Step 2: Create a Tracker
After you create the detector, CTS threat detection is enabled by default. However, MTD cannot obtain log data from the CTS service without a tracker.
This section describes how to configure the tracker.
Limitations and Constraints
CTS threat detection is not supported for the CN-Hong Kong region.
Procedure
- Log in to the management console.
- Click
 in the upper left corner of the management console and select a region or project.
in the upper left corner of the management console and select a region or project. - Click
 in the left navigation pane and choose Security & Compliance > Managed Threat Detection.
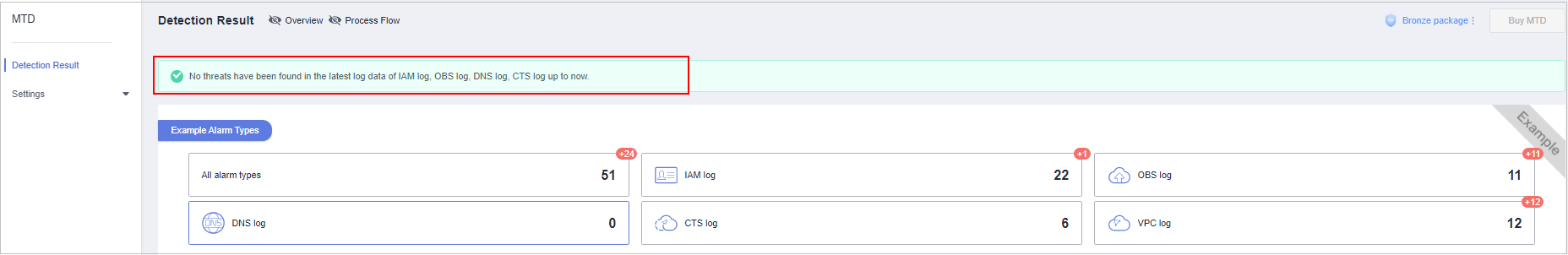
View the notice on the Detection Result page.Figure 1 Notice on the detection result page
in the left navigation pane and choose Security & Compliance > Managed Threat Detection.
View the notice on the Detection Result page.Figure 1 Notice on the detection result page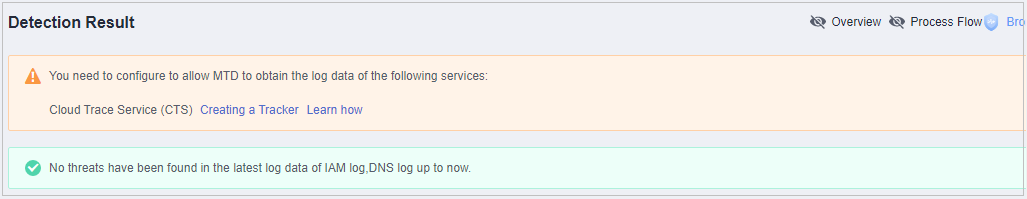
- Click Creating a Tracker to switch to the CTS Tracker List page. In the tracker list, locate the only default tracker which is of the Management type.
Figure 2 Management tracker

- In the row that contains the target tracker, click Configure in the Operation column.
- On the Basic Information page, the tracker name is generated by default.
- Click Next to go to the Configure Transfer page.
- On the Configure Transfer page, toggle on Transfer to LTS.
Figure 3 Configure Transfer
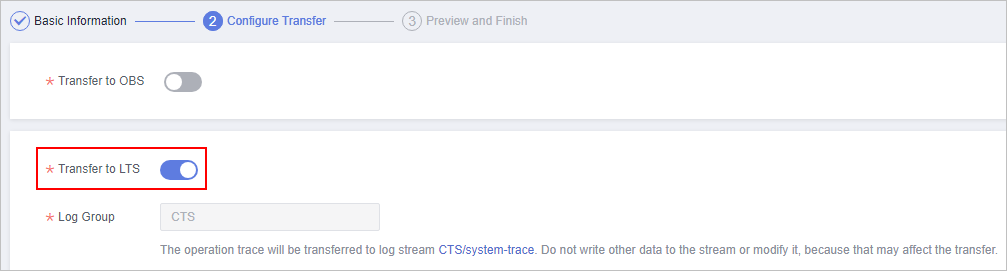
- Click Next to go to the Preview and Finish page
- Confirm settings and click Configure.
- Go back to the MTD console.
- In the left navigation pane, choose . On the Detection Settings page, click
 next to Cloud Trace Service (CTS) to turn the toggle off. In the displayed dialog box, click OK to temporarily disable CTS threat detection. Operation successfully! is displayed in the upper right corner.
Figure 4 Disabling CTS
next to Cloud Trace Service (CTS) to turn the toggle off. In the displayed dialog box, click OK to temporarily disable CTS threat detection. Operation successfully! is displayed in the upper right corner.
Figure 4 Disabling CTS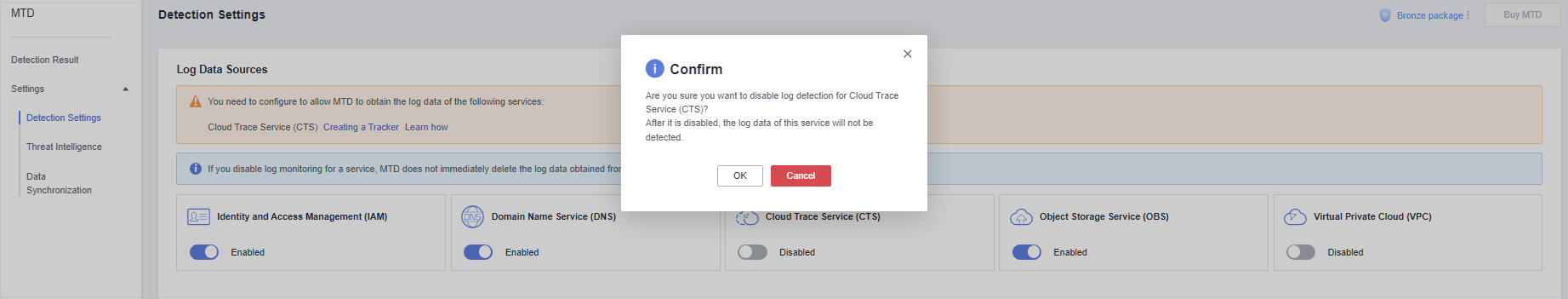
- Click
 next to Cloud Trace Service Log (CTS) to enable CTS threat detection. Operation successfully! is displayed in the upper right corner.
Figure 5 Enabling CTS
next to Cloud Trace Service Log (CTS) to enable CTS threat detection. Operation successfully! is displayed in the upper right corner.
Figure 5 Enabling CTS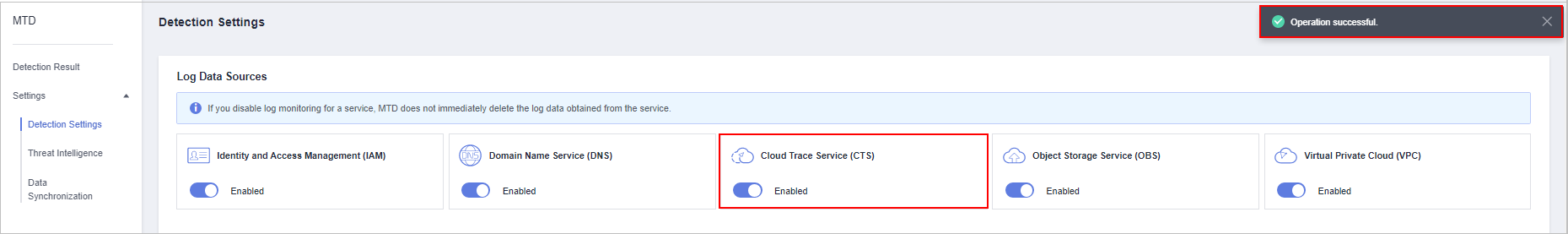
- In the navigation pane on the left, choose Detection Result. On the displayed page, "No threats have been found in the latest log data of IAM log, OBS log, DNS log, CTS log up to now" disappears. If CTS threat detection is enabled, the tracker is configured successfully.
Figure 6 Tracker configured
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot





