Creating a Key for Cloud Service Encryption
A key can be symmetric or asymmetric.
- For symmetric keys, the same key is used to encrypt and decrypt data, which is fast and efficient, suitable for encrypting a large amount of data.
- For asymmetric keys, a key pair, that is, a public key and a private key, are used for encryption and decryption. Public keys can be distributed to anyone, while private keys must be kept secure and provided for only trusted users. These keys are used for digital signature verification and encrypted transmission of sensitive information.
Procedure
This section uses the AES-256 symmetric key and RSA-2048 asymmetric key as examples to describe how to create a key and bind it to a cloud service. The following figure shows the process.

|
Procedure |
Description |
|---|---|
|
Register a Huawei ID, enable Huawei Cloud services, top up the account, and grant KMS permissions to the account. |
|
|
Create a key and select the key algorithm type. |
|
|
After the key is created, bind the key to the instance when you create or use a cloud service instance for encryption. |
Preparations
- Before creating key, register a Huawei Cloud account and enable Huawei Cloud services. For details, see Signing Up for a HUAWEI ID and Enabling Huawei Cloud Services.
If you have enabled Huawei Cloud, skip this step.
- You have obtained KMS CMKFullAccess or higher permissions. For details, see Creating a User and Authorizing the User the Permission to Access DEW.
Table 1 KMS system-defined roles Role
Description
Type
Dependencies
KMS administrator
All permissions of KMS
System-defined role
None
KMS CMKFullAccess
All permissions for KMS keys. Users with these permissions can perform all the operations allowed by policies.
System-defined policy
None
KMS CMKReadOnlyAccess
Read-only permissions for KMS keys. Users with these permissions can perform all the operations allowed by policies.
System-defined policy
None
Step 1: Creating a Key
This section describes how to create an AES-256 symmetric key and an RSA-2048 asymmetric key.
The created key can be used only in the current region. To use it in other regions, switch to the target region and create a key or use a regional key.
- Log in to the DEW console.
- On the Key Management Service page, click Create Key in the upper right corner.
- On the displayed page, configure the parameter as shown in the following and retain default settings for other parameters. For details about the parameters, see Table 2.
Figure 2 Creating a key
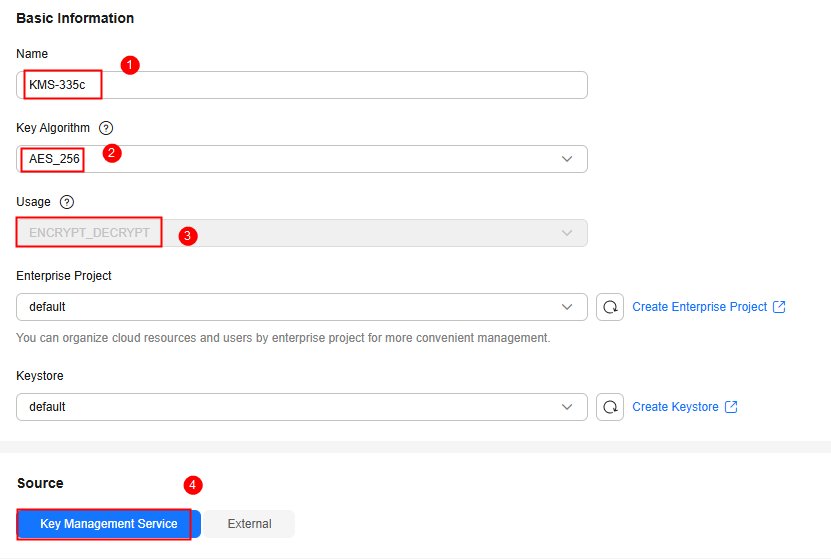
Table 2 Mandatory parameters Parameter
Example Value
Description
Name
KMS-335c
Custom key name, which cannot be empty.
Key Algorithm
AES-256
Supported key algorithm types and description. For details, see Key algorithms supported by KMS.
Usage
ENCRYPT_DECRYPT
The value cannot be changed after the key is created.
For AES_256 symmetric keys, the default value is ENCRYPT_DECRYPT.
Source
Key Management Service
The following key material sources are supported:
- Key Management Service: KMS generates key materials.
- External: Import local key materials to KMS.
- Click OK. A message is displayed in the upper right corner of the page, indicating that the key is created. In the key list, you can view the created keys, which are in the Enabled state by default.
The created key can be used only in the current region. To use it in other regions, switch to the target region and create a key or use a regional key.
- Log in to the DEW console.
- On the displayed Key Management Service page, click Create Key in the upper right corner.
- On the displayed page, configure the parameter as shown in the following and retain default settings for other parameters. For details about the parameters, see Table 2.
Figure 3 Creating a key
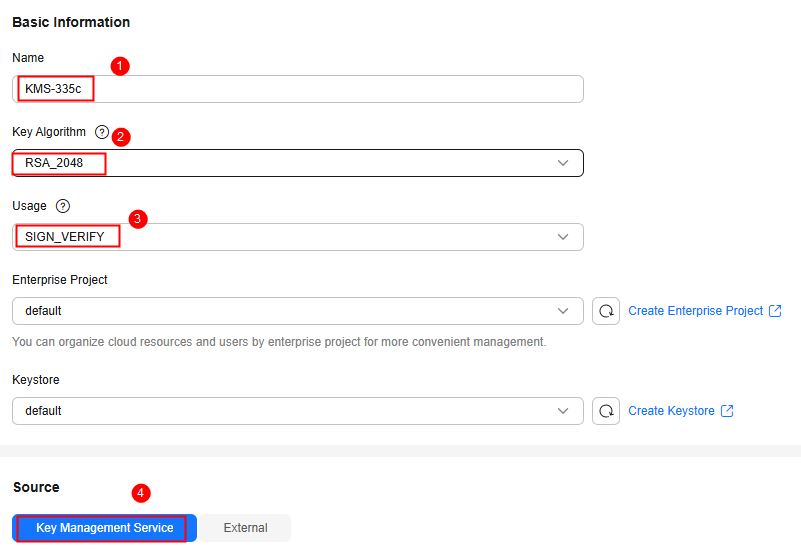
Table 3 Mandatory parameters Parameter
Example Value
Description
Name
KMS-335c
Custom key name, which cannot be empty.
Key Algorithm
RSA-2048
Supported key algorithm types and description. For details, see Key algorithms supported by KMS.
Usage
SIGN_VERIFY
The value cannot be changed after the key is created.
For RSA asymmetric keys, the value can be ENCRYPT_DECRYPT or SIGN_VERIFY.
Source
Key Management Service
The following key material sources are supported:
- Key Management Service: KMS generates key materials.
- External: Import local key materials to KMS.
- Click OK. A message is displayed in the upper right corner of the page, indicating that the key is created. In the key list, you can view the created keys, which are in the Enabled state by default.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot





