Device Integration
How Do I Obtain the Device Access Address?
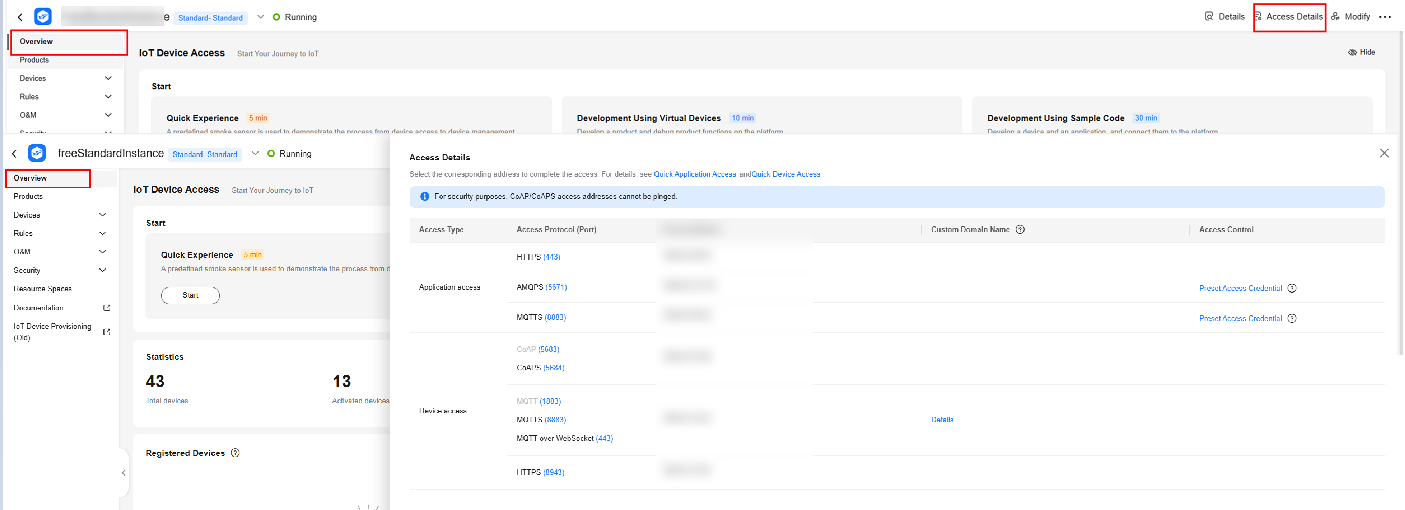
- Log in to the IoTDA console. In the navigation pane, choose IoTDA Instances. Click the target instance card.
Figure 1 Instance management - Changing instance

- In the navigation pane, choose Overview. Click Access Details to check your platform access address.
Figure 2 Obtaining access information
Must the X.509 Certificate I Use for Device Connection Be Issued by an Authoritative Organization?
Not necessary. A custom certificate is also supported, but you are advised to use a certificate issued by an authoritative organization. For details, see Uploading a Device CA Certificate.
How Do I Locate the Cause of the Certificate-based Device Connection Failure?
- Check whether the platform CA entered on the device side is correct.
Platform certificate verification fails on the device side if the following stack information is displayed: Caused by: javax.net.ssl.SSLHandshakeException: sun.security.validator.ValidatorException: PKIX path building failed: sun.security.provider.certpath.SunCertPathBuilderException: unable to find valid certification path to requested target. In this case, check whether the platform CA entered on the device side is correct.
Use OpenSSL to run the following command to obtain server certificate information:
openssl s_client --connect <brokerAddress:brokerPort>
Figure 3 OpenSSL execution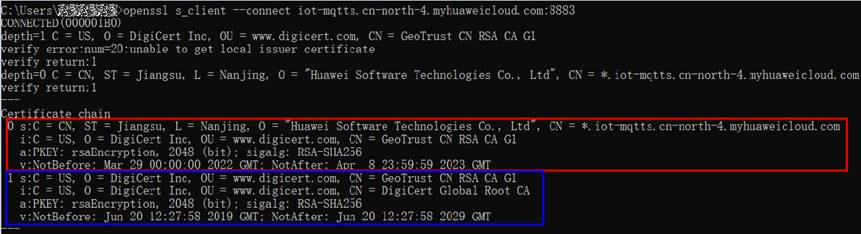
The obtained certificate chain contains the following certificates:
- Certificate 0 is the platform certificate that identifies the platform.
- Certificate 1 is the intermediate CA that issues the platform certificate.
When verifying the platform identity, a device needs to use the intermediate CA issuer to verify the certificate chain.
Check whether the user information of the platform root CA entered on the device side is consistent the issuer information of the intermediate CA. If consistent, save the intermediate CA displayed in the CLI as a file and run the following command to verify the issuing relationship between the root CA and the intermediate CA:
openssl verify -verbose -CAfile <CAFile> <middleCAFile>
Figure 4 OpenSSL certificate verification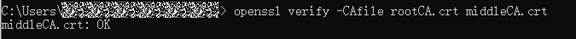
- Check whether the device certificate entered on the device side matches the private key of the device certificate.
Run the following commands to extract the MD5 hash values of the certificate and private key file:
openssl x509 -noout -modulus -in <certificate file> | openssl md5
openssl rsa -noout -modulus -in <private key file> | openssl md5
If the two MD5 hash values are different, the certificate and private key do not match. You are advised to enter the correct device certificate and private key.
Figure 5 Comparing MD5 values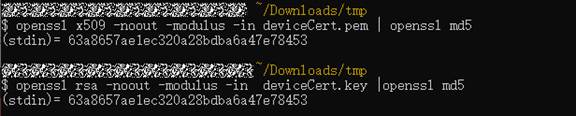
- Check the binding relationship between the device and the certificate fingerprint.
Enable message tracing for the device and locate the fault based on the traced messages.
How Do I Set the Device Name?
- Set the name of a device when you add the device to the IoTDA console.
- Set the device name when you use the API for registering or creating a device.
How Do I Activate IoT Devices?
When a device is registered on the IoT platform, and gets connected to the platform or starts to report data to the platform, the device is considered to be activated. For details, see Device Connection Authentication.
How Is the Status of a Device Changed?
An NB-IoT device is considered online when it reports data to the IoT platform. If no data is reported within 25 hours since the last data reporting, the device status changes to abnormal. If no data is reported within 49 hours, the device status changes to offline.
An MQTT device is considered online when it is connected to the platform. If the device is disconnected from the platform, it is considered to be offline and its status will be updated on the platform within a minute. You can click the status refresh button to update the status immediately.
For details, see Device Management.
How Can I Check the Details of Gateways and Child Devices?
Log in to the IoTDA console, choose Devices > All Devices in the navigation pane, and click View in the row where a gateway is located. Check the gateway details on the Device Info tab page, and check its child devices on the Child Devices tab page. For details, see Gateways and Child Devices.

Why Is the Status of Child Devices Displayed as Online When the Gateway Is Offline?
The status of child devices is managed by the gateway. When the gateway is offline, it can call the API for Gateway Updating Child Device Status to send the latest status of child devices to the IoT platform.
What Are the Differences Between Device ID, Node ID, and IMEI and What Are They Used For?
On the IoT platform, you need to enter a node ID (nodeId) when registering a device. A node ID is a physical identifier of a device. Generally, an IMEI or MAC address is used. A device ID (deviceId) is a logical identifier of a device on the IoT platform.
- NB-IoT devices: The node ID is carried for access authentication when a device connects to the platform.
- MQTT devices: A device uses the secret and device ID to connect to the platform. The access authentication is the one-device-one-secret mode.
For details, see Device Authentication.
Can a Device Send Files to the IoT Platform?
Yes. For details about the sending process, see File Uploads.
What Do I Do If the IoT Link Plug-in Download Fails When Using the BearPi Development Board?
Download Visual Studio Code 1.49 that matches your computer configuration and install it. Other versions do not support IoT Link.
What Do I Do If Device Activation Fails When Using the BearPi Development Board?
Enter AT+CGATT? and click Send. If +CGATT:1 is returned, the network attach is successful, indicating that the NB-IoT network is normal. If +CGATT:0 is returned, the network attach fails. Check whether the SIM card is correctly inserted, contact the carrier to check the network status, or check whether the IMEI is the same as that entered during device registration on the platform. You can obtain the IMEI by setting the dialing test switch to the AT-PC mode, selecting the STM port, setting the baud rate to 9600, and then running the AT+CGSN=1 command.
What Do I Do If Data Reporting or Command Receiving Fails When Using the BearPi Development Board?
Obtain code from Developing a Smart Street Light Using NB-IoT BearPi or Developing a Smart Smoke Detector Using NB-IoT BearPi. If the code is obtained from other channels, contact technical support of the channel. You can also post your questions about BearPi on the forum.
What Do I Do If a Message is Displayed Indicating that the Device is Occupied During Device Registration?
For an MQTT device, check whether the device ID is unique under your account. For an LwM2M device, check whether the node ID is unique under your account. If the device/node ID is unique, submit a service ticket on the console.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot





