Default Security Groups and Rules
- The default security group is named default and to ensure it is never confused with custom groups, the name cannot be changed.
- The default security group cannot be deleted, but you can modify its rules or add rules to it.
- The default security group allows instances in the security group to communicate with each other and denies all external requests. To allow access to an instance associated with this security group, you can add rules to allow access over given ports by referring to Remotely Logging In to an ECS from a Local Server.
- If your service has different security requirements on instances for different purposes, you can create security groups and associate these instances with different security groups accordingly.

You can use security groups free of charge.
When you create an ECS for the first time, the system automatically creates the Sys-FullAccess and Sys-WebServer security groups.
Default Security Group Rules
- Inbound rules control incoming traffic to instances in the default security group. The instances can communicate with each other but cannot be accessed from external networks.
- Outbound rules allow all traffic from the instances in the default security group to external networks.
Figure 1 shows the default security group.
Table 1 describes the default security group rules.
|
Direction |
Action |
Type |
Protocol & Port |
Source/Destination |
Description |
|---|---|---|---|---|---|
|
Inbound |
Allow |
IPv4 |
All |
Source: default security group (default) |
Allows IPv4 instances in the security group to communicate with each other using any protocol over any port. |
|
Inbound |
Allow |
IPv6 |
All |
Source: default security group (default) |
Allows IPv6 instances in the security group to communicate with each other using any protocol over any port. |
|
Outbound |
Allow |
IPv4 |
All |
Destination: 0.0.0.0/0 |
Allows all traffic from the instances in the security group to any IPv4 address over any port. |
|
Outbound |
Allow |
IPv6 |
All |
Destination: ::/0 |
Allows all traffic from the instances in the security group to any IPv6 address over any port. |
Sys-FullAccess and Sys-WebServer Security Group Rules
- Add the Sys-WebServer security group.
- Add the Sys-FullAccess security group.
|
Direction |
Action |
Type |
Protocol & Port |
Source/Destination |
Description |
|---|---|---|---|---|---|
|
Inbound |
Allow |
IPv4 |
ICMP: All |
Source: 0.0.0.0/0 |
Allows the use of the ping command to test the network connectivity over IPv4 protocols. |
|
Inbound |
Allow |
IPv4 |
All |
Source: current security group (Sys-WebServer) |
Allows instances in the security group to communicate with each other over IPv4 protocols. |
|
Inbound |
Allow |
IPv4 |
TCP: 443 |
Source: 0.0.0.0/0 |
Allows all IPv4 addresses to access websites deployed on ECSs over HTTPS. |
|
Inbound |
Allow |
IPv4 |
TCP: 80 |
Source: 0.0.0.0/0 |
Allows all IPv4 addresses to access websites deployed on ECSs over HTTP. |
|
Inbound |
Allow |
IPv4 |
TCP: 22 |
Source: 0.0.0.0/0 |
Allows all IPv4 addresses to access Linux ECSs over SSH. |
|
Inbound |
Allow |
IPv4 |
TCP: 3389 |
Source: 0.0.0.0/0 |
Allows all IPv4 addresses to access Windows ECSs through the default Windows remote desktop. |
|
Inbound |
Allow |
IPv6 |
All |
Source: current security group (Sys-WebServer) |
Allows instances in the security group to communicate with each other over IPv6 protocols. |
|
Outbound |
Allow |
IPv4 |
All |
Destination: 0.0.0.0/0 |
Allows access from instances in the security group to any IPv4 address over any port. |
|
Outbound |
Allow |
IPv6 |
All |
Destination: ::/0 |
Allows access from instances in the security group to any IPv6 address over any port. |
|
Direction |
Action |
Type |
Protocol & Port |
Source/Destination |
Description |
|---|---|---|---|---|---|
|
Inbound |
Allow |
IPv4 |
All |
Source: current security group (Sys-FullAccess) |
Allows instances in the security group to communicate with each other over IPv4 protocols. |
|
Inbound |
Allow |
IPv6 |
All |
Source: current security group (Sys-FullAccess) |
Allows instances in the security group to communicate with each other over IPv6 protocols. |
|
Inbound |
Allow |
IPv4 |
All |
Source: 0.0.0.0/0 |
Allows all inbound data packets to pass through over IPv4 protocols. |
|
Inbound |
Allow |
IPv6 |
All |
Source address::/0 |
Allows all inbound data packets to pass through over IPv6 protocols. |
|
Outbound |
Allow |
IPv4 |
All |
Destination: 0.0.0.0/0 |
Allows access from instances in the security group to any IPv4 address over any port. |
|
Outbound |
Allow |
IPv6 |
All |
Destination: ::/0 |
Allows access from instances in the security group to any IPv6 address over any port. |
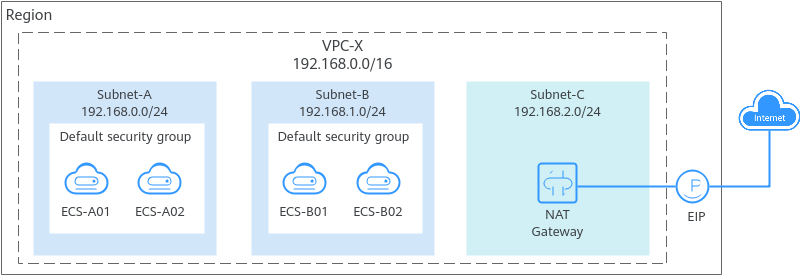
A Default Security Group Example
As shown in Figure 2, VPC-X has three subnets: Subnet-A, Subnet-B, and Subnet-C. ECSs in Subnet-A and Subnet-B have been associated with the default security group. The default security group allows instances in the security group to communicate with each other and denies all external requests. So, the four ECSs (ECS-A01, ECS-A02, ECS-B01, and ECS-B02) can communicate with each other, but they cannot receive traffic from the NAT gateway.
To allow traffic from the NAT gateway, you need to add rules to the default security group or create a security group and associate it with the instances.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot