All-Round Data Boundary
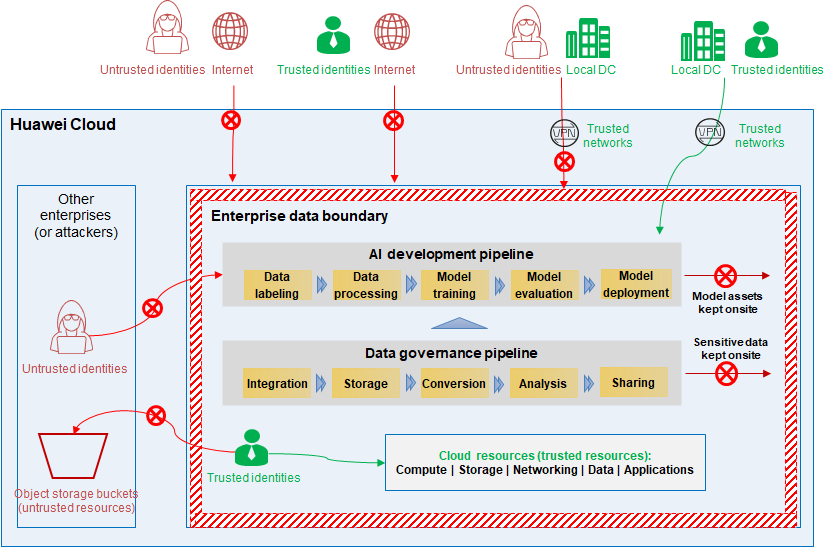
The all-around data boundary uses identity, network, and resource control policies to create a strong security shield. It ensures that only trusted, verified identities can access specific resources in a trusted, secure network environment, thereby maintaining data security. See the following figure. Requests from trusted identities to access cloud resources via the internet (untrusted network) are denied. Requests from untrusted identities to access cloud resources via the local data center network (trusted network) are also denied. Requests from trusted identities to access object storage buckets of other enterprises (untrusted resources) are still denied. Only requests from trusted identities to access cloud resources of their own enterprises via the local data center network (trusted network) are allowed.
Identity Control Policies
Identity control policies are the first line of defense for data boundaries. They ensure that only trusted, verified identities can access enterprise cloud resources. Identity control policies are implemented using service control policies (SCPs) and IAM policies.
SCPs control access based on organizational structure. The organization management account can use SCPs to limit permissions for member accounts to ensure that they stay within your organization's access control guidelines. SCPs can be attached to an organization, organizational units (OUs), and member accounts. Any SCP attached to an organization or OU applies to all the accounts within the organization or under the OU.
For details about SCPs, see SCP Introduction.
SCPs can affect many areas. Test them thoroughly before applying them in your production environment to prevent issues with your cloud resources.
IAM policies control access to Huawei Cloud resources for users, user groups, and agencies. Enterprises can use IAM policies to give users only the permissions they need for operations on specific resources, following the principle of least privilege. This improves security and reduces permission abuse risks.
For details about IAM policies, see Basic Concepts.
On Huawei Cloud, identity control policies are implemented using SCPs and IAM policies. When both SCPs and IAM policies are set, user permissions are the overlap between the two.
Network Control Policies
Network control policies are the second line of defense for data boundaries. They are implemented using Virtual Private Cloud Endpoint (VPCEP) policies.
VPCEP is a network service that sets up private connections in a VPC. It lets you securely connect your VPC to Huawei Cloud services and resources without using public IP addresses. Data is not transmitted over the internet, reducing the risk of interception and attacks. VPCEP policies control which principals (or identities) can use VPC endpoints to access cloud resources. By setting these policies, enterprises can create a closed, secure network. This keeps data safe inside the network and allows only trusted identities to access cloud resources and sensitive data. For example, enterprises can deploy key service systems in VPCs and connect them to RDS DB instances on Huawei Cloud using VPCEP, keeping them off the public network. Only database administrator Shane can access these RDS DB instances via VPCEP, adding another layer of security for sensitive data.
For details about how to manage VPCEP policies, see Managing the Policy of a VPC Endpoint.
Resource Control Policies
Resource control policies are the third line of defense for data boundaries. They are implemented using cloud services' access control policies, such as OBS's bucket policies.
Bucket policies let owners set permissions for their buckets and objects. Enterprises can use bucket policies to specify which users can or cannot perform operations on buckets. For example, you can allow a user to read a specific bucket but not write to or delete it. Bucket policies allow flexible access control based on conditions like requester IP address and request time. For example, an enterprise can set a bucket policy to allow only internal network requests or limit access to a specified period.
For details about how to create a bucket policy, see Creating a Bucket Policy with a Template.
Together, bucket policies and VPCEP policies enhance security. You can set VPCEP policies to let servers (ECS, CCE, and BMS) in a VPC access only certain OBS resources. You can also set bucket policies to allow only servers in a specific VPC to access OBS buckets. This maintains security by controlling both request sources and accessed resources.
Building an all-round data boundary is a systematic and comprehensive project. Enterprises must apply strict control policies for identities, networks, and resources. Coordinating all these three aspects creates a strong data security shield.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot





