Performing a Baseline Check
Scenarios
You can perform a check immediately or schedule it for later.
- Scheduled check: HSS periodically performs baseline checks based on the scheduled check policy you configured. For more information, see Configuring a Baseline Check Policy.
- One-time manual check: You can manually start a baseline check to learn the server security status in real time.
This topic describes how to manually start a baseline check.
Manually Performing a Baseline Check
- Log in to the HSS console.
- Click
 in the upper left corner and select a region or project.
in the upper left corner and select a region or project. - In the navigation pane on the left, choose Risk Management > Baseline Checks.
Figure 1 Baseline checks
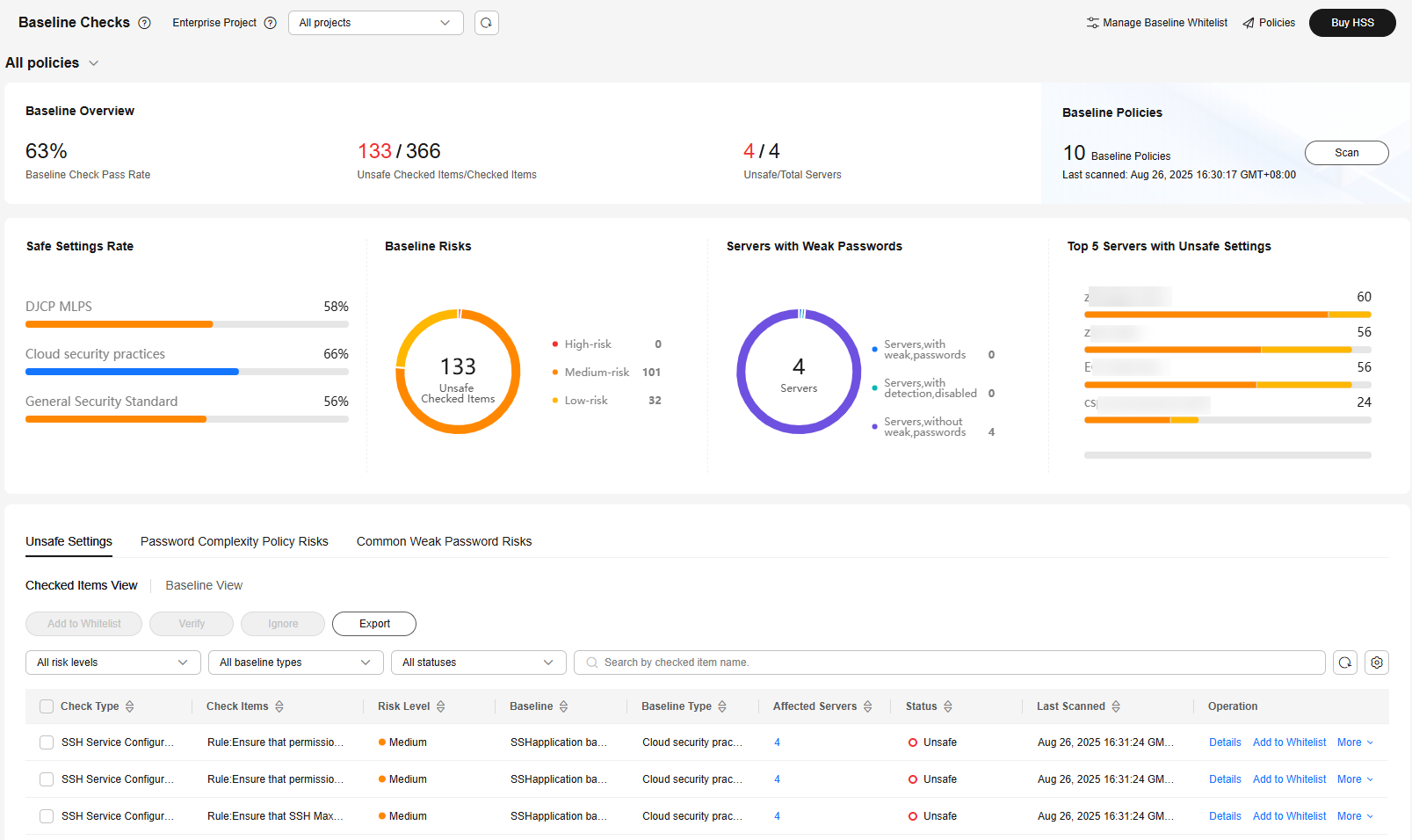
- (Optional) If you have enabled the enterprise project function, select an enterprise project from the Enterprise Project drop-down list in the upper part of the page to view its data.
- In the upper right corner of the page, click Scan.
- Select a policy and click OK.
To view or modify the policy details, click Policies in the upper right corner of the Baseline Checks page. On the displayed page, click Edit in the Operation column of a policy.
- If the time displayed in the Last scanned area under the Baseline Check Policy drop-down list changes to the actual check time, the check has completed.
After a manual check is performed, the button will display Scanning and be disabled. If the check time exceeds 30 minutes, the button will be automatically enabled again. If the time displayed in the Last scanned area becomes the current check time, it indicates the check has completed.
After the check is complete, you can view the check results and handling suggestions by referring to Viewing and Handling Baseline Check Results.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot





