Checking File Change Events
Scenarios
After the HSS professional edition or higher is enabled on a server or container node, HSS monitors the integrity of critical files or directories in real time. Unauthorized file changes will be reported once detected, helping you learn suspicious modifications in time.
Checking File Change Events
- Log in to the HSS console.
- Click
 in the upper left corner and select a region or project.
in the upper left corner and select a region or project. - In the navigation pane, choose . Check the file changes on servers or containers.
Figure 1 File changes
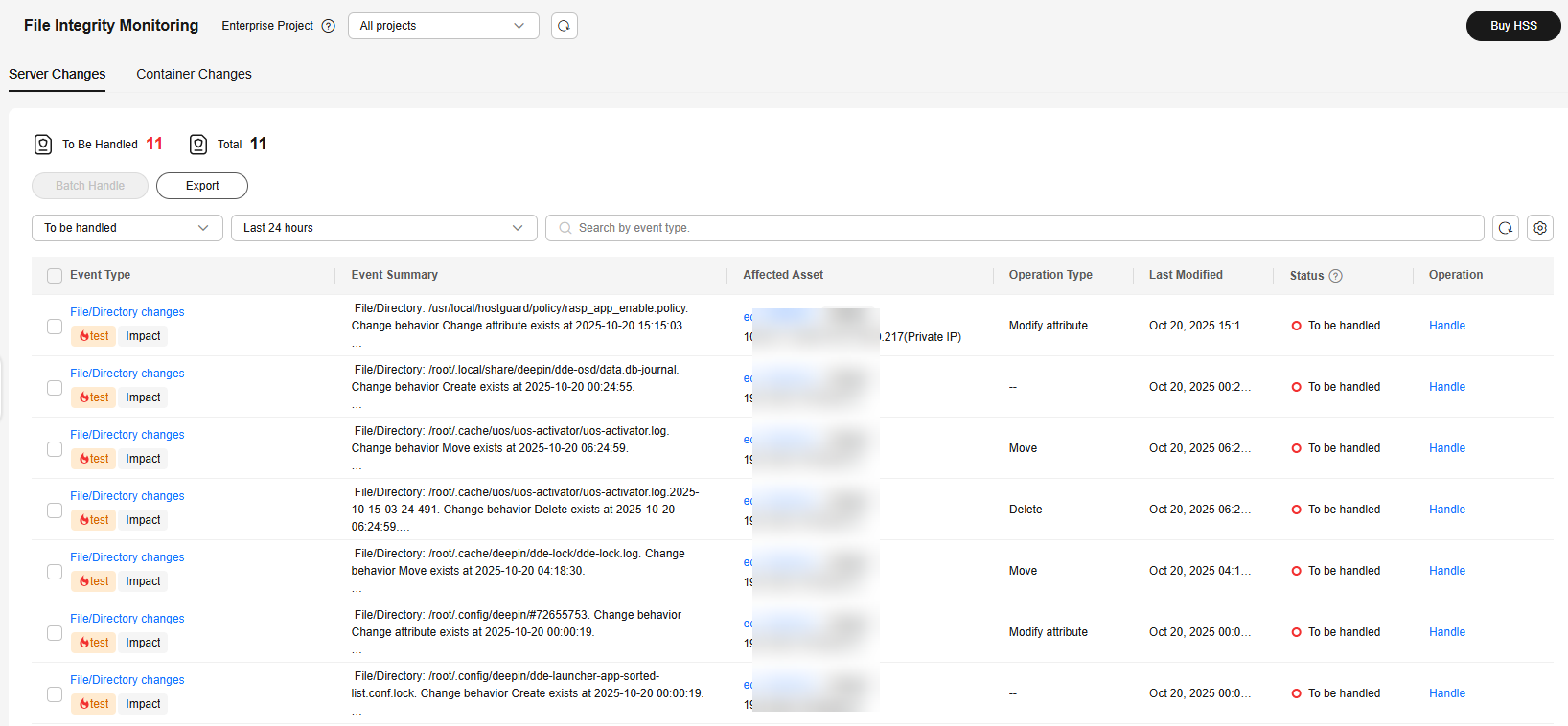
- Click the event type to view its details.
Event types include Important File Is Modified and File/Directory changes. The detection scopes of these event types are specified by File Integrity and Important File Directory Change parameters in the File Protection policy, respectively. For details about how to check or configure the File Protection policy, see Configuring Policies.
Figure 2 Event details
- Handle the event based on the Forensics information in the event details.
- Normal file or directory changes
You can ignore false events or add them to the whitelist.
- In the lower right corner of the event details page, click Ignore or Add to Alarm Whitelist.
- On the Handle Alarms page, set the batch handling, whitelist rule, and remarks.
- Whitelist rule: If Action is set to Add to alarm whitelist, you can click Add Rule to add a custom alarm whitelist rule. By default, HSS automatically provides a rule based on the event summary. You can modify it as needed. If the information of the alarm event detected by HSS is the same as or contains the rule information you entered, HSS will not report an alarm.
- Batch Handle: If you need to handle duplicate alarms at a time, select this option.
- Remarks: Enter the alarm handler or other remarks as needed.
- Click OK to handle the event.
- File or directory changes made by malicious programs
- Check whether high-risk alarms, such as reverse shell, abnormal login, and malware, are generated on the server or container. If yes, the server or container may be attacked. Perform a security check on it immediately.
- In the lower right corner of the event details page, click Mark as handled.
- On the Handle Alarms page, set the batch handling and remarks.
- Batch Handle: If you need to handle duplicate alarms at a time, select this option.
- Remarks: Record the alarm handler or other remarks.
- Click OK to close the event.
- Normal file or directory changes
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot





