Granting Permissions by Cloud Service
If your account has multiple cloud service resources that report monitoring data to Cloud Eye, you can assign different management permissions to various service operators at different levels to ease management.
In the current service scenarios, different cloud services might have different owners. So, you should grant permissions to each owner based on their specific cloud service to manage access.
This section describes how to grant permissions by cloud service.
Constraints
This feature is available only in the new IAM version.
Prerequisites
You have created a user group and an IAM user
Creating Custom Identity Policies
- Use the Huawei Cloud account to log in to the IAM console as an administrator.
- On the IAM console, click Go to New Console in the upper right corner.
- In the navigation pane on the left, choose Identity Policies.
- On the Identity Policies page, click Create Identity Policy in the upper right corner.
- On the Create Identity Policy page, enter a policy name, set Policy View to Visual editor, and configure the policy content.
- To configure permissions except ces:widgets:put, perform the following steps:
- Select Allow for Policy Content.
- Select the operations that support cloud service–based authorization. For details, see Actions That Support Authorization by Cloud Service. You can select all operations except ces:widgets:put.
- Click All resources. All resources is selected by default.
- Click (Optional) Add request condition.
- Click Add Request Condition. In the displayed dialog box, set parameters and click OK. Table 1 uses OBS, ECS, and EVS as an example to describe how to configure parameters. To authorize other cloud services, change the parameter value.
Table 1 Configuring a request condition Parameter
Description
Example Value
Condition Key
A key in the Condition element of a statement.
ces:namespace
Qualifier
The value can be Default, For any value in the request, or For all values in the request.
For any value in the request
Operator
Used together with a condition key and condition value to form a complete condition statement.
StringEquals
Value
Used together with a condition key and an operator that requires a keyword, to form a complete condition statement.
The condition value is the namespace of the cloud service to be authorized. To configure multiple cloud services, click Add and enter the namespace of each cloud service.
CAUTION:Some monitoring data of ECS and BMS depends on the Agent. To authorize ECS, you need to configure SYS.ECS and AGT.ECS. For BMS, configure SYS.ECS and SERVICE.BMS.
SYS.OBS
SYS.ECS
AGT.ECS
SYS.EVS
Figure 1 Configuring the policy content for permission 1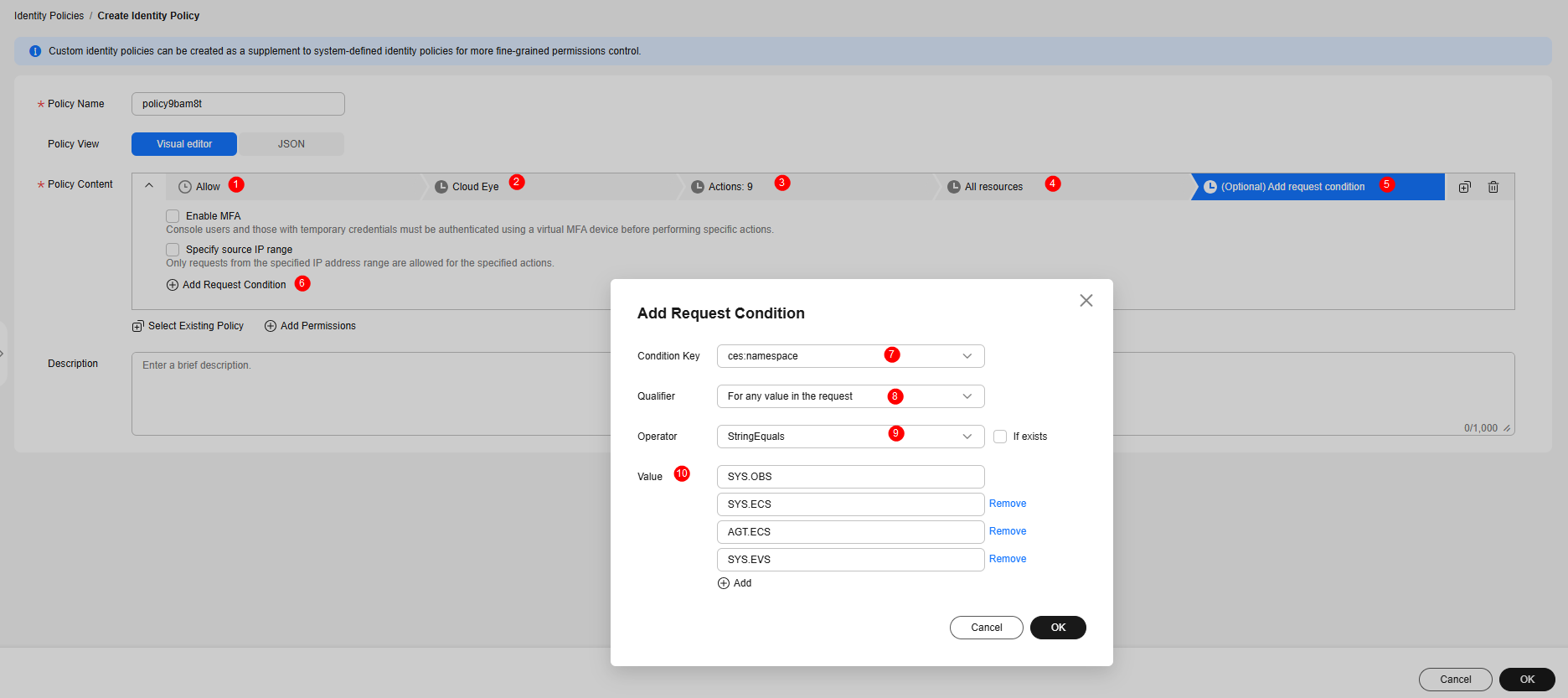
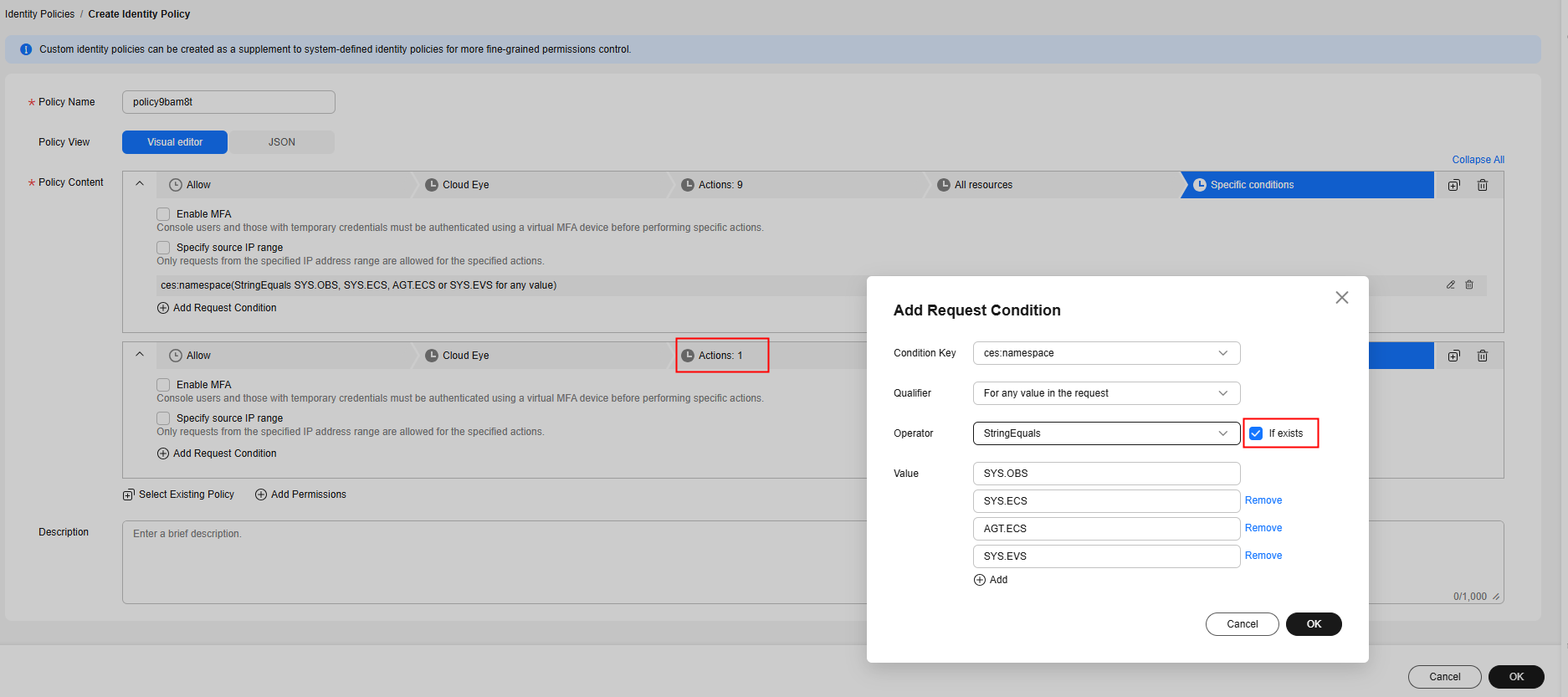
- If you also need to configure the ces:widgets:put operation permission, click Add Permissions under Policy Content and perform the following steps:
- Select Allow for Policy Content.
- Search for ces:widgets:put and select it.
- Click All resources. All resources is selected by default.
- Click (Optional) Add request condition.
- Click Add Request Condition. In the displayed dialog box, set parameters as described in Table 1 and select If exists next to Operator.
- Click OK.
Figure 2 Configuring the policy content for permission 2
- To configure permissions except ces:widgets:put, perform the following steps:
- On the Create Identity Policy page, click OK in the lower right corner.
Authorizing a User Group or User
After creating an identity policy, you can authorize a user or user group. To authorize all users in a user group, you need to authorize the user group. To authorize a single user in a user group, you need to authorize the IAM user. Once authorized, you can log in to the Cloud Eye console and check that only authorized cloud services can be operated. For more on authorizing operations by cloud service, see Actions That Support Authorization by Cloud Service.
After creating an identity policy, you can authorize a user or user group. To authorize all users in a user group, you need to authorize the user group.
- In the navigation pane of the new IAM console, choose User Groups.
- Locate the user group to be authorized and click Authorize in the Operation column.
- On the Select Identity Policies page, search for and select the system identity policy CESServiceFullAccessWithoutNamespacePolicy and the new identity policy.
- Click OK. In the displayed Information dialog box, click OK.
- On the Finish page, you can view the authorization results. Then, click Finish.
Once authorized, all users in the group have the corresponding permissions. If you need to change the permissions of a user, you can add the user to or remove the user from the authorized user group. For details, see Adding Users to or Removing Users from a Group.
In addition to granting permissions to user groups, IAM also allows you to grant permissions to individual users in a user group.
- In the navigation pane of the new IAM console, choose Users.
- Locate the user to be authorized and click Authorize in the Operation column.
- On the Assign Permissions page, set Assign By to Identity policy. Search for and select system identity policy CESServiceFullAccessWithoutNamespacePolicy and the created identity policy.
- Click OK. In the displayed Information dialog box, click OK.
- On the Finish page, you can view the authorization results. Then, click Finish.
Actions That Support Authorization by Cloud Service
Table 2 lists the actions that support authorization by cloud service and their application scenarios. You can select an action as needed.
|
Action |
Scenario |
Description |
|---|---|---|
|
ces:alarms:create |
Grants permission to create an alarm rule. |
|
|
ces:widgets:create |
Grants permission to add a graph. |
Authorization by cloud service is supported when you select Specified resources for Monitoring Scope. |
|
ces:dashboard:listCloudServiceResources |
Grants permission to view cloud service monitoring details. |
-- |
|
ces:dashboard:listServiceResourcesStatistics |
Grants permission to view cloud service monitoring details. |
-- |
|
ces:metaData:get |
Grants permission to view cloud service monitoring details (old edition). |
-- |
|
ces:metrics:listKeyMetrics |
Overview |
-- |
|
ces:namespacesDimensions:get |
Grants permission to create a custom graph. |
Authorization by cloud service is supported when you select Specified resources for Monitoring Scope. |
|
Grants permission to create a resource group. |
Authorization by cloud service is supported when you select Manually for Add Resources. |
|
|
Grants permission to create an alarm rule. |
|
|
|
Grants permission to export cloud service monitoring data. |
-- |
|
|
ces:namespacesDimensions:list |
Overview |
-- |
|
Grants permission to add a custom graph. |
Authorization by cloud service is supported when you select Specified resources for Monitoring Scope. |
|
|
Grants permission to view custom monitoring dashboards. |
Authorization by cloud service is supported when you select Specified resources for Monitoring Scope. |
|
|
Grants permission to create a resource group. |
Authorization by cloud service is supported when you select Manually for Add Resources. |
|
|
Grants permission to create or modify alarm rules. |
|
|
|
Grants permission to monitor servers. |
-- |
|
|
Grants permission to view cloud service monitoring details. |
-- |
|
|
Grants permission to export cloud service monitoring data. |
-- |
|
|
ces:namespacesDimensions:listInstances |
Grants permission to add or configure a custom graph. |
Authorization by cloud service is supported when you select Specified resources for Monitoring Scope. |
|
Grants permission to create or modify resource groups. |
Authorization by cloud service is supported when you select Manually for Add Resources. |
|
|
Grants permission to export cloud service monitoring data. |
-- |
|
|
Grants permission to create or modify alarm rules. |
|
|
|
ces:resourcesMetadata:list |
Grants permission to view custom monitoring dashboard details. |
Authorization by cloud service is supported when you select Specified resources for Monitoring Scope. |
|
Grants permission to add or configure a custom graph. |
Authorization by cloud service is supported when you select Specified resources for Monitoring Scope. |
|
|
Grants permission to view cloud service monitoring details. |
-- |
|
|
Grants permission to view the cloud service monitoring list. |
-- |
|
|
Grants permission to create or modify resource groups. |
Authorization by cloud service is supported when you select Manually for Add Resources. |
|
|
ces:resourcesConsole:list |
Grants permission to view the server monitoring list. |
-- |
|
ces:monitorOverview:listServiceResources |
Grants permission to view resources in a resource group. |
Authorization by cloud service is supported when you select Manually for Add Resources. |
|
ces:widgets:put |
Grants permission to configure a custom graph. |
Authorization by cloud service is supported when you select Specified resources for Monitoring Scope. |
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot





