Configuring Alarm Rules on the LTS Console
After event reporting is enabled, resource events will be reported to the log stream created by CCI 2.0. You can configure alarm rules on the LTS console. After events are generated and reported, the contacts configured on the SMN console will receive notifications.
Configuring Structured Parsing
- Log in to the LTS console. In the log group list on the Log Management page, click the log group name to go to the log group details page.
- Click
 in the upper right corner.
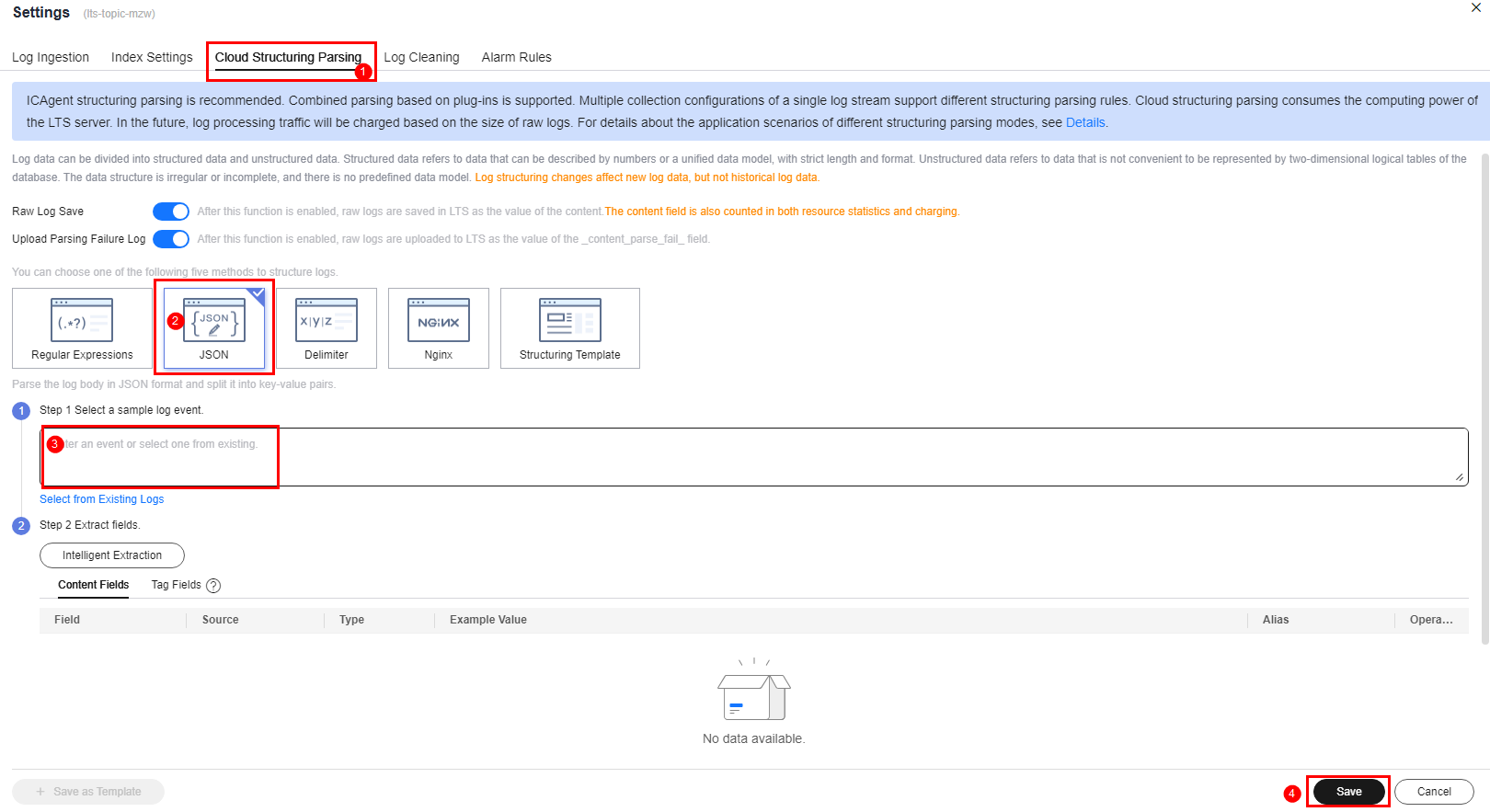
in the upper right corner. - On the Cloud Structuring Parsing tab, select JSON, and enter the event content in the Select a sample log event step.
- Click Intelligent Extraction and then Save. After the configuration is successful, the reported events will be parsed based on the structured analysis rule.
Figure 1 Configuring structured parsing
Creating an Alarm Rule
- Log in to the LTS console. In the log group list on the Log Management page, click the log group name to go to the log group details page.
- Configure filtering criteria for searing for the target events. You can also refer to Configuring Log Alarm Rules.
Figure 2 Configuring filtering criteria
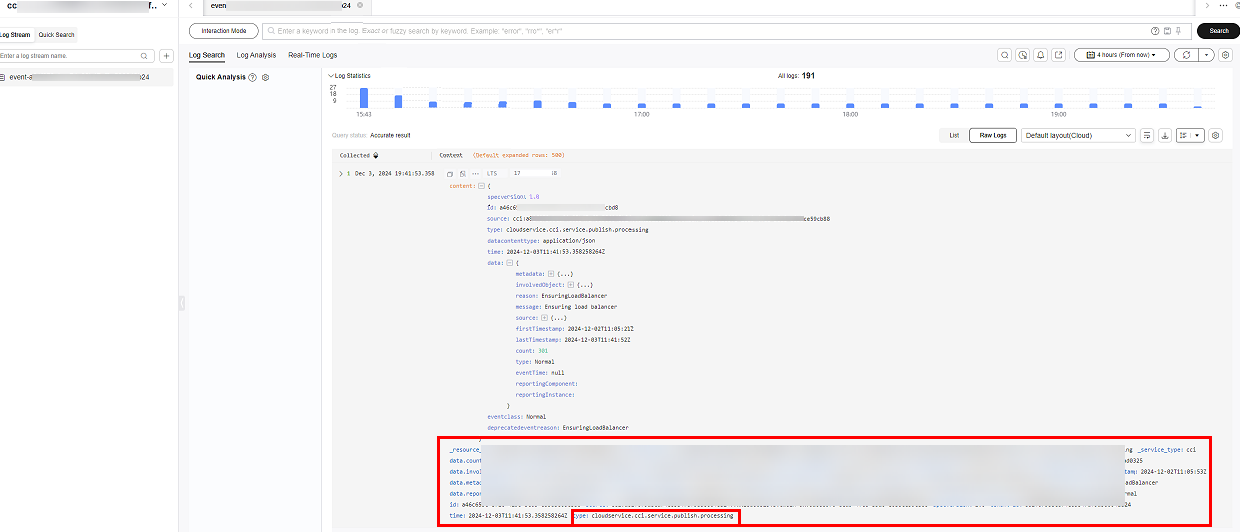
When searching for events based on the type field, you should use fuzzy matching so that you will not miss the events that need special attention.
- Log in to the LTS console. On the Log Alarms page, click Alarm Rules.
- Click Create.
- Enter basic information, select the log group and log stream, and enter keywords.
- Enable Alarm Action Rules and select an alarm action rule. If there are no alarm action rules, click Create Alarm Action Rule first.
Figure 3 Configuring advanced settings
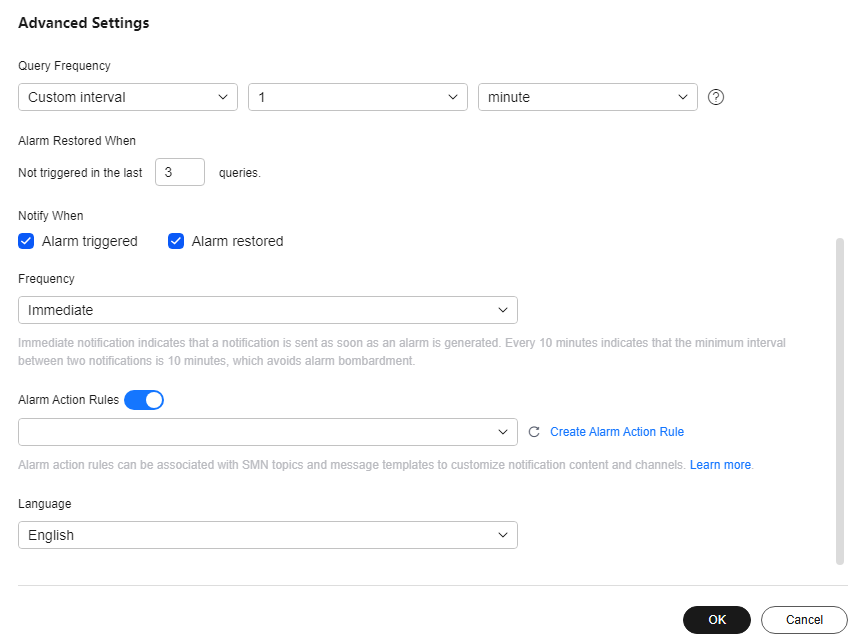
- Click OK.
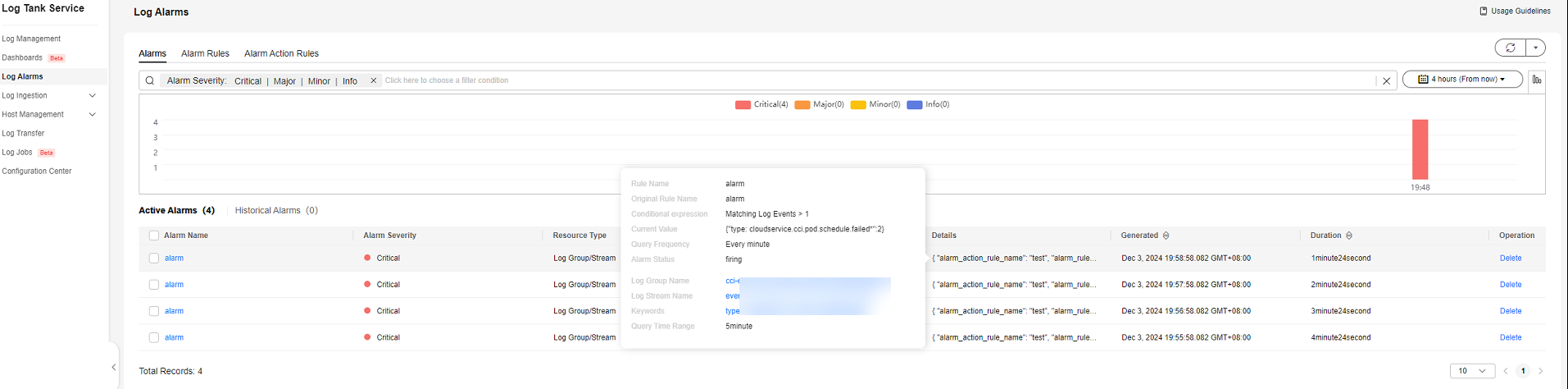
- An alarm is triggered after a specific event is reported. You can view the alarm on the LTS console (Log Alarms > Alarms).
Figure 4 Alarm triggered after a specific event is reported
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot





