Getting Started with Tag Policies
Background
This section describes how to quickly standardize tags across resources with tag policies.
When using a tag policy for the first time, you are advised to attach a simple tag policy to a test account with fewer resources. If the test is successful and you are confident you fully understand the impacts of tag policies, you can attach more advanced tag policies to the root OU, other OUs, or more accounts of the organization.
Procedure
- Log in to Huawei Cloud as the organization administrator or using the management account, navigate to the Organizations console, and access the Organization page.
- Enable the tag policy type for your organization.
- Create a tag policy.
When you are creating a tag policy for the first time, keep it simple, for example:
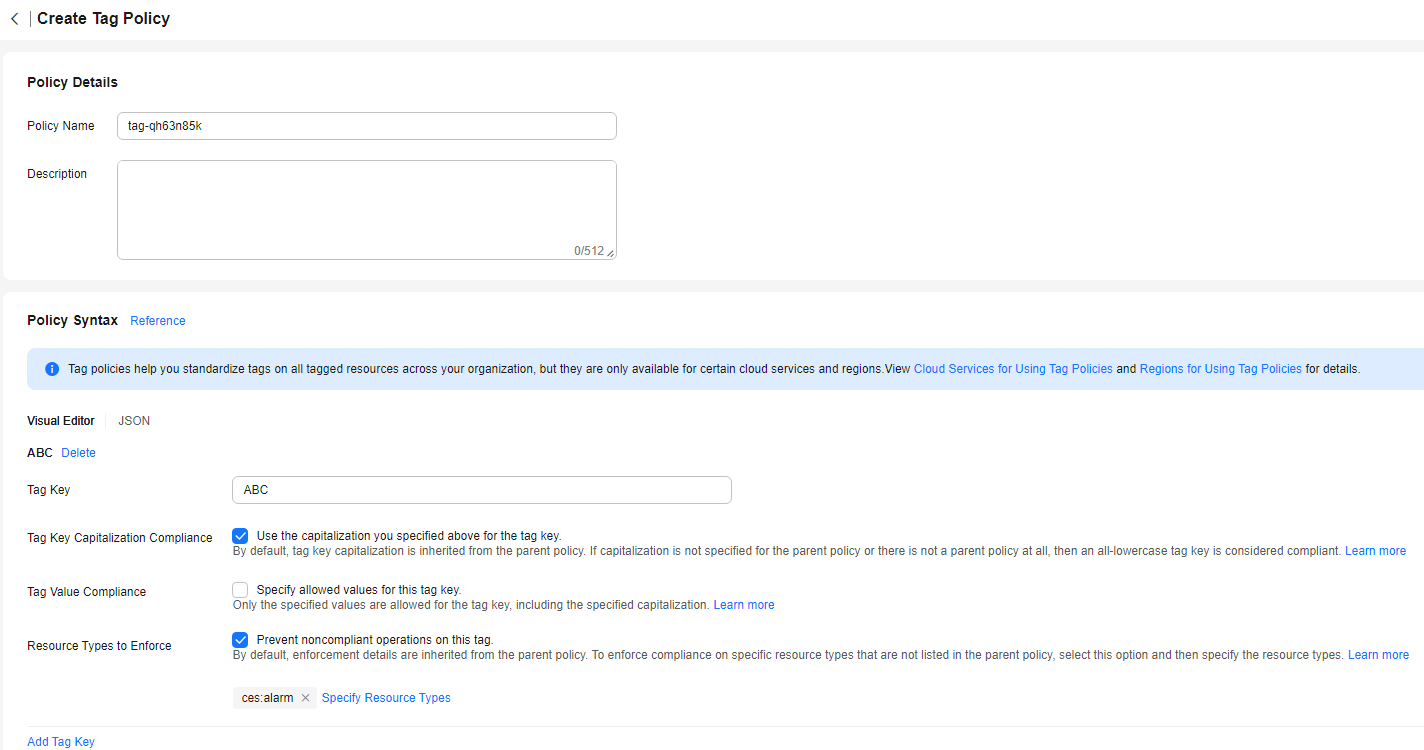
- Set the tag key to ABC.
- Use the capitalization you specified for the tag key for compliance check. Tag keys in all uppercase characters are considered compliant. Those in all lowercase characters or both uppercase and lowercase characters are considered non-compliant. The tag policy will prevent you from adding any non-compliant tags to your resources.
- Specify resource types (such as ces:alarm, the alarm rules of Cloud Eye) to enforce the tag policy. The tag policy will only be applied to resources of the specified type. For details about the cloud services and resource types that support tag policies, see Cloud Services for Using Tag Policies.
If a tag is non-compliant, the tag policy will prevent you from adding the tag. You will have to modify the tag to comply with the tag policy.Figure 1 Creating a tag policy
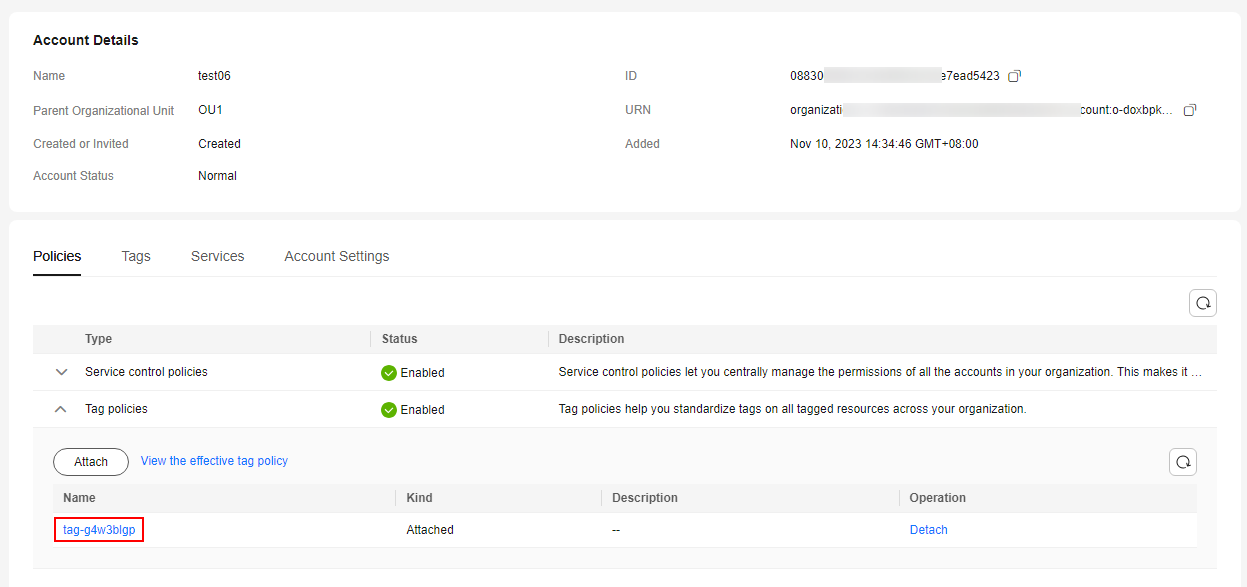
- Attach the tag policy to a test account, one without too many resources. For details, see Attaching a Tag Policy.
Figure 2 Attaching a tag policy
- Log in to Huawei Cloud using the test account. Access the Cloud Eye console, create an alarm rule, and add a tag to the alarm rule to check whether the tag policy is in effect.
- If you add tag ABC to the alarm rule, the operation will be successful.
- If you add tag abc to the alarm rule, a message will be displayed, indicating that the tag is non-compliant. In this case, you need to modify the tag and try again until it becomes compliant.
When you are creating resources with non-compliant tags, the tag policy will prevent this operation, and the resource cannot be created.
When you are adding non-compliant tags to existing resources, the tag policy will prevent this operation, but the resources will not be affected.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot





