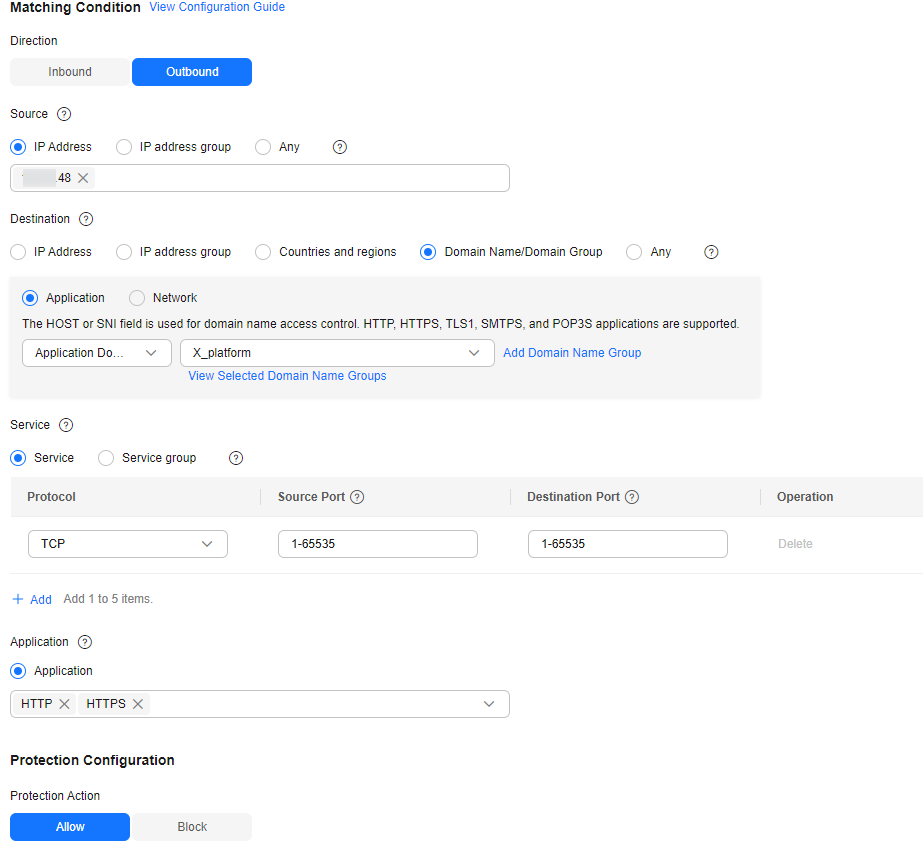
- Configure the following protection rules:
Follow-up Operations
- Policy hits: For details about the protection overview, see Viewing Protection Information Using the Policy Assistant. For details about logs, see Access Control Logs.
- For details about the traffic trend and statistics, see Traffic Analysis. For details about traffic records, see Traffic Logs.
References
- For details about protection rule parameters, see Configuring Protection Rules to Block or Allow Internet Border Traffic.
- For details about blacklist and whitelist configuration, see Adding Blacklist or Whitelist Items to Block or Allow Traffic.
- For details about how to batch add protection policies, see Importing and Exporting Protection Policies.
- For details about how to block network attacks, see Configuring Intrusion Prevention.
- For details about antivirus, see Configuring Virus Defense.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot