Blacklist and Whitelist Authorization
Prerequisites
Perform the following steps to configure the address security domains. Then, perform blacklist and whitelist authorization so that Huawei Qiankun can correctly deliver the IP blacklists.
- Configuring Device Security Zones.
Huawei Qiankun delivers an IP address blacklist for a threat event only when the threat event is initiated from User-untrusted Zone. Therefore, you need to add the corresponding security zone to User-untrusted Zone.
- Configuring a Global Whitelist.
After the configuration, Huawei Qiankun cannot deliver an IP address in the global whitelist as a blacklisted IP address to the Qiankun Shield Device. This ensures that IP address blacklists can be delivered properly by Huawei Qiankun.
- Configuring Untrusted Intranet Addresses.
After the configuration, Huawei Qiankun matches IP addresses in the IP address blacklist against those in Untrusted Intranet IP Address. If the IP addresses are not found in Untrusted Intranet IP Address, Huawei Qiankun does not deliver the IP addresses as blacklisted IP addresses to the device.
Context
Huawei Qiankun uses the automatic analysis model to analyze the logs provided by the device, and automatically delivers the IP address blacklist and domain name blacklist based on the analysis result. Huawei Qiankun can automatically deliver the IP address blacklist and domain name blacklist to a tenant's devices only after the tenant authorizes blacklist management.
The default validity period of the blacklists automatically delivered by Huawei Qiankun is two days.
Currently, only top-level tenants have the permission to authorize blacklist and whitelist management.
Procedure
- Log in to the Huawei Qiankun console, and choose .
- Click Services in the menu bar, and choose Authorization > Blacklist and Whitelist Agreement.
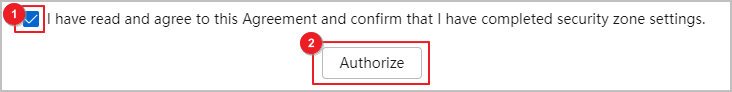
- Perform authorization after verifying that the IP address security zone management is completed.
Figure 1 Blacklist and whitelist authorization
Follow-up Procedure
After the function is authorized, you can perform the following operations:
- Managing Blacklists and Whitelists.
- You can click Cancel Authorization or Authorize again at any time as required.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot






