Using Linux BIND for DNS Resolution in a Hybrid Cloud
Scenarios
DNS resolution relies on domain name servers (DNS servers). DNS servers map IP addresses and domain names to domain names in private or public networks using a built-in database.
In a single environment (for example, a local environment), DNS resolution is relatively simple because the resolution process is within the same network. However, in a hybrid cloud environment, domain name resolution between the local and cloud environments is more complex because the two environments are completely isolated. As a result, local VMs (pointing to the self-built DNS server) may fail to access cloud services managed by Huawei integrated DNS, and ECSs (pointing to the self-built server) in the cloud environment may fail to access cloud services. To avoid this issue, you can configure advanced settings for domain name resolution.
In this practice, you can configure conditional forwarders for DNS servers deployed using Linux BIND to forward DNS queries received by Huawei Cloud service endpoints to Huawei integrated DNS for further resolution and response. You can:
- Use VPC peering connections and VPN connections to allow resources in a multi-account environment to communicate with each other.
- Use Linux BIND to deploy the active and standby DNS servers in a multi-account environment for DNS resolution.
- Configure conditional forwarders for a self-built DNS server to forward the requests for resolving domain names of Huawei Cloud services to Huawei integrated DNS for resolution.
Solution
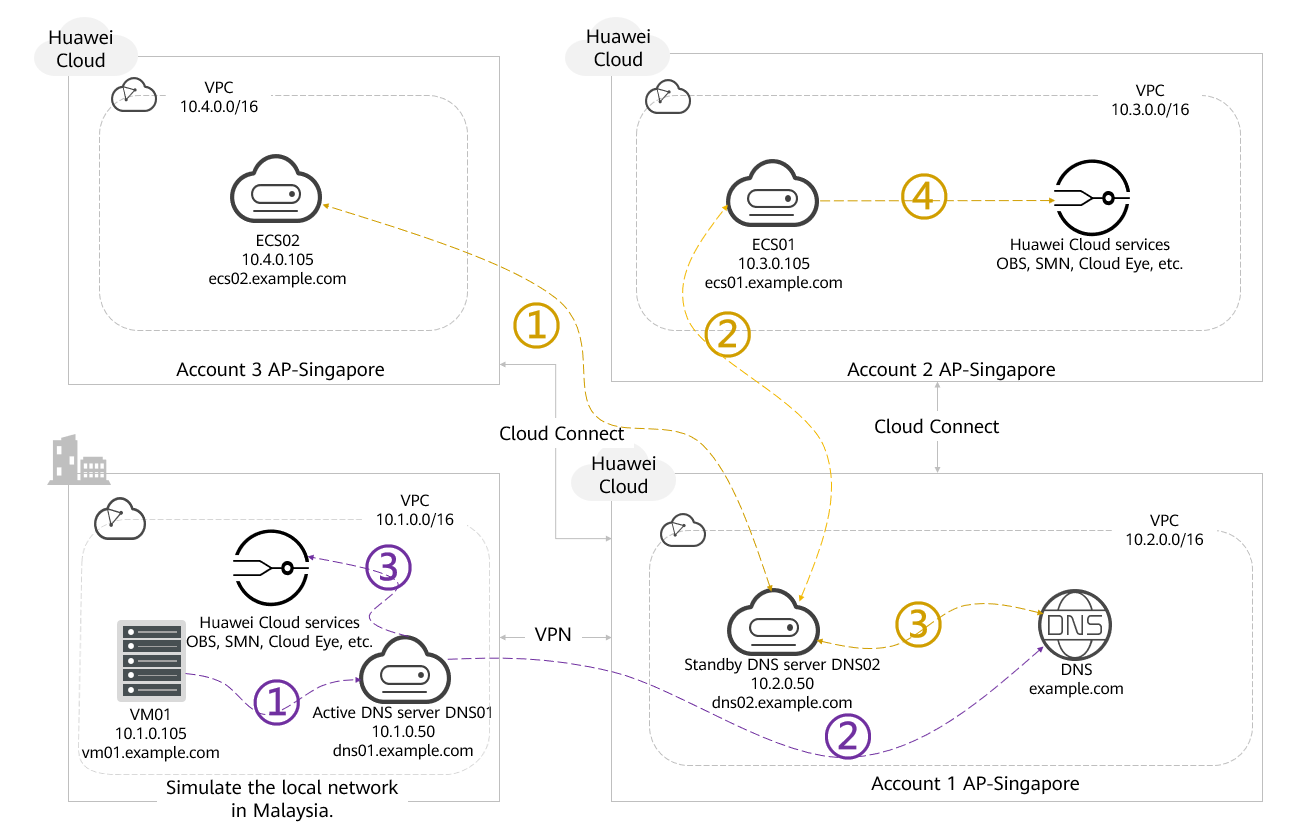
The cloud environments in Malaysia and Singapore are used to demonstrate DNS resolution using Linux BIND in a hybrid cloud.
- A VPN connection is established between Malaysia and Singapore to allow resources to communicate across regions.
- The sub-accounts in Singapore are interconnected through VPC peering connections. Routes are also configured to achieve the same purpose.
- The active DNS server is set up in Malaysia using Linux BIND, while the standby DNS server is set up in an account in Singapore. The standby DNS server in Singapore is a read replica replicated from the active DNS server in Malaysia. Any update in zone files needs to be configured on the active DNS server, and is automatically synchronized to the standby DNS server by increasing the serial number in zone files.
With the preceding configurations, we can use Linux BIND for DNS resolution in a hybrid cloud. VMs in the local environment (Malaysia) will point to the active DNS server as the preferred DNS and the standby DNS server as the alternate DNS. ECSs in the cloud (Singapore) will point to the standby DNS server as the preferred DNS and the active DNS server as the alternate DNS. Both the active and standby DNS servers need to be configured to forward requests to Huawei integrated DNS. When VMs or ECSs access Huawei Cloud services (such as OBS and SMN), the endpoints of these services can be resolved. For example, if ECS01 accesses the OBS service, it sends DNS queries to DNS02. DNS02 identifies that the requested domain name is hosted by another name server and forwards the queries to Huawei integrated DNS for further resolution and response.
- Users can fully utilize Linux BIND to resolve domain names in the hybrid cloud.
In the hybrid cloud, the two DNS servers are configured as the active DNS server (DNS01) and standby DNS server (DNS02) to back up DNS records between the local and cloud environments.
Note that both DNS servers are configured with the redundancy function. DNS02 is a read replica. All zone configuration updates can be performed only on DNS01, and DNS02 is automatically updated based on the sequence number change.
- Condition forwarders must be configured on both DNS servers (DNS01 and DNS02) to resolve Huawei Cloud service endpoints.
- All ECSs on the cloud use DNS02 as the active DNS server and DNS01 as the standby DNS server.
- All VMs in the local environment use DNS01 as the active DNS server and DNS02 as the standby DNS server.
If ECS02 in account 3 wants to access ECS01 in account 2, it sends DNS queries to the active DNS server (DNS02). The same process applies to other ECSs on the cloud and local VMs.
- If VM01 in the local environment wants to access the endpoints of Huawei Cloud services (such as OBS, SMN, and Cloud Eye), it sends DNS queries to the active DNS server (DNS01). DNS01 identifies that the requested domain name is hosted on another name server and forwards DNS queries to Huawei integrated DNS for further resolution and response.
- If an ECS on the cloud wants to access the endpoints of Huawei Cloud services (such as OBS, SMN, and Cloud Eye), it sends DNS queries to the active DNS server (DNS02). DNS02 identifies that the requested domain name is hosted on another name server and forwards DNS queries to Huawei integrated DNS for further resolution and response.
In this practice, the IP addresses in the local network and Huawei Cloud are for reference only. In actual applications, deploy the solution based on the actual network plan.
Preparations
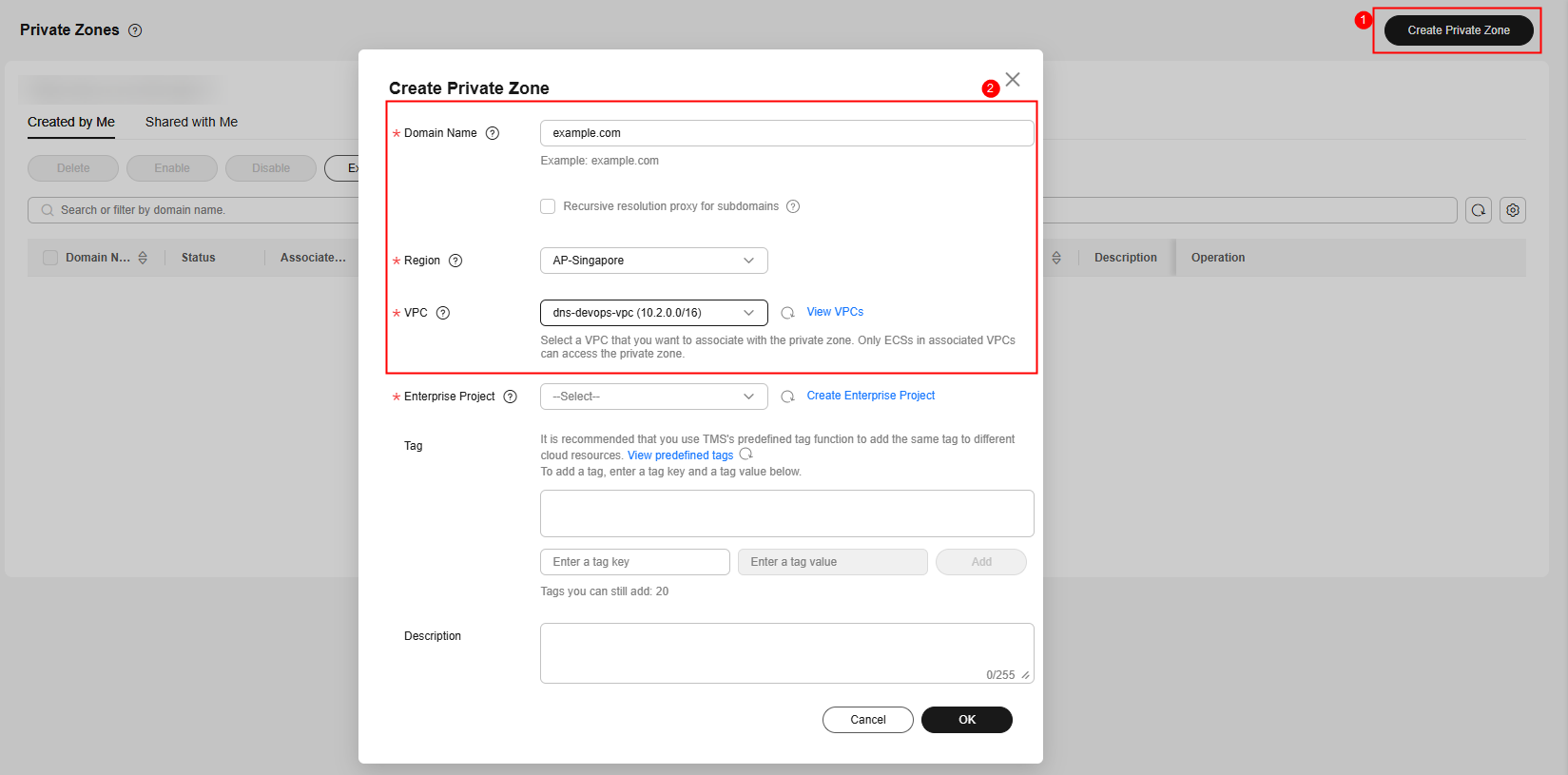
Step 1: Create a Private Zone on Huawei Cloud DNS
- Go to the Private Zones page.
- In the upper right corner of the page, click Create Private Zone.
Figure 2 Creating a private zone
- Click Manage Record Sets in the Operation column. On the Record Sets tab, view and record the private DNS addresses and the values of NS and SOA record sets.
Figure 3 Manage Record Resets
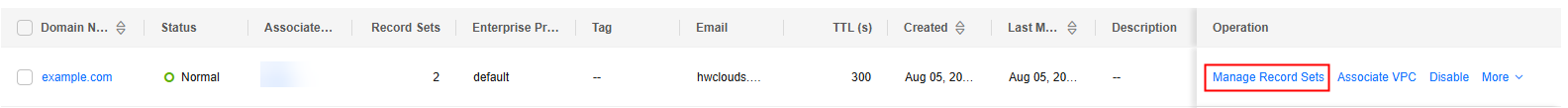 Figure 4 Viewing and recording information
Figure 4 Viewing and recording information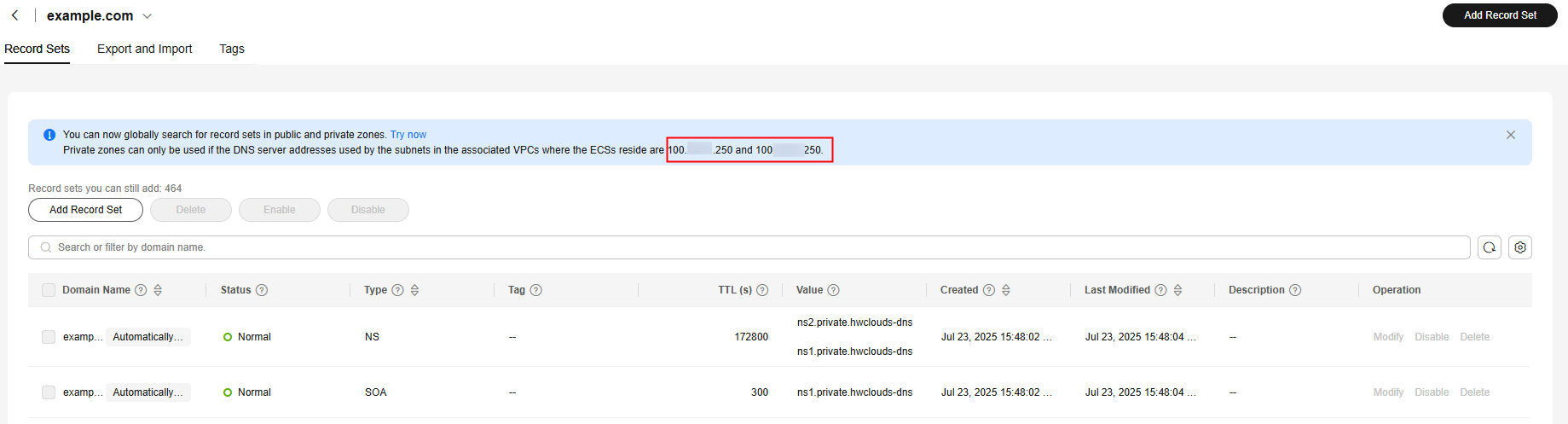
Step 2: Configure the Active DNS Server (DNS01)
- Remotely log in to your active DNS server and run the following commands to update the server and install BIND:
yum update -y yum install bind-utils
- Back up the original name.conf file and edit it.
mv /etc/named.conf /etc/named.conf.orig vim /etc/named.conf
- Modify the settings in the named.conf file based on the environment requirements.
To resolve Huawei Cloud service endpoints (such as OBS, Cloud Eye, and SMN), configure forwarders in the named.conf file to enable conditional forwarding for BIND. The following fields marked in bold need to be modified.
// Provided by Red Hat bind package to configure the ISC BIND named(8) DNS // server as a caching only nameserver (as a localhost DNS resolver only). // // See /usr/share/doc/bind*/sample/ for example named configuration files. // // See the BIND Administrator's Reference Manual (ARM) for details about the // configuration located in /usr/share/doc/bind-{version}/Bv9ARM.html acl "trusted-recursion" { localhost; localnets; 10.1.0.0/24; 10.2.0.0/24; 10.3.0.0/24; 10.4.0.0/24; }; options { listen-on port 53 { any; }; listen-on-v6 port 53 { ::1; }; directory "/var/named"; dump-file "/var/named/data/cache_dump.db"; statistics-file "/var/named/data/named_stats.txt"; memstatistics-file "/var/named/data/named_mem_stats.txt"; allow-query { any; }; allow-recursion { trusted-recursion; }; allow-query-cache { trusted-recursion; }; /* - If you are building an AUTHORITATIVE DNS server, do NOT enable recursion. - If you are building a RECURSIVE (caching) DNS server, you need to enable recursion. - If your recursive DNS server has a public IP address, you MUST enable access control to limit queries to your legitimate users. Failing to do so will cause your server to become large-scale DNS amplification attacks. Implementing BCP38 within your network would greatly reduce such attack surface */ /* recursion yes; */ dnssec-enable yes; dnssec-validation no; /* Path to ISC DLV key */ bindkeys-file "/etc/named.iscdlv.key"; managed-keys-directory "/var/named/dynamic"; pid-file "/run/named/named.pid"; session-keyfile "/run/named/session.key"; # Setup Huawei Integrated DNS as forwarders forwarders { 100.125.xx.xx; 100.125.xx.xx; }; }; logging { channel default_debug { file "data/named.run"; severity dynamic; }; }; zone "." IN { type hint; file "named.ca"; }; include "/etc/named.rfc1912.zones"; include "/etc/named.root.key"; zone "example.com" { type master; file "dynamic/example.com"; # zone file path allow-transfer { 10.2.0.50; }; notify yes; }; zone "10.in-addr.arpa" in { type master; file "dynamic/10.in-addr.arpa.zone"; allow-transfer { 10.2.0.50; }; notify yes; }; zone "125.100.in-addr.arpa" in { type master; file "dynamic/125.100.in-addr.arpa.zone"; allow-transfer { 10.2.0.50; }; notify yes; }; - Run the following command to create a zone file for the private zone:
vim /var/named/dynamic/db.example.com
Modify the settings based on your environment requirements.
$TTL 300 ; 5 minutes @ IN SOA dns01.example.com. admin.example.com. ( 1 ; Serial 3600 ; Refresh 300 ; Retry 1814400 ; Expire 300 ) ; Negative Cache TTL ; name servers - NS records IN NS dns01.example.com. IN NS dns02.example.com. ; name servers - A records dns01.example.com. IN A 10.1.0.50 dns02.example.com. IN A 10.2.0.50 ; All other A records example.com. IN A 10.1.0.200 www.example.com. IN A 10.1.0.200 ecs01.example.com. IN A 10.3.0.105 ecs02.example.com. IN A 10.4.0.105 vm01.example.com. IN A 10.1.0.105 - Run the following command to create a reverse zone file for 10.in-adr.arpa.zone:
vim /var/named/dynamic/10.in-addr.arpa.zone
Modify the settings based on your environment requirements.
$TTL 86400 ; 1 day @ IN SOA dns01.example.com. admin.example.com. ( 1 ; Serial 7200 ; refresh (2 hours) 7200 ; retry (2 hours) 2419200 ; expire (5 weeks 6 days 16 hours) 86400 ) ; minimum (1 day) @ IN NS dns01.example.com. @ IN NS dns02.example.com. @ IN PTR example.com. dns01 IN A 10.1.0.50 dns01 IN A 10.2.0.50 ecs01 IN A 10.3.0.105 ecs02 IN A 10.4.0.105 vm01 IN A 10.1.0.105 www IN A 10.1.0.200 200.0.1 IN PTR www.example.com. 50.0.1 IN PTR dns01.example.com. 50.0.2 IN PTR dns02.example.com. 105.0.3 IN PTR ecs01.example.com. 105.0.4 IN PTR ecs02.example.com. 105.0.1 IN PTR vm01.example.com. - Run the following command to create a reverse zone file for Huawei integrated DNS 125.100.in-addr.arpa.zone:
vim /var/named/dynamic/125.100.in-addr.arpa.zone
Modify the settings based on your environment requirements. Set the SOA, NS, and PTR values to those recorded in step 3.
$TTL 86400 ; 1 day @ IN SOA ns1.system.hwclouds-dns.com. yiam\.kar\.kar.huawei.com. ( 1 ; Serial 7200 ; refresh (2 hours) 7200 ; retry (2 hours) 2419200 ; expire (5 weeks 6 days 16 hours) 86400 ) ; minimum (1 day) @ IN NS ns2.system.hwclouds-dns.com. @ IN NS ns1.system.hwclouds-dns.com. ns1 IN A 100.125.xx.xx ns2 IN A 100.125.xx.xx 250.1 IN PTR ns2.system.hwclouds-dns.com. 250.128 IN PTR ns1.system.hwclouds-dns.com. - Run the following command to check the syntax of the /etc/name.conf file:
named-checkconf
If no content is returned, the configuration file is valid.
- Run the following command to check the syntax of the zone files:
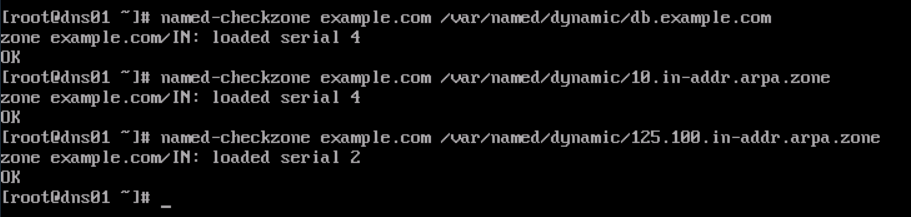
named-checkzone example.com /var/named/dynamic/db.example.com named-checkzone example.com /var/named/dynamic/10.in-addr.arpa.zone named-checkzone example.com /var/named/dynamic/125.100.in-addr.arpa.zone
Figure 5 shows an output example.
- Run the following commands to enable and start BIND:
systemctl enable named systemctl start named
- Back up and update nameserver in the /etc/resolv.conf file.
mv /etc/resolv.conf /etc/resolv.conf.orig vim /etc/resolv.conf
Modify nameserver settings based on your environment requirements.
domain example.com search example.com nameserver 10.1.0.50 nameserver 10.2.0.50
Step 3: Configure the Standby DNS Server (DNS02)
- Remotely log in to your standby DNS server and run the following commands to update the server and install BIND:
yum update -y yum install bind bind-utils
- Back up the original name.conf file and edit it.
mv /etc/named.conf /etc/named.conf.orig vim /etc/named.conf
- Modify the settings in the name.conf file based on your environment requirements.
You also need to configure a forwarder for the standby server for resolving Huawei Cloud service endpoints. The fields to be modified are displayed in bold.
// Provided by Red Hat bind package to configure the ISC BIND named(8) DNS // server as a caching only nameserver (as a localhost DNS resolver only). // // See /usr/share/doc/bind*/sample/ for example named configuration files. // // See the BIND Administrator's Reference Manual (ARM) for details about the // configuration located in /usr/share/doc/bind-{version}/Bv9ARM.html acl "trusted-recursion" { localhost; localnets; 10.1.0.0/24; 10.2.0.0/24; 10.3.0.0/24; 10.4.0.0/24; }; options { listen-on port 53 { any; }; listen-on-v6 port 53 { ::1; }; directory "/var/named"; dump-file "/var/named/data/cache_dump.db"; statistics-file "/var/named/data/named_stats.txt"; memstatistics-file "/var/named/data/named_mem_stats.txt"; allow-query { any; }; allow-recursion { trusted-recursion; }; allow-query-cache { trusted-recursion; }; /* - If you are building an AUTHORITATIVE DNS server, do NOT enable recursion. - If you are building a RECURSIVE (caching) DNS server, you need to enable recursion. - If your recursive DNS server has a public IP address, you MUST enable access control to limit queries to your legitimate users. Failing to do so will cause your server to become large-scale DNS amplification attacks. Implementing BCP38 within your network would greatly reduce such attack surface */ /* recursion yes; */ dnssec-enable yes; dnssec-validation no; /* Path to ISC DLV key */ bindkeys-file "/etc/named.iscdlv.key"; managed-keys-directory "/var/named/dynamic"; pid-file "/run/named/named.pid"; session-keyfile "/run/named/session.key"; # Setup Huawei Integrated DNS as forwarders forwarders { 100.125.xx.xx; 100.125.xx.xx; }; }; logging { channel default_debug { file "data/named.run"; severity dynamic; }; }; zone "." IN { type hint; file "named.ca"; }; include "/etc/named.rfc1912.zones"; include "/etc/named.root.key"; zone "example.com" { type slave; file "slaves/db.example.com"; masters { 10.1.0.50; }; }; zone "1.168.192.in-addr.arpa" in { type slave; file "slaves/10.in-addr.arpa.zone"; masters { 10.1.0.50 }; zone "125.100.in-addr.arpa" in { type slave; file "slaves/125.100.in-addr.arpa.zone"; masters { 10.1.0.50 }; }; - Run the following command to check the syntax of the /etc/name.conf file:
named-checkconf
If no content is returned, the configuration file is valid.
- Run the following commands to enable and start BIND:
systemctl enable named systemctl start named
- Back up and update nameserver in the /etc/resolv.conf file.
mv /etc/resolv.conf /etc/resolv.conf.orig vim /etc/resolv.conf
Modify nameserver settings based on your environment requirements.
domain example.com search example.com nameserver 10.1.0.50 nameserver 10.2.0.50
Step 4: Configure a DNS Server on the Client
- Remotely log in to VM01, ECS01, and ECS02 and run the following commands to update the servers and install BIND:
yum update -y yum install bind bind-utils
- Set the name servers to point to the IP addresses of the DNS servers deployed in Step 2: Configure the Active DNS Server (DNS01) and Step 3: Configure the Standby DNS Server (DNS02).
vim /etc/resolv.conf
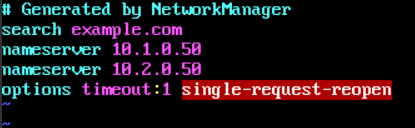
- The nameserver configuration of VM01 is as follows.
Figure 6 nameserver configuration example
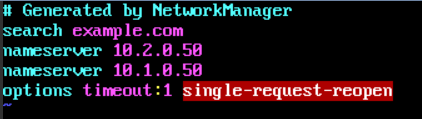
- The nameserver configuration of ECS01 and ECS02 is as follows.
Figure 7 nameserver configuration example
- The nameserver configuration of VM01 is as follows.
Verification
In this section, we will use the IP addresses and domain names configured in the multi-account environment to test network connectivity. The resources of multiple accounts are connected through VPN connections, VPC peering connections, and configured routes. We will also use the nslookup command to test the access to the endpoints of Huawei Cloud services (such as OBS, SMN, and Cloud Eye).
- Run the ping command to test the connectivity between VM01 and ECS01 and between VM01 and ECS02.
- Ping the IP addresses of ECS01 and ECS02 from VM01.
Figure 8 Pinging the IP addresses of ECS01 and ECS02 from VM01
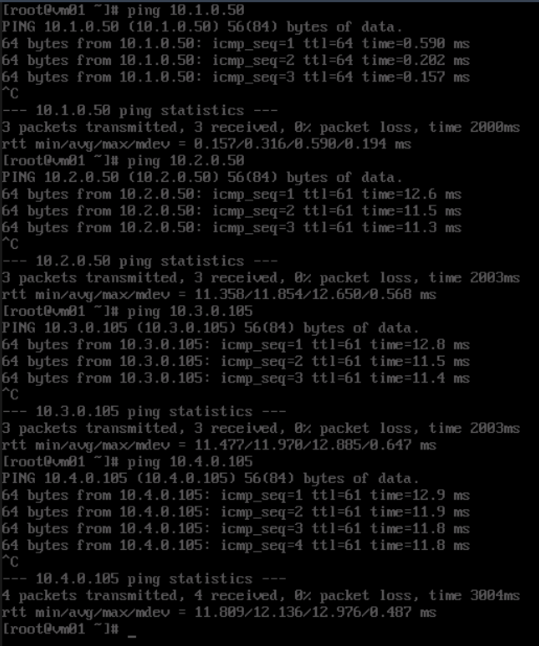
- Ping the domain names of ECS01 and ECS02 from VM01.
Figure 9 Pinging the domain names of ECS01 and ECS02 from VM01
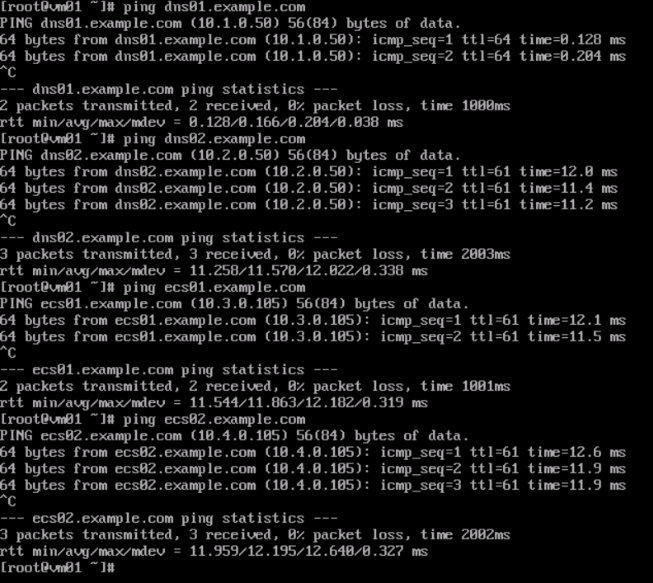
- Test the connectivity between VM01 and Huawei Cloud services.
Figure 10 Accessing the endpoints of Huawei Cloud services from VM01
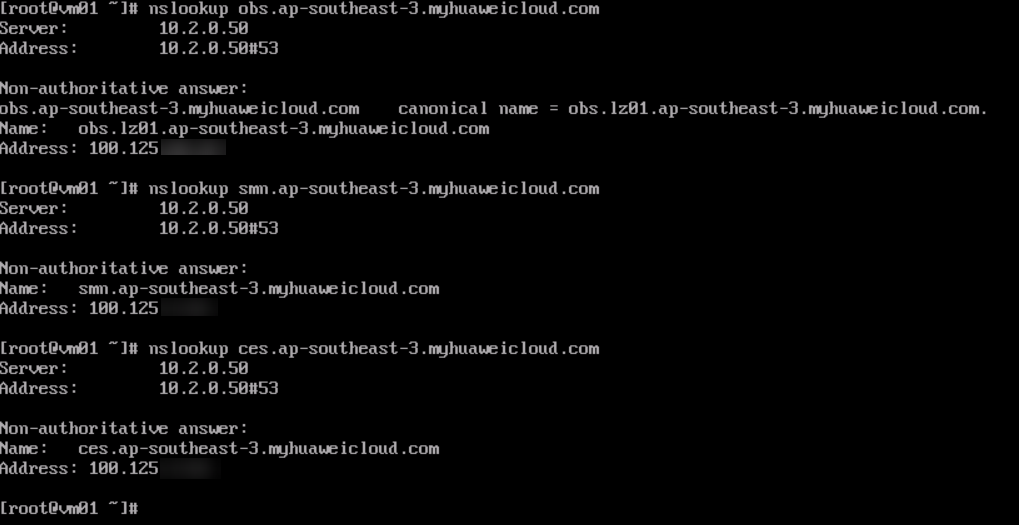
- Ping the IP addresses of ECS01 and ECS02 from VM01.
- Run the ping command to test the connectivity between ECS01 and VM01 and between ECS01 and ECS02.
- Ping the IP addresses of VM01 and ECS02 from ECS01.
Figure 11 Pinging the IP addresses of VM01 and ECS02 from ECS01
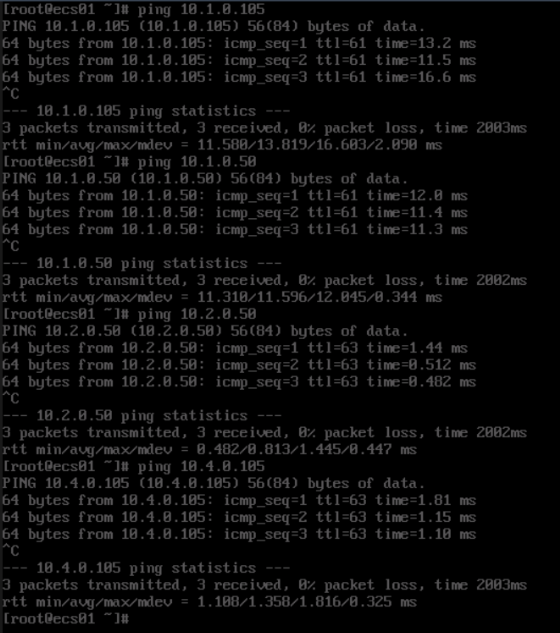
- Ping the domain names of VM01 and ECS02 from ECS01.
Figure 12 Pinging the domain names of VM01 and ECS02 from ECS01
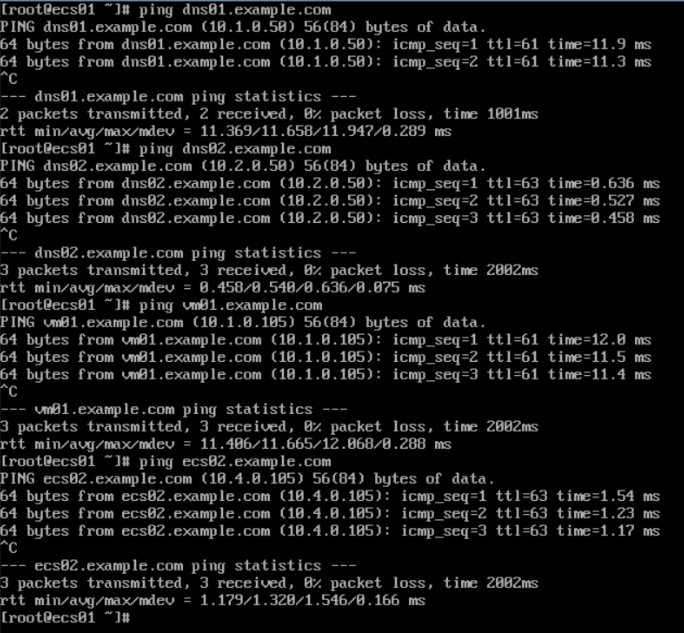
- Test the connectivity between ECS01 and Huawei Cloud services.
Figure 13 Accessing the endpoints of Huawei Cloud services from ECS01
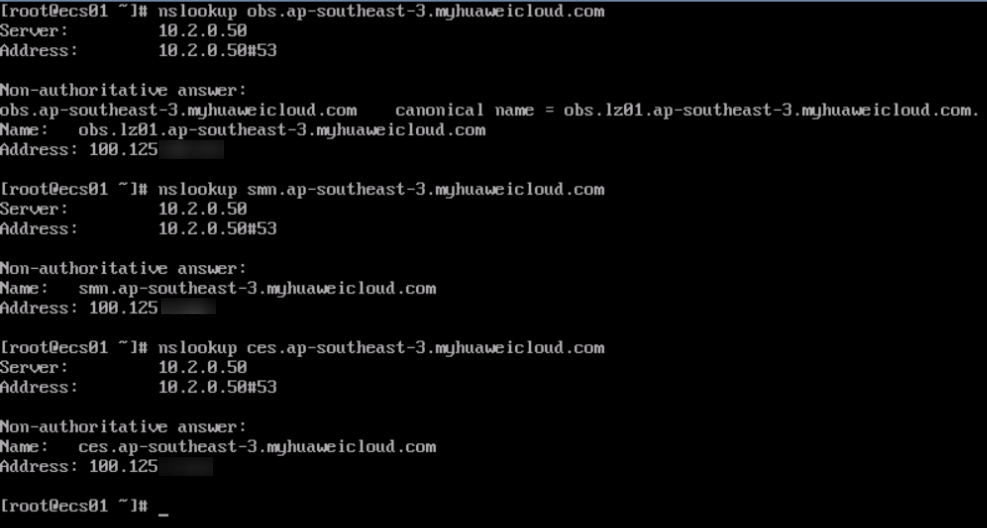
- Ping the IP addresses of VM01 and ECS02 from ECS01.
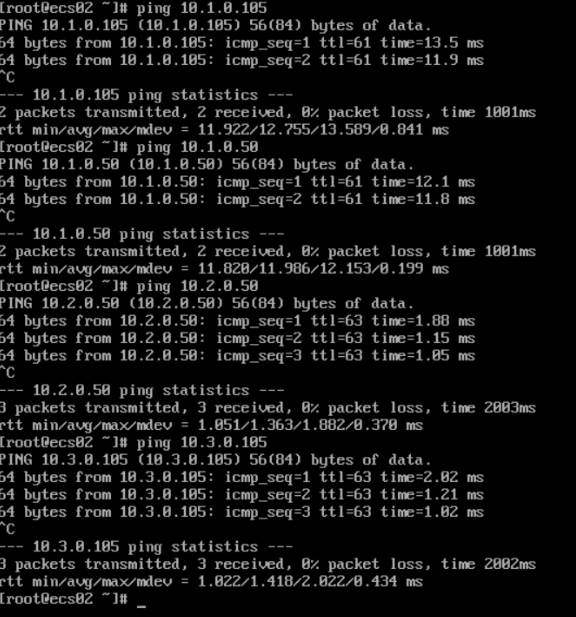
- Run the ping command to test the connectivity between ECS02 and VM01 and between ECS02 and ECS01.
- Ping the IP addresses of VM01 and ECS02 from ECS01.
Figure 14 Pinging the IP addresses of VM01 and ECS02 from ECS01
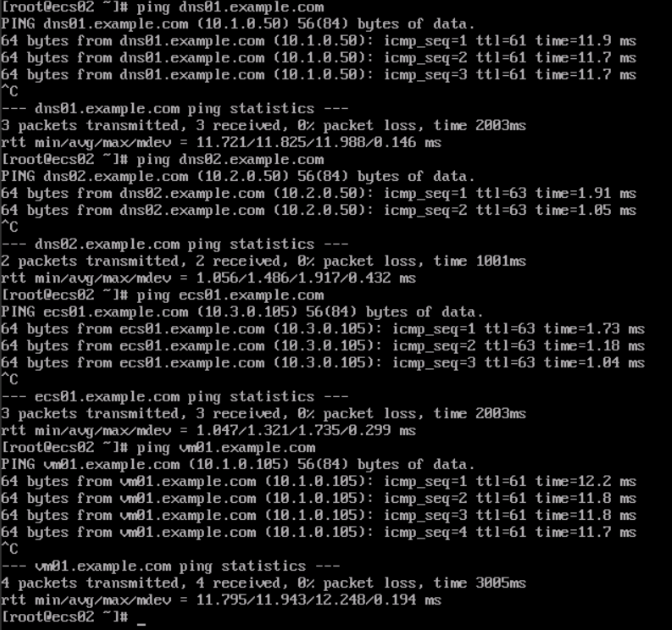
- Ping the domain names of VM01 and ECS01 from ECS02.
Figure 15 Pinging the domain names of VM01 and ECS01 from ECS02
- Test the connectivity between ECS02 and Huawei Cloud services.
Figure 16 Accessing the endpoints of Huawei Cloud services from ECS02
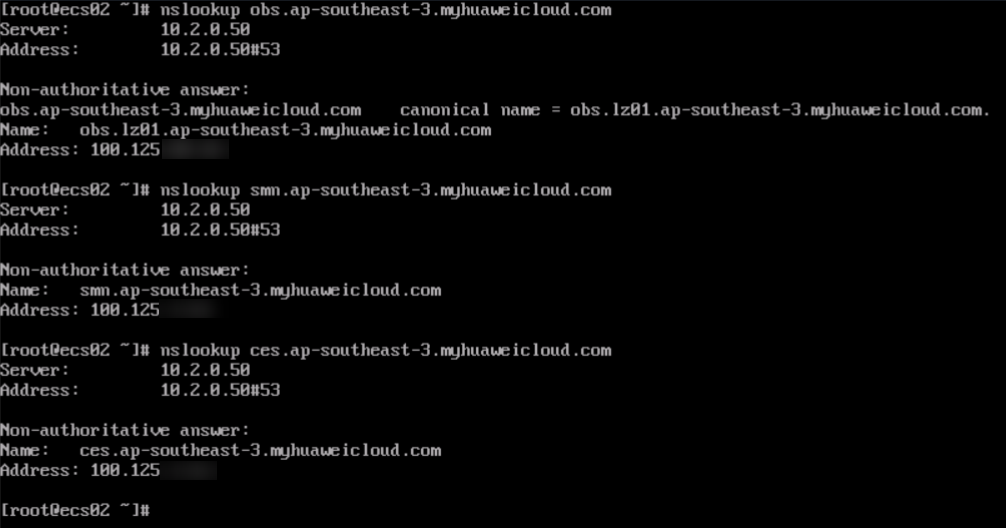
- Ping the IP addresses of VM01 and ECS02 from ECS01.
Summary
In this practice, we learned how to use Linux BIND to deploy primary and secondary DNS servers for DNS resolution in a multi-account environment. We also learned how to deploy DNS servers in a multi-account environment and use AD-integrated DNS servers for DNS resolution. In addition, we have configured the DNS server as a forwarder for Huawei Cloud integrated DNS to resolve endpoints of Huawei Cloud services such as SMN, OBS, and Cloud Eye. This makes it easier to access resources used in any environment.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot