Configuring a Protection Rule to Protect Traffic Between Two VPCs
Application Scenarios
A large amount of data needs to be exchanged between VPCs. CFW can check and collect statistics on inter-VPC traffic, helping you detect abnormal traffic.
This section describes how to configure CFW to protect traffic between VPC1 (172.16.0.0/16) and VPC2 (172.18.0.0/16).
Constraints
- Only the professional edition supports VPC border firewalls.
- Traffic diversion depends on the enterprise router in enterprise router mode.
- To use public network CIDR blocks other than 10.0.0.0/8, 172.16.0.0/12, 192.168.0.0/16, or the 100.64.0.0/10 segment reserved for carrier-level NAT as private network CIDR blocks, modify private network CIDR blocks or submit a service ticket to expand your private IP CIDR blocks, or CFW may fail to forward traffic between your VPCs.
Applicable Version
This section is applicable to the new version of the VPC border firewall. Its configuration GUI is as follows.

How to Configure
The process is as follows:
- Create a firewall (for example, vpc-cfw-er) and associate it with subnets. For details, see Step 1: Create a Firewall.
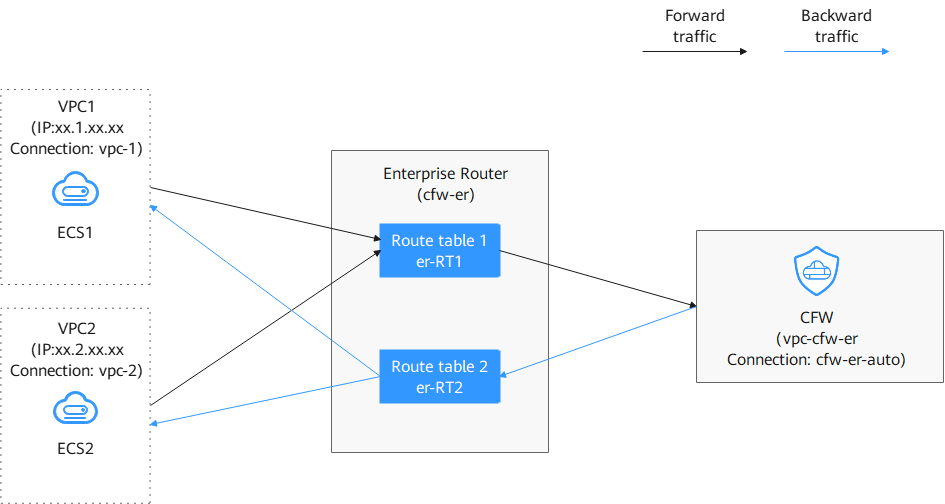
- Configure an enterprise router.
- Configure all VPCs (including the firewall VPC and the VPC to be connected) to let them route traffic to the enterprise router. For details, see Diverting Traffic to Enterprise Router.
- Create attachments for all VPCs (including the firewall VPC and the VPC to be connected). For details, see Adding Connections.
- Create two route tables (er-RT1 and er-RT2, for example). For details, see Creating Two Route Tables.
- Configure the association route table er-RT1 to transmit traffic from the VPC to the CFW. For details, see Configuring Route Table er-RT1.
Configure the propagation route table er-RT2 to transmit traffic from the CFW to the VPC. For details, see Configuring Route Table er-RT2.
- Modify VPC route tables.
- Enable VPC protection and verify the communication.
- Configure protection rules and view the outcomes.
Video Tutorial
This video demonstrates how to configure protection rules to protect inter-VPC traffic.
Step 1: Create a Firewall
- Log in to the CFW console.
- Click
 in the upper left corner of the management console and select a region or project.
in the upper left corner of the management console and select a region or project. - In the navigation pane, choose Assets > Inter-VPC Border Firewalls.
- Click Create Firewall, select an enterprise router, and configure a CIDR block.
- An enterprise router is used for traffic diversion. It must meet the following requirements:
- Not associated with other firewall instances.
- Belongs to the current account and is not shared with other users.
- Default Route Table Association, Default Route Table Propagation, and Auto Accept Shared Attachments must be disabled.
- After a CIDR block is configured, an inspection VPC is created by default to forward traffic to CFW. A CFW-associated subnet is automatically allocated to forward traffic to an enterprise router. Pay attention to the following restrictions:
- After a firewall is created, its CIDR block cannot be modified.
- The CIDR block must meet the following requirements:
- Only private network address segments (10.0.0.0/8, 172.16.0.0/12, and 192.168.0.0/16) are supported. Otherwise, route conflicts may occur in public network access scenarios, such as SNAT.
- The CIDR block 10.6.0.0/16-10.7.0.0/16 is reserved for CFW and cannot be used.
- This CIDR block cannot overlap with the private CIDR block to be protected, or routing conflicts and protection failures may occur.
- An enterprise router is used for traffic diversion. It must meet the following requirements:
- Click OK. The firewall will be created in 3 to 5 minutes.
Step 2: Configure an Enterprise Router
- Log in to the VPC console.
- Click
 in the upper left corner of the management console and select a region or project.
in the upper left corner of the management console and select a region or project. - Configure the route tables of VPCs (VPC1, VPC2, and vpc-cfw-er) to divert traffic to the enterprise router.
In the service list, choose Networking > Virtual Private Cloud. In the navigation pane, choose Route Tables. In the Name/ID column, click the route table name of the VPC to be protected.
Click Add Route. The following table describes the parameters.
Table 1 Route parameters Parameter
Description
Example Value
Destination
Destination CIDR block.
The CIDR block cannot conflict with existing routes or subnet CIDR blocks in the VPCs.
xx.xx.xx.0/16
Next Hop Type
Select Enterprise Router from the drop-down list.
Enterprise Router
Next Hop
Select a resource for the next hop.
The enterprise routers you created are displayed in the drop-down list.
cfw-er
Description
(Optional) Description of a route.
Enter up to 255 characters. Angle brackets (< or >) are not allowed.
-
- In the service list, Choose Networking > Enterprise Router.
Add a VPC connection to the enterprise router. For details, see Adding VPC Attachments to an Enterprise Router.
- Add at least three VPC attachments (for CFW and the two protected VPCs). An attachment is required for each protected VPC you add.
For example, the firewall attachment (automatically generated after the firewall is created) is named cfw-er-auto, the VPC1 attachment is named vpc-1, the VPC2 attachment is named vpc-2, and the VPC3 attachment is named vpc-3.
- To use the enterprise router of account A to protect VPCs under account B, share the router with account B. For details, see Creating a Sharing.
- In this section, the firewall attachment is named cfw-er-auto (automatically created with the firewall), the VPC1 connection is named vpc-1, and the VPC2 connection is named vpc-2.
- Add at least three VPC attachments (for CFW and the two protected VPCs). An attachment is required for each protected VPC you add.
- Create two route tables er-RT1 and er-RT2 for connecting to the VPC and the firewall, respectively.
Click the enterprise router name and click the Route Table tab. Click Create Route Table.
For details about the parameters, see Table 2.
Table 2 Route table parameters Parameter
Description
Example Value
Name
Route table name. The name:
- Must contain 1 to 64 characters.
- Can contain letters, digits, underscores (_), hyphens (-), and periods (.).
er-RT1/er-RT2
Tag
During the route table creation, you can tag the route table resources. Tags identify cloud resources for purposes of easy categorization and quick search.
For details about tags, see Tag Overview.
Tag key: test
Tag value: 01
Description
Route table description
-
- Configure the association route table er-RT1. Set the associations and routing.
- Select the route table (er-RT1) to be connected to the VPC. On the Route Tables tab, click the Associations tab and click Create Association.
See Figure 3. For more information, see Association parameters.
Table 4 VPC2 association parameters Parameter
Description
Example Value
Attachment Type
Select VPC.
VPC
Attachment
Select the attachment of the VPC to be protected.
vpc-2
- Create the routing of the route table (er-RT1). Click the Routes tab and click Create Route. You can create one or more routes as needed.
See Figure 4. For more information, see Route parameters.
Table 5 Route parameters Parameter
Description
Destination
Set the destination address.
- If 0.0.0.0/0 is configured, all the traffic (IPv4) of the VPC is protected by CFW.
- If a CIDR block is configured, the traffic of the CIDR block is protected by CFW.
Blackhole Route
You are advised to disable this function. If it is enabled, the packets from a route that matches the destination address of the blackhole route will be discarded.
Attachment Type
Set Attachment Type to CFW instance.
Next Hop
Select the automatically generated firewall attachment cfw-er-auto-attach.
Description
(Optional) Description of a route.
- Select the route table (er-RT1) to be connected to the VPC. On the Route Tables tab, click the Associations tab and click Create Association.
- Configure the propagation route table er-RT2. Set the associations and routing.
- Select the route table (er-RT2) to be connected to the firewall. Click the Associations tab and click Create Association.
See Figure 5. For more information, see Association parameters.
- Create propagations for the route table (er-RT2). Click the Propagations tab and click Create Propagation.
See Figure 6. For more information, see Propagation parameters.
Table 7 Propagation parameters Parameter
Description
Example Value
Attachment Type
Select VPC.
VPC
Attachment
Select the attachment of the VPC to be protected.
vpc-1
Table 8 Propagation parameters Parameter
Description
Example Value
Attachment Type
Select VPC.
VPC
Attachment
Select the attachment of the VPC to be protected.
vpc-2

- Add at least two propagations. A propagation is required for each protected VPC you add.
For example, select attachment vpc-1 for VPC1 and vpc-2 for VPC2. To add VPC3 for protection, add a propagation and select attachment vpc-3.
- After a propagation is created, its route information will be extracted to the route table of the enterprise router, and a propagation route will be generated. In the same route table, the destinations of different propagation routes may be the same, and cannot be modified or deleted.
- You can add static routes for the attachments in a route table. The destinations of static routes in a table must be unique, and can be modified or deleted.
- If a static route and a propagation route in the same route table happen to use the same destination, the static route takes effect first.
- Add at least two propagations. A propagation is required for each protected VPC you add.
- Select the route table (er-RT2) to be connected to the firewall. Click the Associations tab and click Create Association.
- Modify VPC route tables. Point the route of VPC1 to VPC2 and the route of VPC2 to VPC1.
- Return to the Enterprise Router page. In the navigation pane on the left, choose .
- In the Name/ID column, click the route table name of a VPC. The Summary page is displayed.
- Click Add Route and configure parameters as follows:
- Add a route to VPC1 (172.16.0.0/16).
- Destination Type: Select IP address.
- Destination: 172.18.0.0/16
- Next Hop Type: Enterprise Router
- Add a route to VPC2 (172.18.0.0/16).
- Destination Type: Select IP address.
- Destination: 172.16.0.0/16
- Next Hop Type: Enterprise Router
- Add a route to VPC1 (172.16.0.0/16).
Step 3: Enable VPC Protection and Verify Communication
- In the navigation pane, choose Assets > Inter-VPC Border Firewalls.
- Click Enable Protection to the right of Firewall Status.
- Click OK.
- Generate traffic. For details, see Verifying Network Connectivity.
- View logs. In the navigation pane, choose . Click the tab and click VPC Border Firewall.
- If a log is generated, CFW is protecting the traffic between VPCs.
- If no logs are recorded, check the configurations of the enterprise router. For details, see Step 2: Configure an Enterprise Router.
Step 4: Configure a Protection Rule and View Outcomes
- In the navigation pane, choose .
- Add three protection rules.
On the Protection Rules tab page, click Add Rule. On the Add Rule page, configure protection information and set other parameters as needed.
- Add a rule to block all traffic.
- Source: Any
- Destination: Any
- Service: Any
- Application: Any
- Protection Action: Block
- Add a rule to allow the traffic from VPC1 to VPC2.
- Source: Select IP address and enter 172.16.0.0/16.
- Destination: Select IP address and enter 172.18.0.0/16.
- Service: Any
- Application: Any
- Action: Allow
- Add a rule to allow the traffic from VPC2 to VPC1.
- Source: Select IP address and enter 172.18.0.0/16.
- Destination: Select IP address and enter 172.16.0.0/16.
- Service: Any
- Application: Any
- Action: Allow
- Add a rule to block all traffic.
- View the rule hits in access control logs.
In the navigation pane, choose Log Audit > Log Query. Click the Access Control Logs tab and click VPC Border Firewall.
References
For details about how to add other protection rules, see Adding a Protection Rule.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot









