Viewing and Handling Baseline Check Results
Scenarios
You can check for and fix unsafe baseline settings, weak passwords, and insecure password complexity policies on your servers.
If multiple baseline check policies are configured for a server, the system displays only the latest baseline check result.
Constraints
Only the HSS enterprise, premium, WTP, and container editions support baseline configuration checks.
Detection Description
The MySQL baseline detection of Linux OS is based on the MySQL 5 security configuration specifications. If MySQL 8 is installed on your server, the following check items are not displayed in the detection results, because they are discarded in that version. The detection results are displayed only on the server whose MySQL version is 5.
- Rule: Do not set old_passwords to 1.
- Rule: Set secure_auth to 1 or ON.
- Rule: Do not set skip_secure_auth.
- Rule: Set log_warnings to 2.
- Rule: Configure the MySQL binlog clearing policy.
- Rule: The sql_mode parameter contains NO_AUTO_CREATE_USER.
- Rule: Use the MySQL audit plug-in.
Viewing Baseline Check Overview Information
- Log in to the HSS console.
- Click
 in the upper left corner and select a region or project.
in the upper left corner and select a region or project. - In the navigation pane on the left, choose Risk Management > Baseline Checks.
- (Optional) If you have enabled the enterprise project function, select an enterprise project from the Enterprise Project drop-down list in the upper part of the page to view its data.
- On the Baseline Check page, view the check data statistics. For details about the parameters, see the following table.
To view the check results of servers under different baseline check policies, you can switch between baseline check policies.
Figure 1 Baseline checks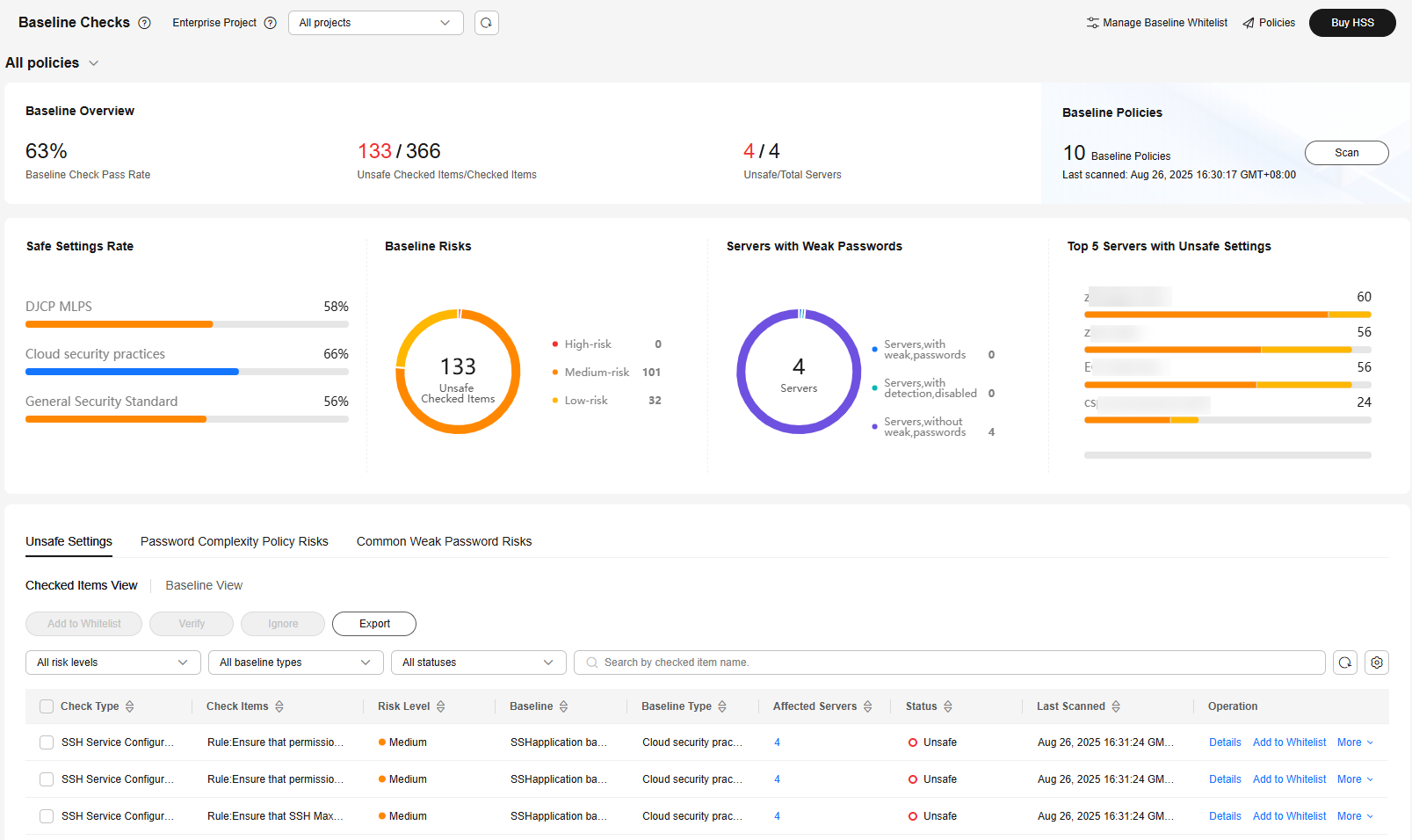
Table 1 Baseline check overview Parameter
Description
Baseline Check Policy
Click
 in the upper left corner of the page to select the baseline check policy whose check results you want to view.
in the upper left corner of the page to select the baseline check policy whose check results you want to view.Scanned Servers
Total number of scanned servers.
Baseline Inspection Pass Rate
Proportion of the number of unsafe check items to the number of checked items.
Unsafe Checked Items/Checked Items
Number of unsafe checked items and the total number of checked items.
Unsafe/Total Servers
Number of servers that fail the check and the total number of servers.
xx Policies
Number of created baseline check policies.
Safe Settings Rate
Proportion of the number of safe checked items to the number of checked items, categorized by baseline type.
Baseline Risks
Number of failed check items and the numbers of high, medium, and low risks.
Servers with Weak Passwords
The weak password statistics of all servers, including the number of servers with weak passwords, number of servers where weak password scans are disabled, and number of servers without weak passwords.
Top 5 Servers with Unsafe Settings
The top 5 servers with the highest risks are displayed. If no high-risk settings exist, the servers with medium or low risks are displayed.
Unsafe Settings
Unsafe settings statistics are displayed in the dimension of Checked Item or Baseline, and suggestions are provided.
Password Complexity Policy Risks
The assets where password complexity policies failed the baseline check are displayed, and suggestions are provided.
Common Weak Password Risks
Unsafe accounts statistics are displayed, and suggestions are provided.
Viewing and Handling Baseline Configuration Risks
You can efficiently check and handle baseline configuration risks in Checked Items View or Baseline View.
- Click the Unsafe Settings tab page and click Checked Items View.
Figure 2 Unsafe settings
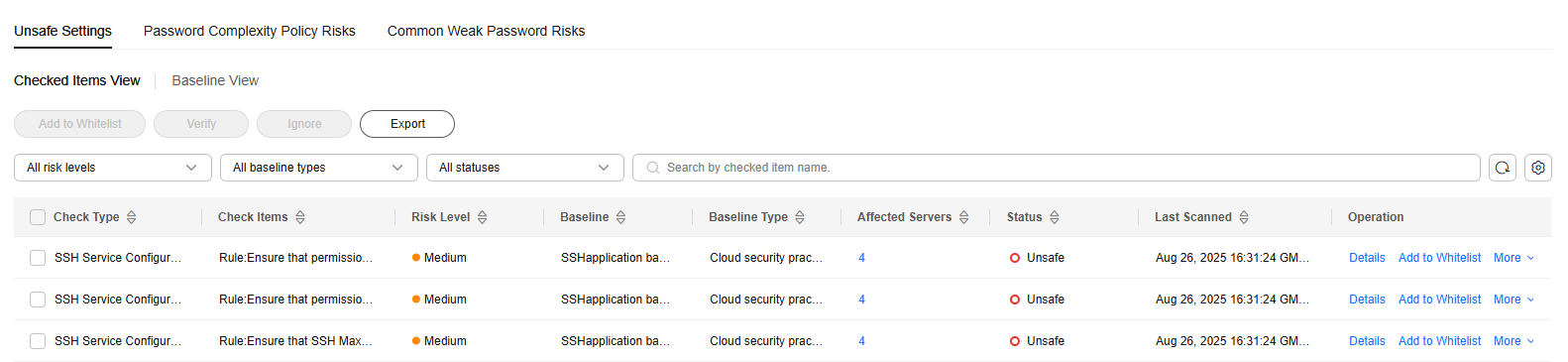
Table 2 Check item parameters Parameter
Description
Check Type
Check item type.
Check Item
Check item name.
Risk Level
Risk level of a check item.
Baseline
Baseline that a check item belongs to.
Baseline Type
Baseline type of a check item.
Affected Servers
Number of servers that failed the check. You can click the number to view the check item description, modification suggestions, and details about the affected servers.
Status
Check item status. The options are as follows:
- Passed: All servers have passed the check on this item.
- Unsafe: At least one server under this item is in Unsafe, Fixing, Verifying, or Failed to fix state.
- Handled: All the servers under this item are in the Passed, Ignored, or Whitelisted state, and at least one server is in the Ignored or Whitelisted state.
Last Scanned
Time when the last scan was performed.
- In the status drop-down list, select Unsafe to filter the check items that failed the check.
- In the Operation column of a check item, click Details. On the check item details page, view the check item description, suggestions, and details about the affected servers.
- Based on the information obtained in the preceding steps, you can handle the servers that failed the check in the following ways:
- Ignoring check results
The ignored check results will always be displayed in the handled list, and will not trigger alarms in later checks.
- Return to the check item list. In the Operation column of a check item, choose . Select multiple check items and click Ignore to ignore them at a time.
You can also go to the check item details page and ignore specific servers.
- In the displayed dialog box, click OK.
- You can filter check items in the Handled state, and click Details in the row of a check item to view the status of the servers that failed the check on this item.
- Return to the check item list. In the Operation column of a check item, choose . Select multiple check items and click Ignore to ignore them at a time.
- Fixing the servers that failed the check
- Rectify the unsafe settings on all affected servers based on the Suggestion on the check item details page.
- Currently, some EulerOS, CentOS 8, and HCE 2.0 baselines support one-click fix. You can click Fix to fix unsafe settings. For check items having configurable parameters, retain their default settings.
- You are advised to fix the settings with high severity immediately and fix those with medium or low severity.
- After the fix is complete, click Verify to verify it.
- If a failed check item has been fixed, you can update its status through verification. The restrictions are as follows:
- Currently, baseline verification is not supported for Windows OSs.
- The agent status of the target server must be online.
- Only one risk item can be verified at a time. Other risk items can be verified only after the current verification is complete.
- Baseline checks are supported for the following Linux OSs: Apache 2, Docker, MongoDB, Redis, MySQL 5, Nginx, Tomcat, SSH, vsftp, CentOS 7, CentOS 8, EulerOS, Debian 9, Debian 10, Debian 11, Red Hat 6, Red Hat 7, Red Hat 8, Ubuntu 12, Ubuntu 14, Ubuntu 16, Ubuntu 18, SUSE 12, SUSE 15, HCE 1.1, and HCE 2.0.
- Click OK to start the verification.
- On the check item details page, check the status of each affected server.
The status changes to Verifying. The system starts automatic verification. After the verification is complete, check the status. If the status is Passed, the fix is successful.
- Rectify the unsafe settings on all affected servers based on the Suggestion on the check item details page.
- Whitelisting check results
After a check result is whitelisted, it will always be displayed in the whitelist management list, and will not be checked in later baseline checks.
- Click Add to Whitelist in the Operation column of a check item. Select multiple check items and click Ignore above the list to ignore them at a time.
You can also go to the check item details page and whitelist specific servers.
- On the Add to Whitelist page, confirm the server information, configure Add to global whitelist as needed, and add remarks.
To exclude the whitelisted items from checks for all servers, select Add to global whitelist.
- Click OK.
To check whitelisted items, return to the Baseline Checks page and click Manage Baseline Whitelist in the upper right corner. For more information, see Managing the Baseline Whitelist.
- Click Add to Whitelist in the Operation column of a check item. Select multiple check items and click Ignore above the list to ignore them at a time.
- Ignoring check results
- Click the Unsafe Settings tab to view the asset baseline risks. For more information, see Table 3.
Figure 3 Viewing unsafe settings
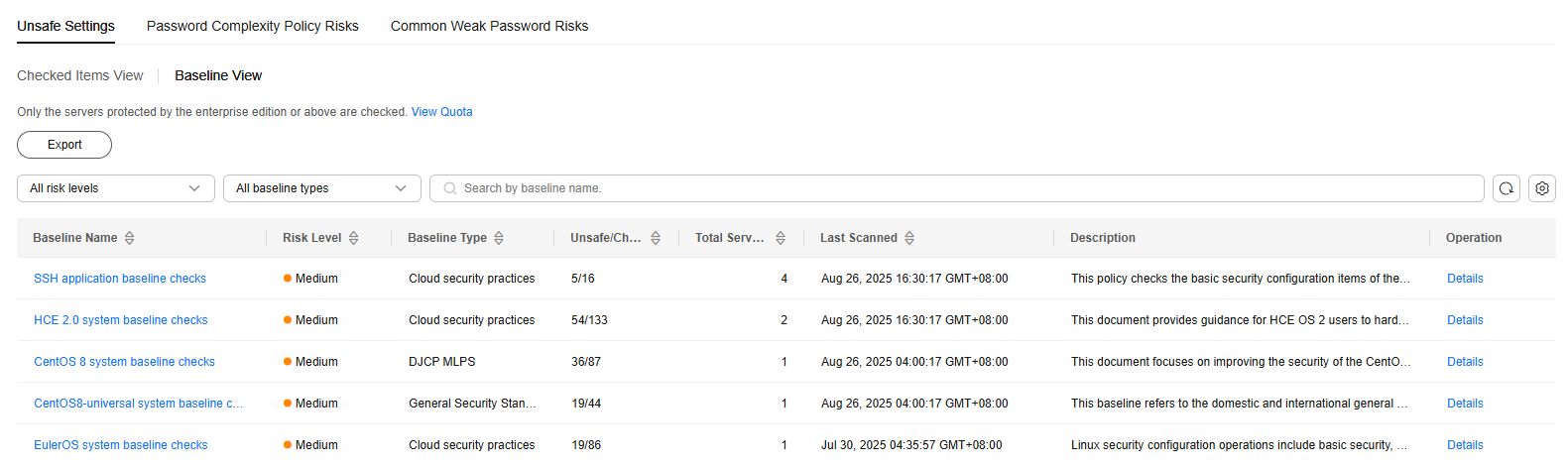
Table 3 Baseline parameters Parameter
Description
Baseline Name
Baseline name.
Risk Level
Level of a detection result.
- High
- Low
- Medium
- Secure
Baseline Type
Baseline type.
- Cloud security practices
- DJCP MLPS
- General Security Standard
Unsafe Checked Items/Checked Items
Number of unsafe checked items and the total number of checked items.
Scanned Servers
Total number of servers scanned against a baseline.
Last Scanned
Time when the last scan was performed.
Description
Description of a baseline.
- Click the name of a baseline in the list to view the check item details and server check results.
Figure 4 Viewing unsafe settings
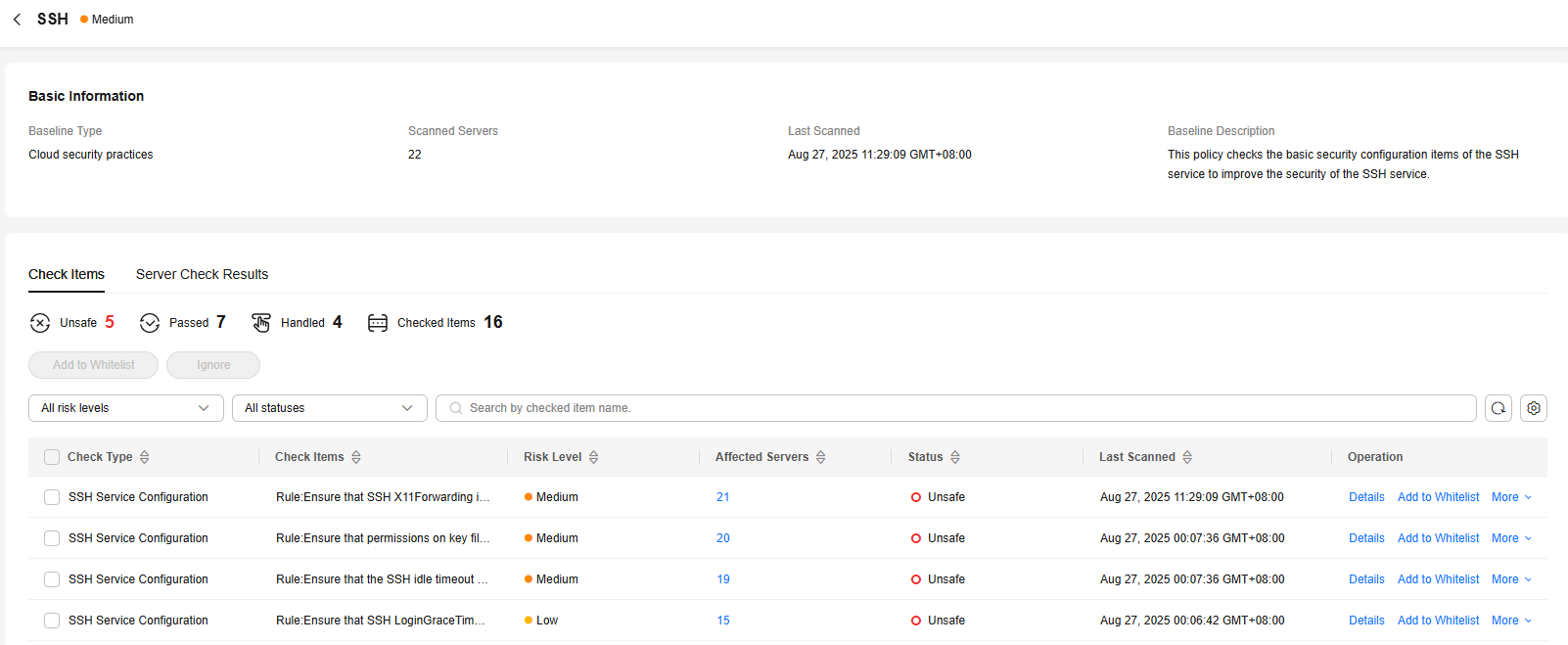
- You can handle the checked items that failed the check in the following ways:
- Ignoring check results
The ignored check results will change to the Handled state, and will not trigger alarms in later checks.
- In the Operation column of a check item, choose . Select multiple check items and click Ignore to ignore them at a time.
You can also click Details to go to the details page and ignore specific servers.
- In the displayed dialog box, click OK.
- In the Operation column of a check item, choose . Select multiple check items and click Ignore to ignore them at a time.
- Fixing the servers that failed the check
- Click View Details in the Operation column of a check item.
- View the check item details, suggestions, and affected servers, and fix the unsafe settings on all the affected servers based on the suggestions.
- Currently, some EulerOS, CentOS 8, and HCE 2.0 baselines support one-click fix. You can click Fix in the Operation column to fix server settings. For check items having configurable parameters, retain their default settings.
- You are advised to fix the settings with high severity immediately, and then fix those with medium or low severity as needed.
- After the fix is complete, click Verify to verify it.
If a failed check item has been fixed, you can update its status through verification. The restrictions are as follows:
- Currently, baseline verification is not supported for Windows OSs.
- The agent status of the target server must be online.
- Only one risk item can be verified at a time. Other risk items can be verified only after the current verification is complete.
- Baseline checks are supported for the following Linux OSs: Apache 2, Docker, MongoDB, Redis, MySQL 5, Nginx, Tomcat, SSH, vsftp, CentOS 7, CentOS 8, EulerOS, Debian 9, Debian 10, Debian 11, Red Hat 6, Red Hat 7, Red Hat 8, Ubuntu 12, Ubuntu 14, Ubuntu 16, Ubuntu 18, SUSE 12, SUSE 15, HCE 1.1, and HCE 2.0.
- Click OK to start the verification.
- On the check item details page, check the status of the item.
The status changes to Verifying. The system starts automatic verification. After the verification is complete, check the status. If the status is Passed, the fix is successful.
- Whitelisting check results
After a check result is whitelisted, it will always be displayed in the whitelist management list, and will not be checked in later baseline checks.
- Click Add to Whitelist in the Operation column of a check item. Select multiple check items and click Ignore above the list to ignore them at a time.
You can also go to the check item details page and whitelist specific servers.
- On the Add to Whitelist page, confirm the server information, configure Add to global whitelist as needed, and add remarks.
To exclude the whitelisted items from checks for all servers, select Add to global whitelist.
- Click OK.
To check whitelisted items, return to the Baseline Checks page and click Manage Baseline Whitelist in the upper right corner. For more information, see Managing the Baseline Whitelist.
- Click Add to Whitelist in the Operation column of a check item. Select multiple check items and click Ignore above the list to ignore them at a time.
- Ignoring check results
Checking and Handling Password Complexity Policy Risks
- Click the Password Complexity Policy Risks tab to view the risk statistical items and handling suggestions. For more information, see Table 4.
Figure 5 Viewing password complexity policy risks
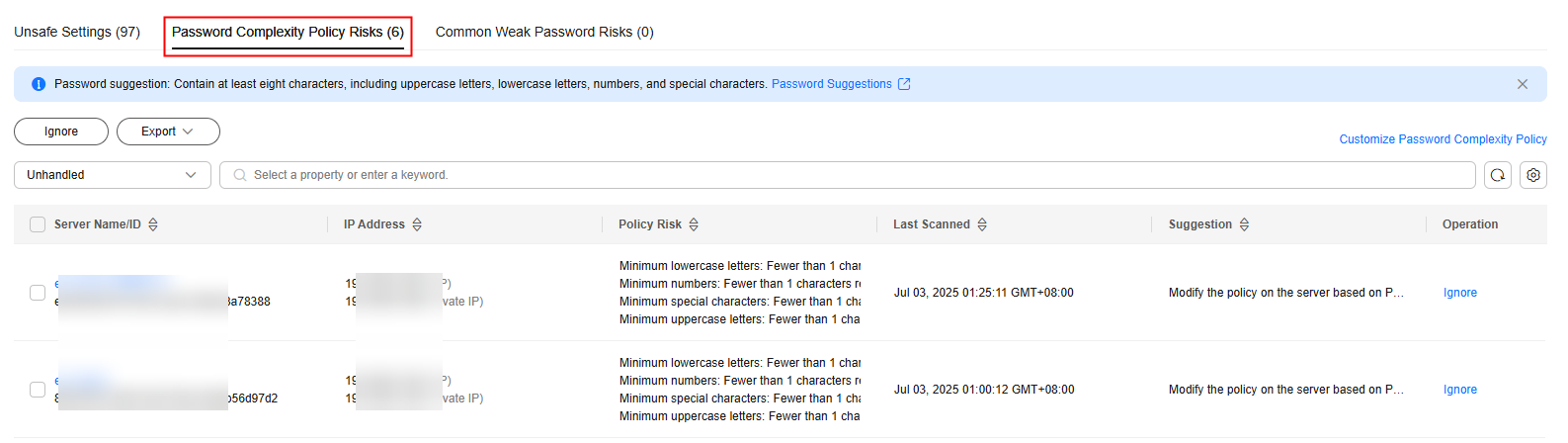
Table 4 Parameters for password complexity policy risks Parameter
Description
Server Name/ID
The name and ID of a checked server.
IP Address
The EIP and private IP address of a checked server.
Policy Risk
The password complexity policy settings that do not meet security requirements.
Last Scanned
Last time when the password complexity policy was checked.
Suggestion
Suggestions for modifying the password complexity policy.
- Handle password complexity policy check results.
- Modifying the password complexity policy
- Modify the password complexity policy on the server based on the Suggestion column in the check result.
- To monitor the password complexity policy on a Linux server, install the Pluggable Authentication Modules (PAM) on the server. For details, see How Do I Install a PAM in a Linux OS?
- For details about how to modify the password complexity policy on a Linux server, see How Do I Install a PAM and Set a Proper Password Complexity Policy in a Linux OS?
- For details about how to modify the password complexity policy on a Windows server, see How Do I Set a Secure Password Complexity Policy in a Windows OS?
- Save the modification. Click Scan in the upper part of the Baseline Checks page to verify the modification.
If you do not perform a manual verification, HSS will automatically check the settings at 00:00:00 the next day.
- Modify the password complexity policy on the server based on the Suggestion column in the check result.
- Ignoring password complexity policy check results
You can view the ignored detection results on the Ignored tab page.
- Ignoring a single result
In the Operation column of a server scan result, click Ignore.
- Batch ignoring records
Select scan results and click Ignore in the upper left corner of the list. Up to 200 results can be ignored at a time.
Figure 6 Ignoring multiple results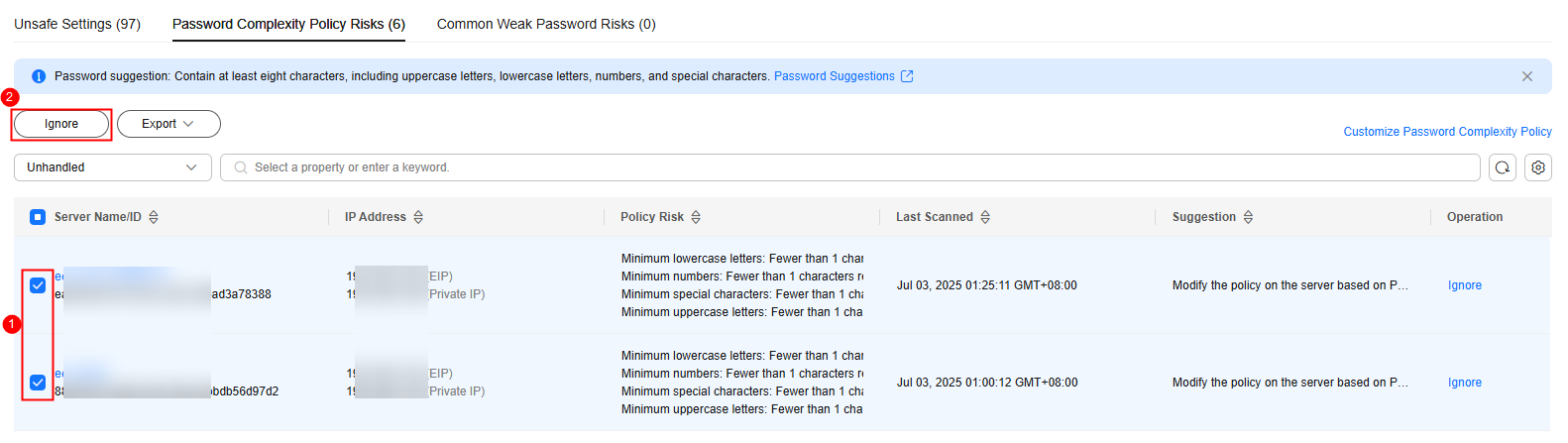
- Ignoring all results
Click Ignore in the upper left corner of the list. Up to 1000 password complexity policy check results can be ignored at a time.
Figure 7 Ignoring all results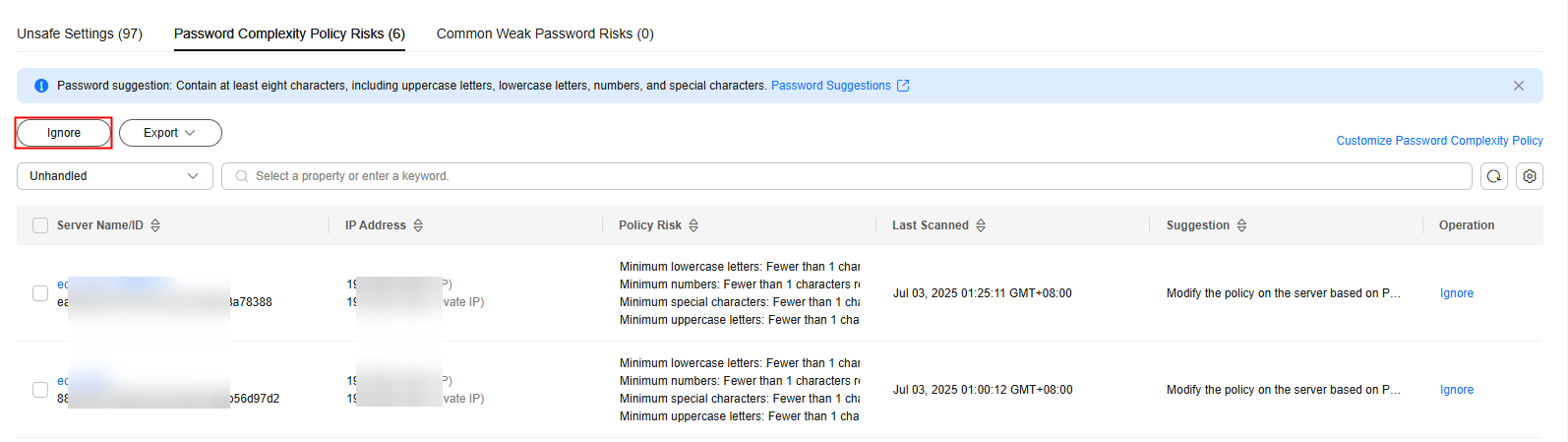
- Ignoring a single result
- Modifying the password complexity policy
Viewing and Handling Common Weak Password Risks
- Click the Common Weak Password Risks tab to view the statistics of weak passwords on the server. For more information, see Table 5.
Figure 8 Viewing common weak password risks
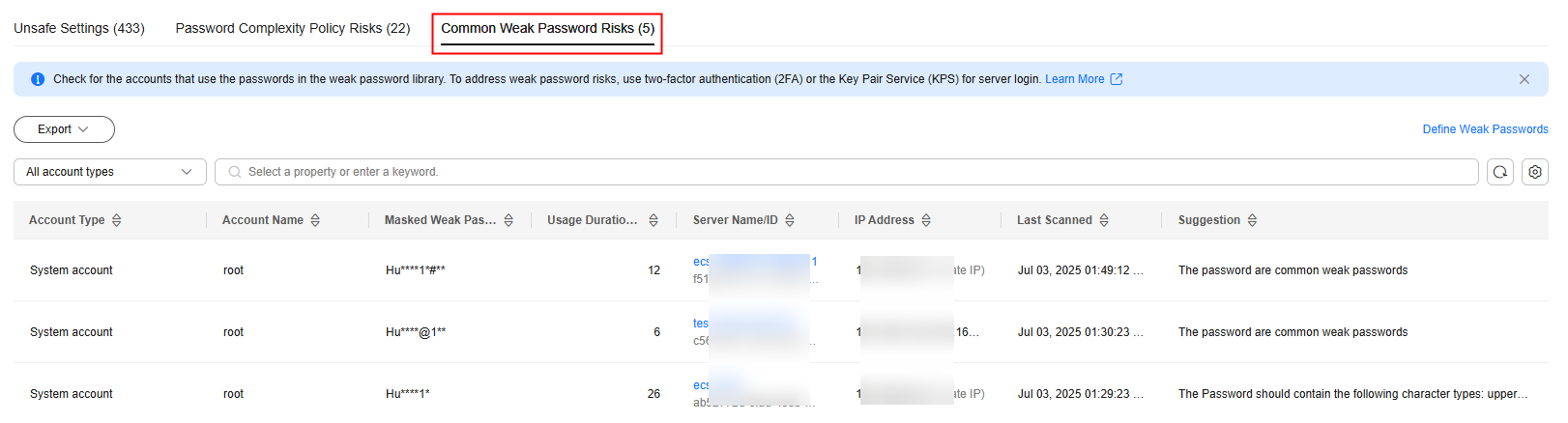
Table 5 Parameters for common weak password risks Parameter
Description
Account Type
Type of an account.
Account Name
Accounts identified with weak passwords.
Masked Weak Password
Masking result of a weak password. The rules for displaying masked weak passwords are as follows:
- ******** indicates that the password length is less than 8.
- ***a**** indicates that the password contains only lowercase letters.
- ***B*** indicates that the password contains only uppercase letters.
- **a**B** indicates that the password contains only uppercase and lowercase letters.
- **a**A***@**1** indicates that the password is a common weak password.
Usage Duration (Days)
Duration a weak password is used.
Server Name/ID
Name and ID of the server where a weak password is used.
IP Address
The EIP and private IP address of a server.
Last Scanned
Time when the last scan completed.
Suggestion
Suggestion for changing weak passwords. You can check why the password is regarded insecure and set a strong password based on the suggestion.
- Log in to the server and change the weak password.
- To enhance server security, you are advised to modify the accounts with weak passwords in a timely manner, such as SSH accounts.
- To protect internal data of your server, you are advised to modify software accounts that use weak passwords, such as MySQL accounts and FTP accounts.
- A password should contain more than eight characters, including uppercase letters, lowercase letters, digits, and special characters.
- After the weak password is changed, perform a manual check in the upper part of the Baseline Checks page to verify the result.
If you do not perform a manual verification, HSS will automatically check the settings at 00:00:00 the next day.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot





