Initializing a Key
Before using encryption for the first time, you need to initialize keys.
Keys for database encryption and access control include root keys (RKs), data source keys (DSKs), and data encryption keys (DEKs). For details, see Initializing a Key.
|
Type |
Description |
|---|---|
|
Root key (RK) |
Generated after a key is initialized. It is not exposed externally. |
|
Data source key (DSK) |
Generated when a data source is added. It is encrypted by RK for storage. |
|
Data encryption key (DEK) |
Generated during initialization when an encryption task is added. It is encrypted by DSK for storage. |
Procedure
- Log in to database encryption and access control.
- In the navigation pane on the left, choose Key Management > Key Configuration.
- Click Initialize Key. In the displayed dialog box, enter the security password and click OK.
- In the password verification dialog box, enter the security password and click Confirm.
For details about how to change the security password, see Changing the Security Password.
- In the Initialize Key dialog box, set the key sources. For details about the parameters, see Table 2.
Figure 1 Initializing a key
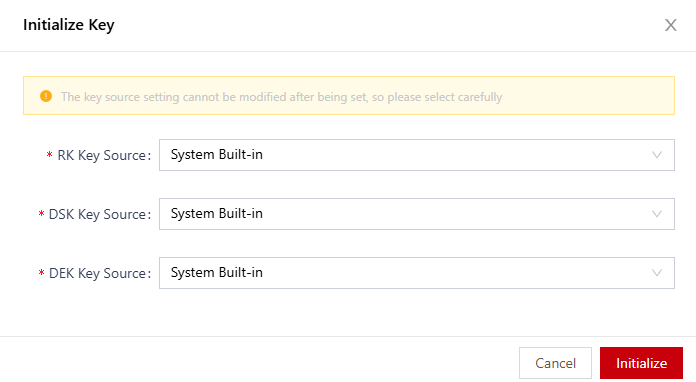
Table 2 Initializing a key Parameter
Description
RK Key Source
RK source. The following sources are supported:- System Built-in: fixed key built in the system, which is used only for tests.
- KEY_Service: key platform connected to the system.
For details about how to configure a key platform, see Interconnecting with KMS.
After the configuration, select a platform vendor.
NOTE:KMS requires the KMS CMKFullAccess permission.
DSK Key Source
DSK source. The following sources are supported:- System Built-in: fixed key built in the system, which is used only for tests.
- KEY_Service: key platform connected to the system.
For details about how to configure the key platform, see Interconnecting with KMS.
After the configuration, select a platform vendor.NOTE:KMS requires the KMS CMKFullAccess permission.
DEK Key Source
DEK source. The following sources are supported:- System Built-in: fixed key built in the system, which is used only for tests.
- KEY_Service: key platform connected to the system.
For details about how to configure the key platform, see Interconnecting with KMS.
After the configuration, select a platform vendor.
NOTE:KMS requires the KMS CMKFullAccess permission.
- Click Initialize.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot





