Obtaining a Long-Term Valid Login Command
Scenario
This section describes how to obtain a login command that is permanently valid.
- For security purposes, it is advised to obtain the login command in the development environment.
- Before logging in to the IAM console, ensure that you have the permission for accessing IAM service. For details about the authorization mode, see Creating a User Group and Assigning Permissions.
Process
You can obtain a long-term valid login command as the following process:

Procedure
- Obtain the programmatic access permission. (If the current user has the permission, skip this step.)
- Log in to the management console as an administrator.
- Click
 in the upper left corner and select a region and a project.
in the upper left corner and select a region and a project. - Click
 in the navigation pane on the left and choose Management & Governance > Identity and Access Management.
in the navigation pane on the left and choose Management & Governance > Identity and Access Management. - Enter the name of the user to whom you want to grant the programmatic access permission in the search box on the Users page.
- Click the user to go to its details page.
- Click
 next to Access Type.
next to Access Type. - Select Programmatic access. (You can select only programmatic access or both access types.)
- Obtain the regional project name and image repository address.
- Log in to the IAM console.
- Hover the cursor over the username in the upper right corner.
- Choose My Credentials from the drop-down list.
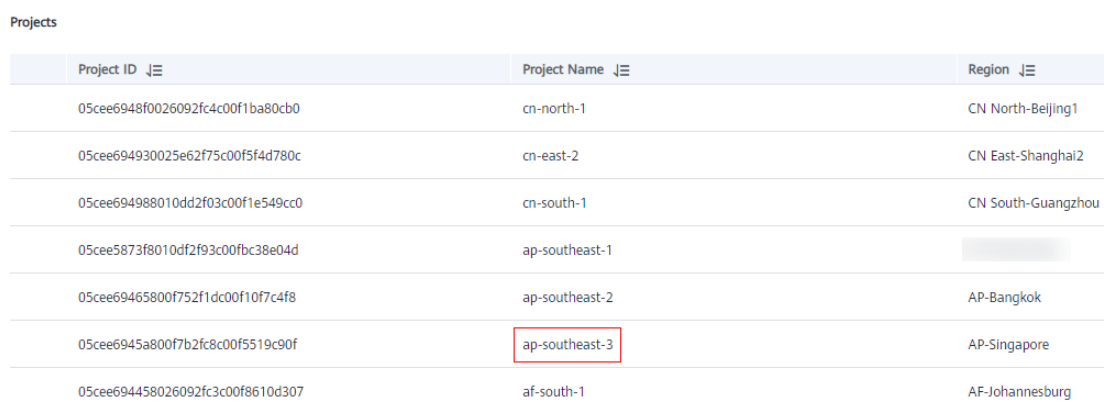
- In the project list, find the region and project to which your VM belongs.
Figure 2 Region and project
- Obtain an AK/SK.
The access key ID (AK) and secret access key (SK) are a pair of access keys used together to authenticate users who wish to make API requests. The AK/SK pair provides functions similar to a password. If you already have an AK/SK, skip this step.
- Log in to the IAM console, hover over your username, and click My Credentials.
- In the navigation pane on the left, choose Access Keys and click Create Access Key.
- Enter a description, and click OK.
- In the displayed dialog box, click Download.
After the certificate is downloaded, obtain the AK and SK information from the credentials file.
Table 1 credentials file User Name
Access Key Id
Secret Access Key
a*****
RVHVMX******
H3nPwzgZ******
Keep the AK/SK file confidential to prevent information leakage.
- Log in to a Linux PC and run the following command to obtain the login key:
printf "AK" | openssl dgst -binary -sha256 -hmac "SK" | od -An -vtx1 | sed 's/[ \n]//g' | sed 'N;s/\n//'
Replace AK with the Access Key Id and SK with Secret Access Key in the credentials file in Step 3.
Examples:
printf "RVHVMX******" | openssl dgst -binary -sha256 -hmac "H3nPwzgZ******" | od -An -vtx1 | sed 's/[ \n]//g' | sed 'N;s/\n//'
After the command is executed, the following login key is obtained:
cab4ceab4a1545***************
The preceding key is only an example.
- Put the information you obtained in the following format to generate a long-term valid login command:
docker login -u [Regional project name]@[AK] -p [Login key] [Image repository address]
In the command, the regional project name and image repository address are obtained in 2, the AK in 3, and the login key in 4.
Examples:
docker login -u ap-southeast-3@RVHVMX****** -p cab4ceab4a1545*************** swr.ap-southeast-3.myhuaweicloud.com
If the Login Succeeded message is displayed, it indicates that the login is successful.
- The login key is encrypted and cannot be decrypted. Therefore, other users cannot obtain the SK from -p.
- The login command can be used on other devices.
- (Optional) When you log out the repository, run the following command to delete your authentication information.
cd /root/.docker/ rm -f config.json
- Run the history -c command to clear the operation records.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot








