Configuring Grayscale Release for a LoadBalancer Ingress
Dedicated LoadBalancer ingresses support grayscale release by:
- Proportion
- HTTP request header
- Cookie

Ingress grayscale release requires ELB support for weighted backend server groups and cookie-based advanced forwarding policies. Submit a service ticket to enable ELB grayscale release before use.
Prerequisites
- A CCE standard or Turbo cluster is available, and the cluster version meets the following requirements:
- v1.23: v1.23.14-r0 or later
- v1.25: v1.25.9-r0 or later
- v1.27: v1.27.6-r0 or later
- v1.28: v1.28.4-r0 or later
- Other clusters of later versions
Notes and Constraints
- After a grayscale ingress is created, do not delete the original ingress.
- When configuring multiple grayscale release policies for ingresses associated with a load balancer listener, the policy based on HTTP request headers takes the highest priority. The cookie-based policy has the second highest priority. The proportion-based policy has the lowest priority.
- This feature relies on the ELB advanced forwarding policies. Once enabled, the priority is not determined by the domain name or path matching. You can customize the forwarding policy priority as needed. For details about the forwarding policy priority, see Forwarding Policy Priorities of LoadBalancer Ingresses.
Using the CCE Console
- Log in to the CCE console and click the cluster name to access the cluster console.
- Deploy the original service.
- In the navigation pane, choose Workloads. Then, click Create Workload in the upper right corner and deploy a workload named origin-server. For details about parameter settings, see Creating a Deployment.
- In the navigation pane, choose Services & Ingresses. On the Services tab page, click Create Service in the upper right corner. Create a Service named origin-service and associate it with the created origin-server workload. For a CCE standard cluster, create a NodePort Service, and for a CCE Turbo cluster, create a ClusterIP Service.
- In the navigation pane, choose Services & Ingresses. Click the Ingresses tab page and then Create Ingress in the upper right corner. Create an ingress named origin-ingress and associate it with the created origin-service Service. For details about parameter settings, see Creating a LoadBalancer Ingress on the Console.
- Grayscale release a new version for the Service.
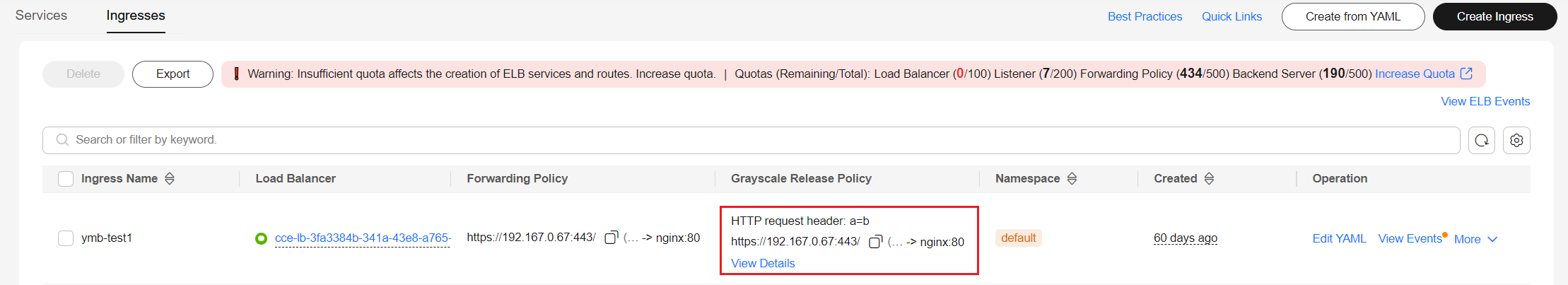
- In the navigation pane, choose Services & Ingresses, switch to the Ingresses tab, locate the row containing the ingress for which you want to configure grayscale release, and choose More > Create Grayscale Release in the Operation column.
- Configure grayscale release parameters.
Table 1 Key parameters Parameter
Description
Example
Gray release
- HTTP request header: When the header key-value pair in an HTTP request is matched, the grayscale released Service can be accessed.
- If domain names and paths are configured for an ingress forwarding policy, a maximum of eight values can be configured.
- If only paths are configured for an ingress forwarding policy, a maximum of nine values can be configured.
- Cookie: When the cookie key-value pair in an HTTP request is matched, the grayscale release service can be accessed.
- Proportion: percentage of the requests for accessing the grayscale release service to the total number of requests
HTTP request header
- Key: a
- Value: b
Forwarding Policy
- Domain Name: Enter an actual domain name to be accessed. If it is left blank, the ingress can be accessed through the IP address. Ensure that the domain name has been registered and licensed. Once a forwarding policy is configured with a domain name specified, you must use the domain name for access.
- Grayscale Release: After grayscale release is enabled for a domain name, external access traffic of the cluster will be forwarded to the target Service using the selected traffic policy.
- Traffic Policy: Select from HTTP request header, Cookie, and Proportion (percentage of grayscale release requests) as needed.
- Destination Service: Select an existing Service. Only Services that meet the requirements are automatically displayed in the Service list. If no Service meets the requirements, create one by following the operations provided in Services Supported by Ingresses.
- Destination Service Port: Select the access port of the destination Service.
- Domain Name: You do not need to configure this parameter.
- Grayscale Release: enabled
- Traffic Policy: HTTP request header
- Destination Service: nginx
- Destination Service Port: 80
- HTTP request header: When the header key-value pair in an HTTP request is matched, the grayscale released Service can be accessed.
- Click OK.
- Check whether the new version is grayscale released.
- Terminate the old-version Service.
After the Service of the new version runs stably, terminate the Service of the old version. During the Service termination, change the original Service to the new-version Service so that all traffic will be routed to the new-version Service. Then, delete the grayscale released ingress.
Using kubectl
- Deploy the original service.
- Deploy a workload named origin-server.
- Deploy a Service named origin-service and associate it with the created origin-server workload. (Create a NodePort Service in a CCE standard cluster or a ClusterIP Service in a CCE Turbo cluster.)
- Deploy an ingress named origin-ingress and associate it with the created origin-service Service.
Configure the ingress as follows:
apiVersion: networking.k8s.io/v1 kind: Ingress metadata: name: origin-ingress namespace: default annotations: kubernetes.io/elb.port: '81' kubernetes.io/elb.id: e491f4e7-2351-4984-ad0a-8569e5e964a3 kubernetes.io/elb.class: performance spec: rules: - host: example.com http: paths: - path: / backend: service: name: origin-service port: number: 81 property: ingress.beta.kubernetes.io/url-match-mode: STARTS_WITH pathType: ImplementationSpecific ingressClassName: cce
- Grayscale release a new version for the Service.
Deploy the workload, Service, and ingress of a new version so that traffic can be routed to the Service of the new version by weight or header.
- Deploy a workload named canary-server.
- Deploy a Service named canary-service and associate it with the created canary-server workload. (Create a NodePort Service in a CCE standard cluster or a ClusterIP Service in a CCE Turbo cluster.)
- Create a grayscale released ingress. For details about parameter settings, see Parameters.
- Scenario 1, by HTTP request header: When the header key-value pair in an HTTP request is matched, the grayscale released Service can be accessed.
Deploy an ingress named canary-header-ingress and associate it with the created canary-service Service for grayscale release by header.
Configure the ingress as follows:apiVersion: networking.k8s.io/v1 kind: Ingress metadata: name: canary-header-ingress namespace: default annotations: kubernetes.io/elb.canary: 'true' # Set this parameter to true, indicating that canary annotation is enabled. kubernetes.io/elb.canary-by-header: 'location' # Set the header key to location. kubernetes.io/elb.canary-by-header-value: '{"values":["hz","sz","sh"]}' # Set the header values to hz, sz, and sh. kubernetes.io/elb.class: performance # Only dedicated load balancers support grayscale release. kubernetes.io/elb.id: e491f4e7-2351-4984-ad0a-8569e5e964a3 kubernetes.io/elb.port: '81' spec: ingressClassName: cce rules: - host: example.com http: paths: - path: / pathType: ImplementationSpecific backend: service: name: canary-service port: number: 80 property: ingress.beta.kubernetes.io/url-match-mode: STARTS_WITH - Scenario 2: by proportion: Configure the proportion of requests for accessing the grayscale released Service.
Deploy an ingress named canary-weight-ingress and associate it with the created canary-service Service for grayscale release by weight.
Configure the ingress as follows:apiVersion: networking.k8s.io/v1 kind: Ingress metadata: name: canary-weight-ingress namespace: default annotations: kubernetes.io/elb.canary: 'true' # Set this parameter to true, indicating that canary annotation is enabled. kubernetes.io/elb.canary-weight: '40' # Configure a weight, indicating that 40% of the request traffic will be routed to the Service of the new version. kubernetes.io/elb.class: performance # Only dedicated load balancers support grayscale release. kubernetes.io/elb.id: e491f4e7-2351-4984-ad0a-8569e5e964a3 kubernetes.io/elb.port: '81' spec: ingressClassName: cce rules: - host: example.com http: paths: - path: / pathType: ImplementationSpecific backend: service: name: canary-service port: number: 81 property: ingress.beta.kubernetes.io/url-match-mode: STARTS_WITH - Scenario 3, by cookie: When the cookie key-value pair in a request is matched, the grayscale released Service can be accessed.
Deploy an ingress named canary-cookie-ingress and associate it with the created canary-service Service for grayscale release by cookie.
Configure the ingress as follows:apiVersion: networking.k8s.io/v1 kind: Ingress metadata: name: canary-cookie-ingress namespace: default annotations: kubernetes.io/elb.canary: 'true' # Set this parameter to true, indicating that canary annotation is enabled. kubernetes.io/elb.canary-by-cookie: 'location' # Set the header key to location. kubernetes.io/elb.canary-by-cookie-value: '{"values":["hz","sz","sh"]}' # Set the header values to hz, sz, and sh. kubernetes.io/elb.class: performance # Only dedicated load balancers support grayscale release. kubernetes.io/elb.id: e491f4e7-2351-4984-ad0a-8569e5e964a3 kubernetes.io/elb.port: '81' spec: ingressClassName: cce rules: - host: example.com http: paths: - path: / pathType: ImplementationSpecific backend: service: name: canary-service port: number: 81 property: ingress.beta.kubernetes.io/url-match-mode: STARTS_WITH
- Scenario 1, by HTTP request header: When the header key-value pair in an HTTP request is matched, the grayscale released Service can be accessed.
- Check whether the new version is grayscale released.
- Check the creation of the ingress.
kubectl get ingress
Command output:NAME CLASS HOSTS ADDRESS PORTS AGE canary-cookie-ingress cce example.com 88.88.88.165 80 16s canary-header-ingress cce example.com 88.88.88.165 80 46s canary-weight-ingress cce example.com 88.88.88.165 80 117s origin-ingress cce example.com 88.88.88.165 80 2m25s
- Check the result of a service request.
- Use the location: hz request header to access the Service.
curl -H "Host: example.com" -H "location: hz" http://88.88.88.165:81/
Expected result:new
Attempt the access for multiple times. All the returned results are new.
- Access the Service without using a request header.
curl -H "Host: example.com" http://88.88.88.165:81/
Expected result: 40% for new, and 60% for old
- Use the location: hz request header to access the Service.
- Check the creation of the ingress.
- Terminate the old-version Service.
After the Service of the new version runs stably, terminate the Service of the old version. During the Service termination, change the original Service to the new-version Service so that all traffic will be routed to the new-version Service. Then, delete the grayscale released ingress.
- Change the original Service to the new-version Service.
apiVersion: networking.k8s.io/v1 kind: Ingress metadata: name: origin-ingress namespace: default annotations: kubernetes.io/elb.port: '81' kubernetes.io/elb.id: e491f4e7-2351-4984-ad0a-8569e5e964a3 kubernetes.io/elb.class: performance spec: rules: - host: example.com http: paths: - path: / backend: service: name: canary-service port: number: 81 property: ingress.beta.kubernetes.io/url-match-mode: STARTS_WITH pathType: ImplementationSpecific ingressClassName: cce - Check whether the old-version Service has been terminated.
Initiate a request with a header and a request without a header to access the Service.
curl -H "Host: example.com" -H "location: hz" http://88.88.88.165:81/ curl -H "Host: example.com" http://88.88.88.165:81/
Expected result: All results are returned from the new-version Service.
- Delete the grayscale released ingress.
kubectl delete ingress canary-cookie-ingress canary-weight-ingress canary-header-ingress
- Change the original Service to the new-version Service.
Parameters
|
Parameter |
Mandatory |
Type |
Description |
|---|---|---|---|
|
kubernetes.io/elb.canary |
No |
String |
Grayscale release status for an ingress. If this parameter is set to true, the implementation of grayscale release varies depending on annotation configurations. Option: true
|
|
kubernetes.io/elb.canary-weight |
No |
String |
Weight of a grayscale release. After this parameter is configured, the ingress will be grayscale released based on the weight.
|
|
kubernetes.io/elb.session-affinity-mode |
No |
String |
After weight-based grayscale release is enabled, configure sticky session. This parameter can only be set to HTTP_COOKIE for grayscale release. |
|
kubernetes.io/ elb.session-affinity-option |
No |
String |
Sticky session timeout after sticky session is enabled for weight-based grayscale release. The parameter value is a JSON string in the following format: {"persistence_timeout": "1440"}
Parameters:
|
|
kubernetes.io/elb.canary-by-header |
No |
String |
Key of an ingress header used for grayscale release, indicating the name of a request header. This parameter must be used with kubernetes.io/elb.canary-by-header-value. Parameters: Enter 1 to 40 characters. Only letters, digits, hyphens (-), and underscores (_) are allowed. |
|
kubernetes.io/elb.canary-by-header-value |
No |
String |
Value of an ingress header used for grayscale release. This parameter must be used with kubernetes.io/elb.canary-by-header. The parameter value is an array in JSON format, for example: '{"values":["a","b"]}'
Parameters:
|
|
kubernetes.io/elb.canary-by-cookie |
No |
String |
Key of cookie-based grayscale release, indicating the name of a request cookie. This parameter must be used with kubernetes.io/elb.canary-by-cookie-value. Parameters: Enter 1 to 100 characters, including letters, digits, and other characters (!%'"()*+,./:=?@^\\-_`~). |
|
kubernetes.io/elb.canary-by-cookie-value |
No |
String |
Value of cookie-based grayscale release. This parameter must be used with kubernetes.io/elb.canary-by-cookie. The parameter value is an array in JSON format, for example: '{"values":["a","b"]}'
Parameters:
|
|
kubernetes.io/elb.canary-related-ingress-uid |
No |
String |
UID of the original ingress associated with the grayscale release ingress, which is used to display the association between the original ingress and the grayscale release ingress. ● Format: character string ● Value: metadata.uid of the original ingress |
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot