External Attack Sources
Prerequisites
Blacklist and Whitelist Authorization has been completed.
Context
Huawei Qiankun determines whether a threat event is an external attack source based on the following rules:
- If a host in a user-untrusted zone or mixed zone launches attacks, the IP address of the host is not in the global whitelist or in the default private network segment, the threat event is an external attack source.
For details about the user-untrusted zone and mixed zone, see Configuring Device Security Zones. For details about the global whitelist, see Configuring a Global Whitelist. The default private network segments are 10.0.0.0 to 10.255.255.255, 172.16.0.0 to 172.31.255.555, and 192.168.0.0 to 192.168.255.255.
- If an intranet IP address in the user-untrusted zone or mixed zone initiates attacks and the IP address is an untrusted private IP address, the threat event is an external attack source. For details about the untrusted intranet IP address, see Configuring Untrusted Intranet Addresses.
Huawei Qiankun can handle an external attack source event in the following ways:
- Huawei Qiankun intelligently analyzes the event, delivers an IP address blacklist, and sets the handling status of the event to Blocked.
- Huawei Qiankun intelligently analyzes the event and cannot deliver an IP address blacklist. security operations experts then conduct a further analysis and manually deliver an IP address blacklist. In this case, the handling status of the event is displayed as Blocked.
- If both intelligent analysis of Huawei Qiankun and security operations experts cannot handle the event based on existing information or the handling policy fails to be delivered, the handling status of the event is displayed as Unhandled.
Tenants need to manually handle such events by employing measures such as blocking attack sources and marking their status (Manually handled or Ignored).
- Border Protection and Response Service Standard and automatic blocking
- Border Protection and Response Service Professional
- Border Protection and Response Service Advanced
- Border Protection and Response Service Trial
Procedure
- Log in to the Huawei Qiankun console, and choose .
- Click Threat Events in the menu bar.
- Check the overview of external attack sources, and click a number or View More to view details.
Figure 1 Overview of external attack sources
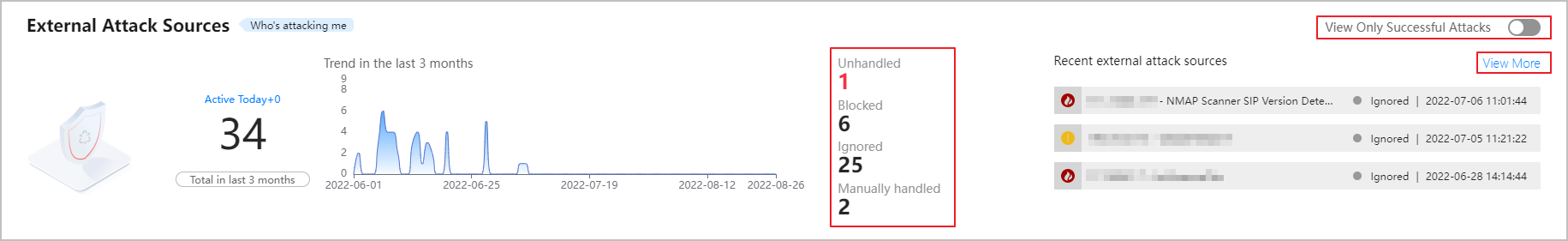
- Handle the external attack sources
- Block attack sources.
If an IP address is an external attack source address, click Block Attack Source in the operation column to deliver the IP address blacklist.
After receiving the IP address blacklist from Huawei Qiankun, the Qiankun Shield devices block traffic sent by and to the blacklisted IP address.
Devices can work in hot standby mode. If two devices are onboarded and bound to work in hot standby mode but the active device cannot work properly, the standby device will take over services from the active device. When you block external attack sources on the By Event tab page, the IP address blacklist is delivered to both the devices working in hot standby mode, and you can see two records in the Historical IP Blacklist.
Figure 2 Blocking attack sources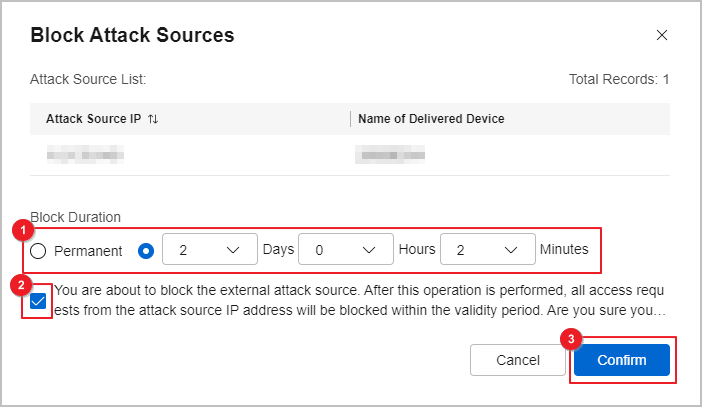
If the handling status of the external attack source is marked
 , the external attack source is unblocked.
, the external attack source is unblocked. - Mark the event status.
- Manually handled
Tenants manually handle external attack source events, for example, searching for the target hosts based on the source and destination addresses of the events, and scanning for and removing viruses from the target hosts. Then, they can mark the event status as Manually handled.
- Ignored
If an event does not need to be handled or is a false positive, set the event status to Ignored in the operation column.
- Manually handled
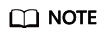
If you do not know how to handle the problem or the problem persists after you handle it, contact the corresponding Managed Security Service Provider (MSSP) or channel partner.
- Block attack sources.
Follow-up Procedure
- On the External Attack Sources page, a national flag is displayed before each IP address in the Attack Source IP column. You can move the mouse cursor over a flag to view the country name, and click an IP address to check details about the external attack source.
You can set search criteria in Advanced Search and click Export to export the list of external attack sources that meet the search criteria to an Excel file. Alternatively, you can select the target external attack sources and click Export to export the list of selected external attack sources.Figure 3 List of external attack sources
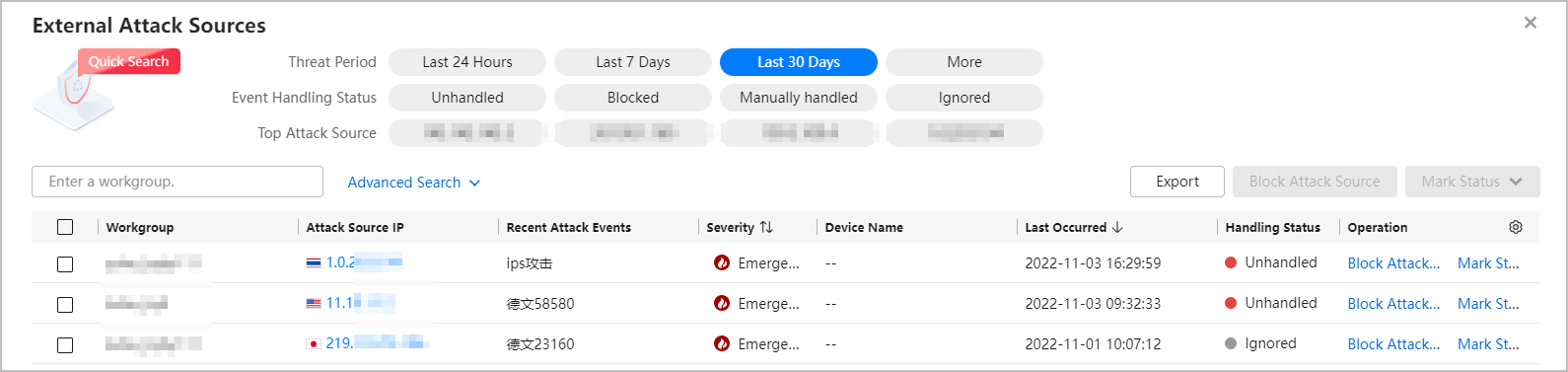
- The external attack source details page displays information such as handling suggestions, handling records, external attack source analysis, and associated alarm event list.
- You can click Export to export details about a specific external attack source to a Word file.
Figure 4 Details page of an external attack source
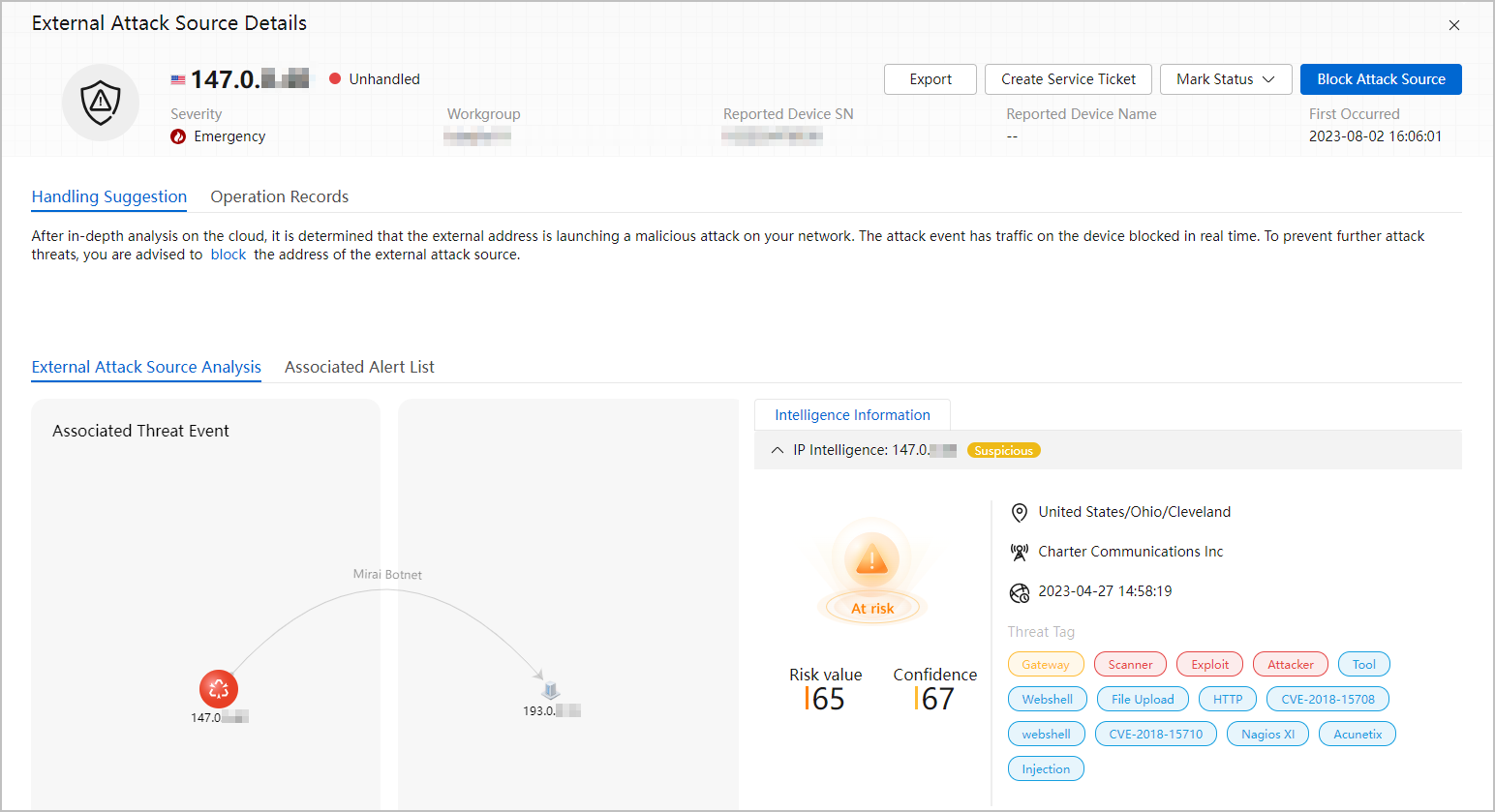
After the export is complete, click your account in the upper right corner and click Download to download the corresponding file.
Figure 5 Download Center
- You can click an event name in the Associated Threat Event List area on the External Attack Source Details page to check details about the event.
Figure 6 Threat Event Details page
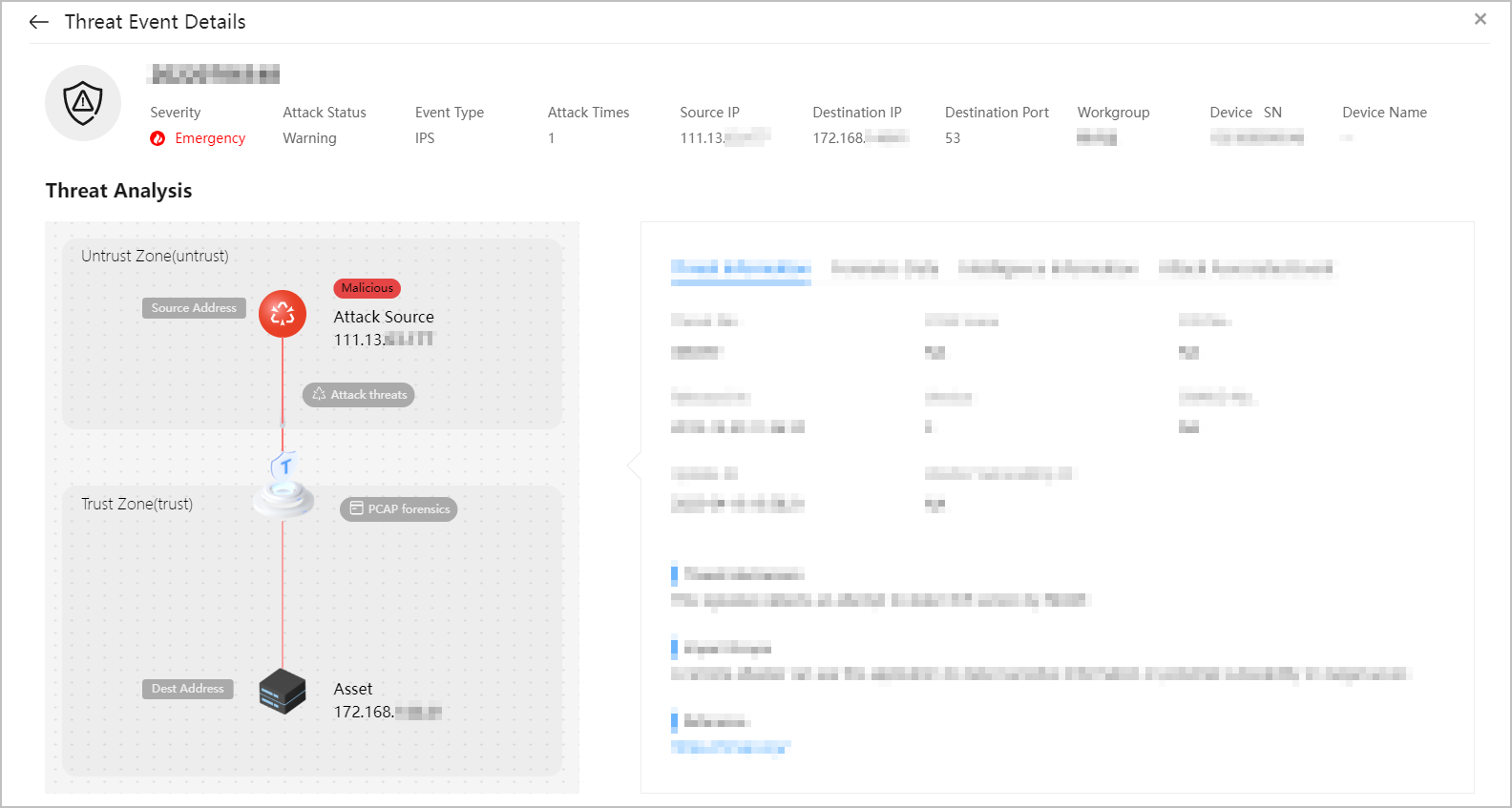
The External Attack Source Details page may contain public IP addresses, helping you learn about threat events. The service does not proactively initiate connections to these public IP addresses.
- You can click Export to export details about a specific external attack source to a Word file.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot






