NGINX Ingress Controller
Check Items
- Check whether there is an Nginx Ingress route whose ingress type is not specified (kubernetes.io/ingress.class: nginx is not added to annotations) in the cluster.
- Check whether the default backend Service specified by the NGINX Ingress Controller backend is available.
- Check whether the key length of the default server certificate specified by the NGINX Ingress Controller meets the security requirements. (If the length fails to meet the security requirements, error message "xxx" is displayed.)
Fault Locating
For Check Item 1
For Nginx Ingress, check the YAML. If the ingress type is not specified in the YAML file and the ingress is managed by the NGINX Ingress Controller, the ingress is at risk. For details, see Possible Causes.
- Check the ingress type.
Run the following command:
kubectl get ingress <ingress-name> -oyaml | grep -E ' kubernetes.io/ingress.class: | ingressClassName:' -B 1
- Fault scenario: If the command output is empty, the ingress type is not specified.
- Normal scenario: The command output is not empty, indicating that the ingress type has been specified by annotations or ingressClassName.

- Ensure that the ingress is managed by the Nginx ingress Controller. The LoadBalancer Ingresses are not affected by this issue.
- For clusters of v1.19, confirm this issue using managedFields.
kubectl get ingress <ingress-name> -oyaml | grep 'manager: nginx-ingress-controller'

- For clusters of other versions, check the logs of the NGINX Ingress Controller pod.
kubectl logs -nkube-system cceaddon-nginx-ingress-controller-545db6b4f7-bv74t | grep 'updating Ingress status'

If the fault persists, contact technical support.
- For clusters of v1.19, confirm this issue using managedFields.
For Check Item 2
- View the DefaultBackend Service in the namespace where the NGINX Ingress Controller is deployed.
kubectl get pod cceaddon-nginx-ingress-<controller-name>-controller-*** -n <namespace> -oyaml | grep 'default-backend'
cceaddon-nginx-ingress-<controller-name>-controller-*** is the controller pod name, <controller-name> is the controller name specified during add-on installation, and <namespace> is the namespace where the controller is deployed.
Command output:
- '--default-backend-service=<namespace>/<backend-svc-name>'
<backend-svc-name> is the name of the DefaultBackend Service for the NGINX Ingress Controller.
- Check whether the default backend Service of the NGINX Ingress Controller is available.
kubectl get svc <backend-svc-name> -n <namespace>
If the Service is unavailable, this check item failed.
For Check Item 3
- Check whether there is a default server certificate in the namespace where the NGINX Ingress Controller is deployed.
kubectl get pod cceaddon-nginx-ingress-<controller-name>-controller-*** -n <namespace> -oyaml | grep 'default-ssl-certificate'
cceaddon-nginx-ingress-<controller-name>-controller-*** is the controller pod name, <controller-name> is the controller name specified during add-on installation, and <namespace> is the namespace where the controller is deployed.
Command output:
- '--default-ssl-certificate=<namespace>/<secret-name>'
<secret-name> indicates the secret name for the default server certificate specified by the NGINX Ingress Controller.
- Check whether the default certificate used by the NGINX Ingress Controller has a security risk due to insufficient encryption length.
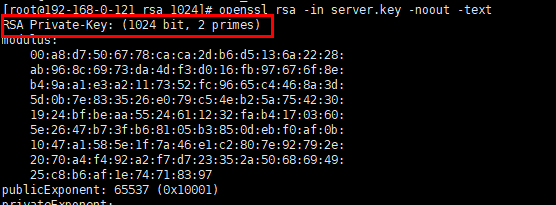
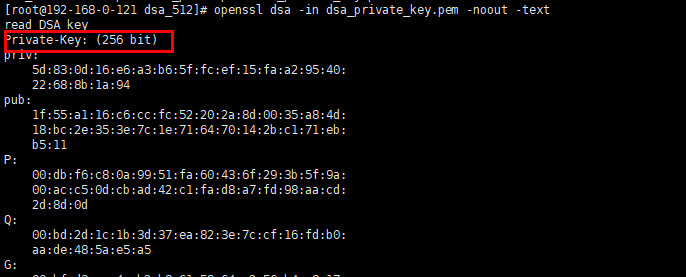
kubectl get secret <secret-name> -n <namespace> -o=custom-columns=:'data.tls\.key' | base64 -d | openssl <encryption-algorithm> -noout -text
<encryption-algorithm> is the encryption algorithm used by the certificate. Common encryption algorithms include RSA and DSA.
Method of obtaining an RSA key length
Method of obtaining a DSA key length
Solution
For Check Item 1
Add an annotation to the Nginx ingresses as follows:
kubectl annotate ingress <ingress-name> kubernetes.io/ingress.class=nginx

There is no need to add this annotation to LoadBalancer ingresses. Verify that these ingresses are managed by NGINX Ingress Controller.
For Check Item 2
- If a custom default backend Service has been specified in the default 404 service configuration during add-on installation, create the same Service.
- If the default backend Service is used during add-on installation, the following is an example YAML file for re-creating a Service:
apiVersion: v1 kind: Service metadata: name: cceaddon-nginx-ingress-<controller-name>-default-backend # <controller-name> is the controller name. namespace: kube-system labels: app: nginx-ingress-<controller-name> app.kubernetes.io/managed-by: Helm chart: nginx-ingress-<version> # <version> is the add-on version. component: default-backend heritage: Helm release: cceaddon-nginx-ingress-<controller-name> annotations: meta.helm.sh/release-name: cceaddon-nginx-ingress-<controller-name> meta.helm.sh/release-namespace: kube-system # Namespace where the add-on is installed spec: ports: - name: http protocol: TCP port: 80 targetPort: http selector: app: nginx-ingress-<controller-name> component: default-backend release: cceaddon-nginx-ingress-<controller-name> type: ClusterIP sessionAffinity: None ipFamilies: - IPv4 ipFamilyPolicy: SingleStack internalTrafficPolicy: Cluster
- Change the secret of the certificate described in 1 and configure a certificate that meets the key length specified by OpenSSL SECLEVEL. For details about the relationship between the security levels and key lengths, see official OpenSSL documents.
- Add the @SECLEVEL field to the ssl-ciphers parameter to support certificates with lower security levels. For details, see Why TLS v1.0 and v1.1 Cannot Be Used After the NGINX Ingress Controller Add-on Is Upgraded?
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot





