What Are the Differences Between IAM and Enterprise Project Management?
Enterprise Project Management (EPS) allows you to hierarchically manage resources with enterprise projects to align with your organizational structure. It includes enterprise project, personnel, accounting, and application management.
Identity and Access Management (IAM) is an identity management service that provides identity authentication, permissions management, and access control.
Similar to IAM, EPS can manage personnel and assign permissions. Different from IAM, EPS can manage accounting and applications. EPS provides more refined resource authorization than IAM. It is recommended that medium- and large-sized enterprises use EPS.
For more information about IAM functions, see the Identity and Access Management.
Detailed Differences
- Enabling method
- IAM is an identity management service. It is free of charge, and you can use it immediately after signing up for Huawei Cloud.
- EPS is a resource management service.You need to enable it after you sign up for Huawei Cloud. For details, see Enabling Enterprise Center and Enabling the Enterprise Project Function.
EPS is free of charge. You only need to pay for your resources.
- Resource isolation
- IAM allows you to create multiple projects in a region for resource isolation. An IAM project can contain resources of only one region. If you assign permissions based on IAM projects, users with related permissions can access all resources in a specific project.
- EPS enables you to create projects with isolated resources, with each project encompassing resources from multiple regions. Additionally, it facilitates authorization of specific cloud resources. For instance, you can add a particular ECS to an enterprise project and authorize access that allows specific users to manage only that ECS.
- Supported services
- See Supported Cloud Services.
- For details about the cloud services supported by EPS, see Supported Cloud Services.
Authentication Process
When a user initiates an access request, the system authenticates the request based on the actions in the policies that have been attached to the group to which the user belongs. The following figure shows the authentication process.
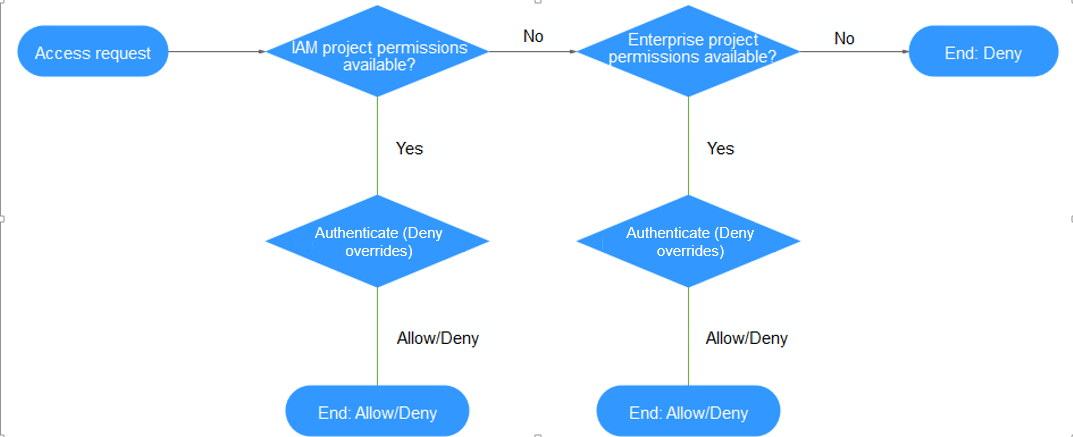
- A user initiates an access request.
- The system checks actions in IAM-project-based policies.
- If a matched Allow or Deny action is found, the system returns an authentication result (Allow or Deny), and the authentication finishes.
- If no matched actions are found in IAM project policies, the system continues to check actions in enterprise-project-based policies.
- If a matched Allow or Deny action is found, the system returns an authentication result (Allow or Deny), and the authentication finishes.
- If no matched actions are found, the system returns a Deny, and the authentication finishes.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot





